Making sure our internet systems and data are secure has become crucial in today’s digital world, as technology is ingrained in every part of our lives. Organizations of all sizes are frequently vulnerable to a variety of cyber dangers. A thorough strategy that incorporates Vulnerability Assessment and Penetration Testing (VAPT) is essential for reducing these threats. Businesses now face ongoing challenges from hackers who try to take advantage of weak points in their systems. In this blog, we’ll talk about the importance of VAPT and how it helps businesses improve their security posture.
Table of Contents
Get in!
Join our weekly newsletter and stay updated
What is VAPT?
A methodical method of assessing the security of computer systems, networks, and applications is called vulnerability assessment and penetration testing (VAPT). It entails the discovery, evaluation, and correction of flaws and vulnerabilities that could be taken advantage of by bad actors. A system, network, or application’s vulnerabilities are found using the VAPT method, which tests the vulnerabilities to see if they can be exploited. Penetration testing and vulnerability assessment are the two processes in the process.
Let’s Understand these Two Terms to have a Better Understanding
Vulnerability Assessment – System, network, and application vulnerabilities are scanned for using automated tools and techniques in vulnerability assessments. In order to find vulnerabilities that might be exploited, these tools look at various elements, including software, configurations, and system settings. The evaluation offers a thorough report on vulnerabilities found, enabling organizations to properly prioritize and remediate them.
Penetration Testing – The practice of ethical hacking, or penetration testing, goes beyond identifying vulnerabilities by simulating actual attack situations. In order to gain unauthorized access, harvest sensitive data, or impair system operation, skilled security professionals try to exploit discovered vulnerabilities. The objective is to assess the efficiency of currently in-place security mechanisms, identify potential access holes, and suggest actions to increase security.
Get in!
Join our weekly newsletter and stay updated
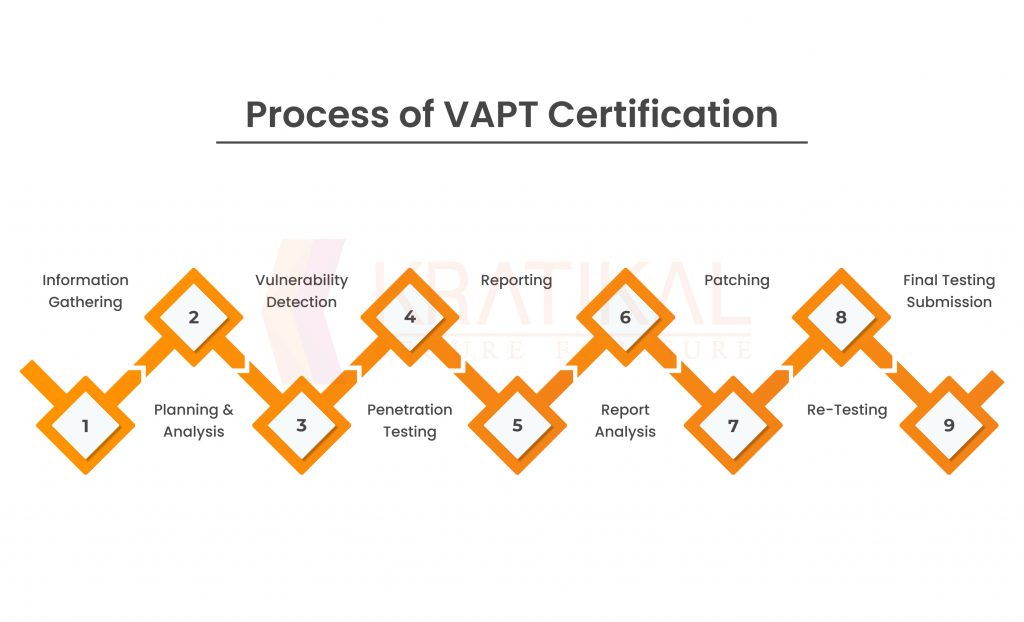
Process of VAPT Certification –
The organization can become certified with the help of the detailed VAPT Certification step-by-step guidance provided below.
- Information Gathering
- Planning & Analysis
- Vulnerability Detection
- Penetration Testing
- Reporting
- Report Analysis
- Patching
- Re-Testing
- Final Testing submission
Benefits Associated with VAPT –
There are numerous benefits which are associated with VAPT. We will discuss in detail the benefits.
- Identify Vulnerabilities: VAPT helps organizations proactively identify vulnerabilities and weaknesses in their systems before malicious actors can exploit them. By uncovering these vulnerabilities, organizations can take preventive measures to mitigate the risks, reducing the likelihood of successful cyber attacks.
- Strengthen Security Controls: Organizations learn more about the efficiency of their current security mechanisms through VAPT. The outcomes of penetration testing and vulnerability assessments point out areas where security controls can be strengthened, enabling organizations to improve their overall security posture.
- Compliance and Regulatory Requirements: Organizations must perform routine security assessments, including VAPT, as required by many regulatory frameworks and industries in order to maintain compliance. Organizations can meet these standards and show their dedication to protecting sensitive data by completing VAPT.
- Minimize Downtime and Financial Loss: A successful downtime, monetary loss, reputational harm, and a decline in client trust can all result from a successful cyber attack. By locating weaknesses and taking proactive measures to repair them, VAPT assists organizations in preventing such incidents by lowering the risk of successful attacks and the resulting consequences.
- Continual Security Improvement: VAPT should not be a one-time activity; it should be integrated into an organization’s security practices as an ongoing process. Regular assessments and tests allow organizations to stay ahead of emerging threats, adapt to evolving technologies, and continually improve their security measures.
- Proactive Security Approach: Regular VAPT enables organizations to adopt a proactive security approach by identifying vulnerabilities before they are exploited. It allows businesses to address these issues promptly and effectively, reducing the risk of successful cyber attacks.
How Kratikal Helps you with VAPT?
Organizations must take proactive efforts to protect their digital assets at a time when cyber threats are growing more sophisticated. Before they are used by attackers, possible vulnerabilities can be found and fixed via vulnerability assessment and penetration testing (VAPT). Businesses can improve their cybersecurity posture, safeguard sensitive data, adhere to industry standards, and reduce the chance of successful cyberattacks by implementing a comprehensive VAPT approach. Setting VAPT as a top priority as part of your overall cybersecurity plan is an essential first step in guaranteeing your company’s long-term profitability and resilience in the digital sphere.
Kratikal, a CERT-In empanelled organization helps in providing VAPT services. There is a comprehensive list of VAPT services to help the organization safeguard its security postures, for instance, web application security testing, network penetration testing, cloud penetration testing, secure code review, IoT security testing, and medical device security testing.
By using VAPT services, your business can improve cybersecurity defenses, proactively detect and resolve potential vulnerabilities, and reduce the likelihood that cyberattacks will be successful. Kratikal customizes its VAPT services to match your unique needs, offering a thorough and unique approach to protecting your digital assets. By strengthening your defenses with Kratikal’s VAPT services one can avoid data breaches, meet security standards, improve cyber resilience, identify security loopholes, and protect organizational data.









Leave a comment
Your email address will not be published. Required fields are marked *