The Open Worldwide Application Security Project (OWASP) has just unveiled its Top 10 Non-Human Identities (NHI) Risks for 2025. While OWASP has long provided resources on application and API security, none have specifically addressed the unique challenges associated with NHIs. This new document bridges that gap, highlighting critical yet often overlooked risks that pose significant threats to organizational security.
This release marks a pivotal moment in cybersecurity, as one of the most trusted security communities formally acknowledges Non-Human Identities (NHIs) as a major enterprise concern. With an increasing number of breaches linked to NHI credential leaks and misuse, this publication comes at a crucial time.
Before diving into the top 10 NHI risks, let’s first examine the key trends that led to this development.
Table of Contents
- 0.1 Non-Human Identities Present an Expanding Attack Vector
- 0.2 A Closer Look At OWASP Top 10 NHI Risks
- 1 Get in!
- 2 Book Your Free Cybersecurity Consultation Today!
Non-Human Identities Present an Expanding Attack Vector
OWASP Non-human identities (NHIs), also known as machine or workload identities, operate within systems by interacting primarily with other non-human entities. For a deeper dive into their definition and implications, check out our article on NHI governance challenges.
Over the past decade, the rapid expansion of NHIs in enterprises has been fueled by cloud computing, increased API-driven third-party integrations, and the rise of machine learning models and agents. Traditional Identity and Access Management (IAM) tools have been designed with human users in mind, leaving many organizations struggling to enforce best practices for NHIs—such as least privilege access, credential management, and auditing.
A key challenge in securing NHIs is the lack of clear ownership. When developers introduce a new service, are they responsible for managing it in production? Who handles its decommissioning? Should NHIs fall under the purview of the IAM team, IT, or Security? This uncertainty spans departments and teams, leading to gaps in governance. With shadow IT accounting for over 50% of total enterprise tech spend, as estimated by Gartner, organizations must rethink how they manage NHIs. The OWASP Top 10 NHI Risks for 2025 provides much-needed clarity, outlining critical steps organizations must take to secure these identities now.
A Closer Look At OWASP Top 10 NHI Risks
Let’s have a look at the risks below in detail:
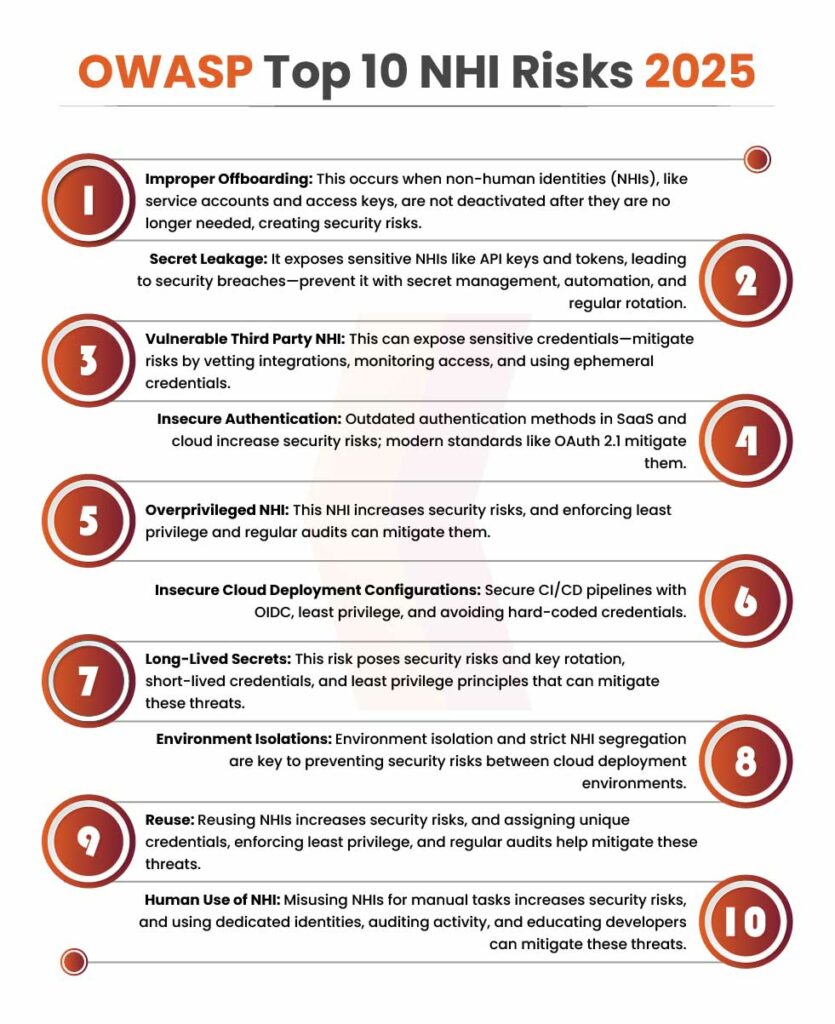
NHI1: Improper Offboarding
Improper offboarding refers to the failure to deactivate or remove non-human identities (NHIs), such as service accounts and access keys when they are no longer needed. This can occur when applications are decommissioned, services are taken offline, or when employees leave an organization. Leaving NHIs unmonitored or orphaned poses significant security risks, including unauthorized access to sensitive systems and data.
Prevention Measures
- Establish an offboarding process that thoroughly reviews all non-human identities (NHIs) linked to a departing employee. For each NHI, assess its necessity—decommission those that are no longer needed, and transfer ownership of the required ones to another employee while rotating any credentials the departing employee had access to.
- Wherever possible, automate offboarding tasks by integrating HR systems with identity and access management (IAM) tools.
- Conduct regular audits of active NHIs to detect any ongoing human usage and prevent potential misuse.
NHI 2: Secret Leakage
Secret leakage occurs when sensitive non-human identities (NHIs) like API keys, tokens, encryption keys, and certificates are exposed during the software development lifecycle. Leaked secrets can be hard-coded in source code, stored in plain text files, or shared through unsecured channels, making them vulnerable to exploitation. This can lead to unauthorized access, data theft, privilege escalation, and significant security breaches. Examples include the leakage of an Azure SAS token in a public repository or an admin API key stored in an employee’s public file share.
Prevention Measures
- Use Ephemeral Credentials Where Possible
- Use Secret Management Tools
- Automate Secret Detection
- Restrict Secret Scope and Permissions
- Rotate Secrets Regularly
NHI 3: Vulnerable Third Party NHI
Third-party non-human identities (NHIs) are commonly used in development workflows, especially through integrated development environments (IDEs) and third-party SaaS tools. These tools often require access to sensitive credentials like API keys, tokens, and SSH keys to interact with services such as code repositories and cloud environments. If a third-party extension or service is compromised, attackers can exploit these credentials, leading to unauthorized access, data breaches, or service disruptions. Examples include IDE integrations with code repositories, extensions accessing cloud resources, and third-party service providers handling sensitive data.
Preventive Measures
- Vet and Limit Third-Party Integrations
- Monitor and Detect Third-Party Behavior
- Use Ephemeral and Rotating Credentials
NHI 4: Insecure Authentication
Using insecure or outdated authentication methods in SaaS applications and cloud environments can expose organizations to unauthorized access, data breaches, and compliance violations. Developers must choose authentication mechanisms carefully, prioritizing industry standards like OAuth 2.1 and OpenID Connect (OIDC). Risks include deprecated OAuth flows, non-standard implementations, reliance on static credentials over secure, credential-less methods, app passwords that bypass MFA, and legacy authentication protocols using usernames and passwords. Adopting modern authentication practices reduces exposure to security threats and enhances overall system protection.
Preventive Measures
- Adopt Modern Authentication Standards
- Leverage Credential-less methods
- Standardize OAuth Implementations
- Conduct Regular Security Audits
NHI 5: Overprivileged NHI
OWASP Non-human identities (NHIs), such as service accounts and API tokens, provide automated access to cloud resources but can become security risks if assigned excessive privileges. Over-privileged NHIs expand the blast radius in case of a compromise, allowing attackers to access sensitive data, escalate privileges, move laterally within networks, install malware, or even take over entire cloud accounts. Example attack scenarios include overprivileged web server users, misconfigured VM permissions, excessive OAuth application privileges, and database service accounts with administrative access. Properly restricting NHIs to the least privileges necessary is essential for reducing security risks.
Preventive Measures
- Enforce the principle of least privilege
- Regularly audit and review permissions
- Establish preventive guardrails
- Leverage Just-in-Time (JIT) access
NHI 6: Insecure Cloud Deployment Configurations
CI/CD applications streamline code deployment but require secure authentication with cloud services. Using static credentials in pipelines is risky, as they can be exposed through repositories or logs, granting attackers persistent access. OIDC provides a more secure alternative with short-lived tokens, but misconfigurations—such as improperly validated identity claims—can still lead to unauthorized access. Proper security measures, including enforcing the least privilege, managing credentials effectively, and restricting OIDC tokens, are crucial. Common attack scenarios include misconfigured AWS OIDC trust relationships and exposed Azure Service Principal credentials, both of which can lead to cloud resource compromises.
Preventive Measures
- Use OICD for Secure Authentication
- Enforce Least Privilege
- Avoid Hard-Coded Credentials
Get in!
Join our weekly newsletter and stay updated
NHI 7: Long-Lived Secrets
Long-lived secrets, such as API keys, tokens, encryption keys, and certificates with extended or no expiration, pose a security risk as they can be exploited if breached. Developers use these secrets for authentication and service interactions, but if leaked, they grant attackers prolonged access to sensitive resources. Attack scenarios include privilege escalation through stale access tokens and session hijacking via stolen long-lived cookies.
Preventive Measures
- Enable Automated Key Rotation
- Implement Short Lived Credentials
- Adopt Zero Trust Principles
- Enforce the Principle of Least Privilege
NHI 8: Environment Isolation
Environment isolation is a crucial security practice in cloud application deployment, ensuring that development, testing, staging, and production environments remain separate to prevent issues from affecting production systems. OWASP Non-human identities (NHIs), such as service accounts and API keys, play a key role in deployment but can introduce security risks if shared across environments. Reusing NHIs between testing and production can allow attackers to exploit compromised testing environments to access sensitive production data. To mitigate this risk, organizations should enforce strict isolation of NHIs by using separate credentials for each environment. Applying the principle of least privilege, implementing environment-specific access controls, and conducting regular audits.
Preventive Measures
- Strict Environmental Isolation for NHIs
- Apply the Principle of Least Privilege
- Enforce Environment Specific Access Controls
- Segregate Infrastructure for Sensitive Resources
NHI 9: NHI Reuse
Reusing OWASP Non-Human Identities (NHIs) like service accounts, API keys, and cloud credentials across multiple applications or services increases security risks by enabling attackers to move laterally if one credential is compromised. This complicates breach mitigation and audit processes. To enhance security, organizations should assign unique NHIs per application or service, following the principle of least privilege. Isolating NHIs helps contain breaches and prevent unauthorized access to critical resources, reducing the risk of widespread attacks.
Preventive Measures
- Assign unique NHIs to each Application or Service
- Assign unique NHIs in each environment
- Enforce the Principle of Least Privilege
- Audit and Review the use of NHis
NHI 10: Human Use of NHI
Misusing non-human identities (NHIs), such as service accounts and API tokens, for manual tasks introduces significant security risks. Originally designed for automated access to cloud resources, NHIs should not be used by developers or administrators for convenience, as this can lead to excessive privileges, reduced auditability, and difficulty distinguishing human activity from automation—making it easier for attackers to exploit. Examples include administrators using service accounts for console logins, developers executing commands with NHIs, and teams sharing API tokens, all of which weaken security controls and accountability.
Preventive Measures
- Use Dedicated Identities
- Audit and Monitor NHI Activity
- Use Context-Aware Access Controls
- Educate Developers
A New Start of NHI Security
OWASP’s Top 10 projects are widely recognized for providing actionable security frameworks. The new NHI-focused Top 10 aims to help enterprises identify and mitigate risks associated with non-human identities, a growing and often overlooked attack surface. This release marks a significant shift in enterprise security, emphasizing NHIs in IAM strategies. As automation and machine-to-machine communication expand, this framework offers clear guidance to address emerging threats, ensuring a more secure digital ecosystem.
Book Your Free Cybersecurity Consultation Today!
Conclusion
OWASP’s Top 10 Non-Human Identity Risks for 2025 provides a framework for organizations to address the often-overlooked security challenges associated with machine and workload identities. As automation and interconnected systems become increasingly prevalent, NHIs represent a significant and expanding attack surface. By understanding and mitigating the risks outlined in this document, from improper offboarding and secret leakage to overprivileged access and insecure configurations, organizations can significantly improve their overall security posture. This framework serves as a timely call to action, urging businesses to prioritize NHI security and implement the recommended best practices to protect against evolving threats in today’s complex digital landscape.
FAQs
- How does OWASP NHI Top 10 pose a security risk to organizations?
NHIs can be exploited by attackers if not properly managed. Risks include:
Credential leaks
Improper offboarding
Overprivileged access
Third-party vulnerabilities
Insecure authentication - What are some common attack scenarios involving NHIs?
Some examples of security breaches include:
Orphaned NHIs being exploited for unauthorized access
Leaked API keys in public repositories leading to data breaches
Overprivileged NHI allows lateral movement within cloud environments
Compromised third-party integrations exposing sensitive credentials









Leave a comment
Your email address will not be published. Required fields are marked *