In today’s world, Enterprise Resource Planning (ERP) applications are being used by numerous companies worldwide. ERP is a type of application that makes it extremely easy for organizations to manage key parts of their business such as manufacturing, HR, sales, accounting and marketing.
Using the latest technologies like Artificial Intelligence (AI) and machine learning, ERP significantly improves efficiency and visibility across every aspect of your business, making it an indispensable asset for organizations around the globe.
No matter which vertical or industry your organization belongs to, ERP can prove to be immensely helpful when it comes to the smooth facilitation of everyday operations. However, it can also expose your company to severe cyber risks if proper security measures are not taken.
Kratikal’s VAPT team has tested and analyzed ERP for several companies, detecting a wide range of vulnerabilities that had the potential of posing huge security risks. So, here is a list of the top 10 critical vulnerabilities they found in ERP applications.
Table of Contents
- 1 Get in!
- 1.1 #1 Vulnerability to Stored Cross-Site Scripting
- 1.2 #2 Weak Password Policy
- 1.3 #3 Weak Lockout Mechanism
- 1.4 #4 Users Could Access Admin’s Configuration Dashboard
- 1.5 #5 Vulnerability to Session Fixation
- 1.6 #6 Unsuccessful Removal of Exif Info
- 1.7 #7 Lack of Rate Limit on ‘Add New Format’ Function
- 1.8 #8 Vulnerability to Time-based Blind SQL Injection
- 1.9 #9 Vulnerability to Reverse Tabnabbing
- 1.10 #10 Unrestricted File Upload
Get in!
Join our weekly newsletter and stay updated
#1 Vulnerability to Stored Cross-Site Scripting
Many of the ERP applications are vulnerable to stored cross-site scripting (stored XSS) attacks. Stored XSS takes place when an ERP application accumulates input from a potentially malicious user and stores this input in a data store to use later. Since this stored input is not properly filtered, the malicious data appears to be part of the application and is executed within a user’s browser under the ERP’s privileges.
How Can This Vulnerability Affect You?
With stored XSS, malicious actors can execute scripts in a user’s browser to deface websites, hijack user sessions, insert hostile content, hijack the victim’s browser via malware, redirect users, etc.
#2 Weak Password Policy
Password policies refer to the guidelines enforced related to the creation of an ERP application’s user password. A weak password policy can decrease the resistance of an ERP application against password guessing and brute force attacks that use password dictionaries to crack the passwords created by the admins and users.
How Can This Vulnerability Affect You?
Weak password policies allow the users to create very weak passwords, which can be easily guessed or bypassed by malicious actors. Weak passwords make an ERP application vulnerable to dictionary, brute force, or rainbow table attacks. Once a user’s password has been cracked, an attacker can have unrestricted access to that user’s account.

#3 Weak Lockout Mechanism
Account lockout mechanisms are quite useful in eliminating the risk of password guessing and brute force attacks. Through lockout mechanisms, users are usually locked out of their accounts after 3-5 unsuccessful login attempts. Once locked, the users can only unlock their accounts after a specific period of time, either via a self-service unlock mechanism or when an administrator intervenes.
How Can This Vulnerability Affect You?
If an ERP application’s lockout mechanism is weak, it may fall victim to brute force attacks. Once an application suffers a successful brute force attack, malicious actors can gain access to admin panels and confidential information. These attacks also enable attackers to launch further attacks on the application.
#4 Users Could Access Admin’s Configuration Dashboard
Referred to as privilege elevation or vertical privilege escalation, this access control vulnerability allows malicious actors to gain higher privileges, typically the ERP application’s admin privileges. It enables a user to access the upper privileged resources meant only for higher-level users like admins by simply using the resource’s URL. This vulnerability arises when an ERP application uses user-supplied input for accessing objects directly.
How Can This Vulnerability Affect You?
This access control vulnerability provides users with unauthorized modification rights that can result in some serious security risks for the ERP application’s users. It allows any user to easily access higher privileged information without authorization, which can lead to serious data leaks and breaches.
#5 Vulnerability to Session Fixation
Many ERP applications are vulnerable to session fixation attacks, which allow malicious actors to hijack a valid user session. If an ERP application fails to renew its session cookies after successful user authentication, malicious actors can force a user to utilize a cookie known to them to hijack a valid user session. Session fixation attacks fix an established session on the targeted user’s browser, beginning the attack before the victim logs in.
How Can This Vulnerability Affect You?
A successful session fixation attack on an ERP application can have grave consequences. It provides malicious actors with access to the victim’s account. This can lead to the attackers gaining access to higher-level privileges or stealing sensitive data.
#6 Unsuccessful Removal of Exif Info
When a user uploads an image in an ERP application, the EXIF Geolocation data of the uploaded image does not get stripped successfully. Consequently, malicious actors can gain access to the user’s sensitive information such as their geolocation or their device information like device version, name, software version, software & amp, etc.
How Can This Vulnerability Affect You?
ERP applications with this vulnerability violate a user’s privacy and provide attackers with sensitive information belonging to the users who upload an image to the application.
#7 Lack of Rate Limit on ‘Add New Format’ Function
Many ERP applications allow the users to exceed their rate limit on one or more of its functions like the ‘Add New Format’ function. Consequently, each time a function is used by users, they may gain some benefit that must be accounted for to properly compensate the owner.
How Can This Vulnerability Affect You?
This vulnerability enables malicious actors to replay a function request multiple times. The lack of rate limit on a function can allow an attacker to flood the ERP application with spurious requests in the backend.
#8 Vulnerability to Time-based Blind SQL Injection
Several ERP applications are vulnerable to SQL injection attacks that involve the insertion of either a complete or a partial SQL query in the application via data input. Malicious actors can inject the application with an SQL segment containing a heavy query or a specific DBMS function that generates a time delay. This allows the attackers to extract some information from the application during the time it takes to get the server to respond. If the attackers integrate the time delay in a conditional statement, they gain the ability to retrieve information from the database and extract sensitive data
How Can This Vulnerability Affect You?
SQL injection can expose an ERP application to some severe security risks. It can adversely affect the integrity and confidentiality of data. It can also impact the authorization and authentication aspects of the ERP application.
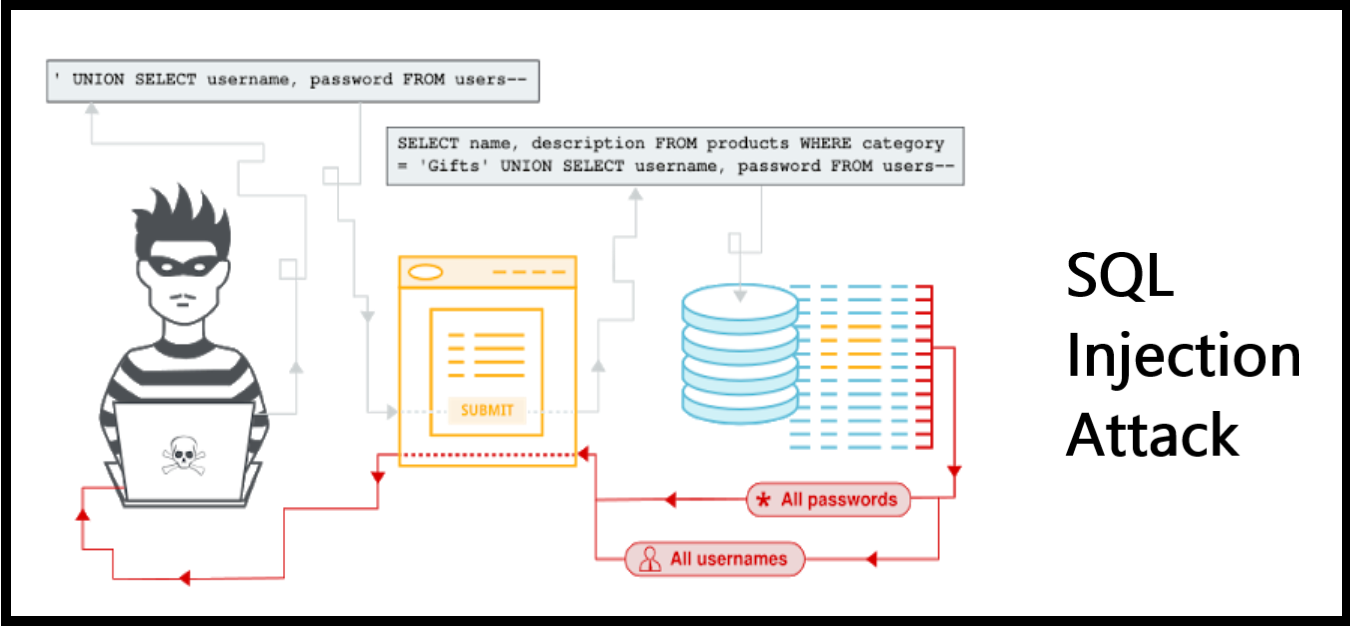
(Source: PortSwigger)
#9 Vulnerability to Reverse Tabnabbing
Many of the ERP applications are left vulnerable to reverse tabnabbing attacks, which allow attackers to redirect users from the application to a malicious site without their knowledge. Open windows consisting of normal hrefs with the tag target=”_blank” are capable of modifying window.opener.location, replacing the parent webpage with another site. If the links do not have rel=”noopener noreferrer” attribute, an attacker can use window.opener.location.assign to change the URL of the source tab, tricking the users into believing that they are still on a trusted page.
How Can This Vulnerability Affect You?
Even though this vulnerability does not permit script execution, it can prove to be quite helpful to malicious actors seeking to launch phishing attacks on the users of the ERP applications. They can exploit this vulnerability to replace the parent tab and trick the users into entering their sensitive data on a malicious website.
#10 Unrestricted File Upload
The business processes of numerous ERP applications allow users to upload data, files or information. The unrestricted file upload can cause numerous security risks as it allows an attacker to encapsulate malicious code into an applicable file type.
How Can This Vulnerability Affect You?
This vulnerability allows an attacker to upload an EICAR file instead of a .jpg or .png file. This can lead to drive-by-download attacks. It can also allow malicious actors to deface the website or obtain access to the ERP application’s file system through a web shell. Once malicious actors can remotely access the server, they can compromise the integrity of data, exfiltrate sensitive files and cause a denial of service.
These are the top 10 critical vulnerabilities usually found in ERP applications. And this is not it! There are several other flaws in ERP applications that can lead to the downfall of your organization’s defenses.
So, stay a step ahead of attackers and fix all the vulnerabilities before they have a chance to exploit them.
How?
Conduct periodic VAPT to identify the flaws in your ERP application and fix the detected vulnerabilities on priority.
After all, isn’t prevention always better than cure?
WAIT!
It’s not over yet…
Here’s a chance to become a BUG BUSTER!
Leave the best recommendations for one or more of these vulnerabilities in the comments section below and win your BUG BUSTER certificate!









Leave a comment
Your email address will not be published. Required fields are marked *