The advancement of technology leaves no scope for negligence when it comes to data protection. Organizations, understanding the urgency of the matter, implement sturdy cybersecurity practices in place, but can the appropriate amount of resources dedicated towards the security program provide complete assurance?
Have you ever wondered which information assets and systems hold the probability of being the most vulnerable? And has it ever sprung to your mind to calculate the potential financial costs you would encounter if the systems went down? In this highly uncertain cyber risk environment, these questions are critical for all organizations to answer.
Table of Contents
What is Risk Assessment?
Risk assessment identifies the cyber threats intimidating a business’s IT infrastructure, as well as assesses the likely consequences that might arise in the events of a data breach. It assists organizations to examine and control incidents harming their sensitive data by detecting exploitable vulnerabilities that a cybercriminal could take advantage of or the system errors made by their employees.
The assessment should be conducted on a regular basis, or whenever a major change occurs in the organization, such as when new technology is implemented or when the working environment is shifted from working from office to remote work.
Some IT security frameworks, like ISO 27001, require the conduction of regular risk assessments in order to certify an organization, making risk assessment a crucial part of a successful security program. Not only does risk assessment safeguard the organization from data breaches, it also imparts information of an enterprise’s constantly changing risks and vulnerabilities so appropriate measures can be installed as a response to security threats.
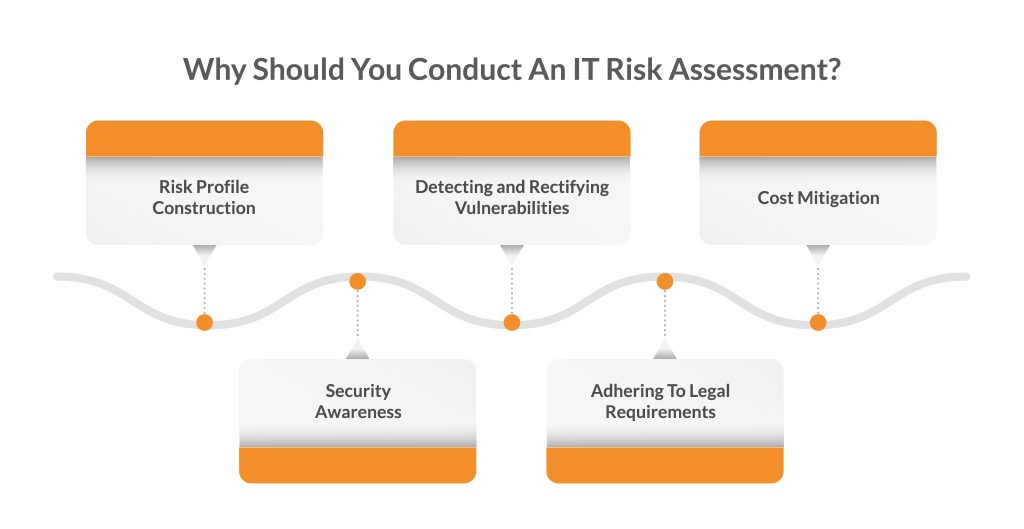
Why Should You Conduct An IT Risk Assessment?
To some businesses, the thought of dedicating a whole team of people to establish security plans may seem fruitless, but risk assessment is something which cannot be disregarded. It serves many significant purposes, including –
- Risk Profile Construction
Identification of risks and ranking them in order of their threat level is essential to allocate resources for them appropriately. A risk profile features the characteristics of probable risks in details, like:
- Source of the potential threat (External or Internal)
- Reason for that threat
- Probability of threat occurring
- Impact of the threat
This can allow organizations to attend to the high-impact, high-probability risks first, and then work their way down to the less impactful and less damaging threats in case of a security emergency.
- Detecting and Rectifying Vulnerabilities
A gap-focused approach can be of service when it comes to identifying and mitigating the exposable vulnerabilities in an organization’s IT ecosystem. Security testing like Vulnerability Assessment and Penetration Testing (VAPT) utilizes the perspective of a potential attacker to ensure the thorough testing of security controls and protocols.
The comparison of risk profile to the performance of an IT infrastructure during such assessments can help determine the finest methods that can be implemented to improve a business’s IT security.
- Cost Mitigation
With regular risk assessments, an organization can eliminate the unnecessary spending on security. Accurate risk estimation enables the balance of costs against benefits, that is, through risk assessment one can easily identify the more catastrophic risks and employ the security resources towards them, instead of wasting them on the less damaging ones.
- Security Awareness
Periodic risk assessment creates better awareness among the organization’s stakeholders and employees of all the vulnerable information assets and processes present in their IT environment so they can correctly prioritize them in case of a data breach.
- Adhering To Legal Requirements
To conduct their business across the globe, organizations have to comply with the privacy and data security requirements of various countries. The companies doing business with the European countries have to comply with GDPR, healthcare organizations have to comply with HIPAA, payment industry have to adhere to PCI DSS regulations, and many more.
Risk Assessment Methodology
Firstly, the legal, regulatory and contractual obligations, the objectives concerning information security, and the requirements and expectations of the stakeholders are anticipated. Once this is done, the risk criteria is set. This established process of risk assessment often considers both the potential of existing threats and likelihood of them occurring.
Afterwards, a risk acceptance criteria is also defined, in which the organization is required to determine the amount of residual risk that can be overlooked since all the risks cannot be eliminated.
Evaluation
When the list of Information Assets is created, the risk associated with them is determined. Some risks may be more severe than others, so analyzing their level of intensity filters the threats that essentially need to be addressed. This is where the Risk Criteria is set in motion.
Building a Risk Criteria provides a guide to compare risks by giving them a score with respect to their likelihood of occurring and the damage caused by them. The security risks threatening an organization can be assessed in a consistent and comparable manner by evaluating the risks through this criteria.
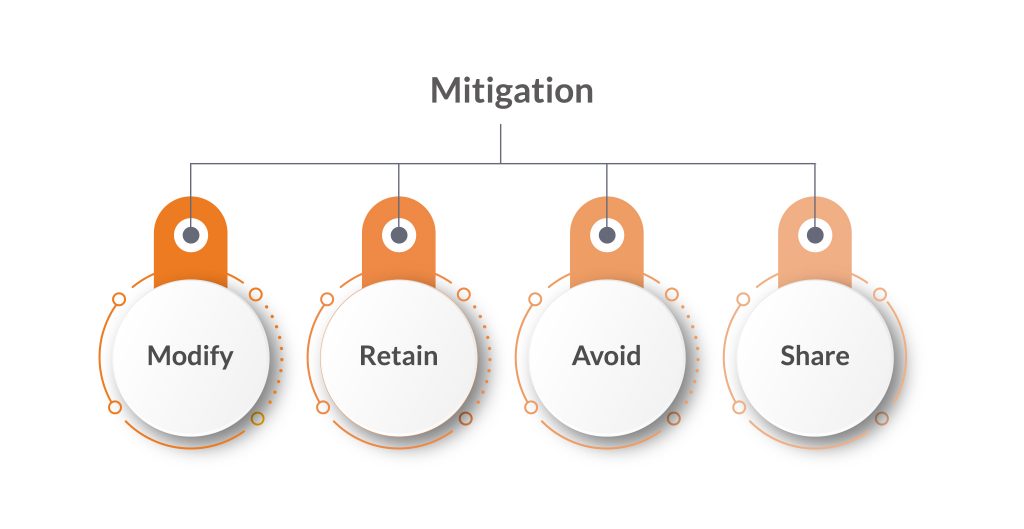
Mitigation
The four ways in which the risks can be mitigated –
- Modify – Modify the risk by implementing security measures to lower the instance of risk occurrence or the damage caused by the threats.
- Retain – Retain the risk within previously established risk acceptance criteria.
- Avoid – Avoid the risk by altering the circumstances causing it.
- Share – Share the risk with an external associate who is capable of managing the risk, like an insurance company or other party.
Risks are categorized based on their impact on the business processes of an organization. To maintain the operational resilience and continuity of operations during or after a business is disrupted due to a security incident, Business Impact Analysis (BIA) can be used to assess the criticality of business activities and their resource requirements. Also, a Business Continuity Plan (BCP) efficiently aids a business recovering after a data breach.
Assess Your Organization’s Risks With Kratikal
While developing your company’s IT security management plan, it is critical to determine fool-proof methodologies when assessing risk. The knowledge of risks associated with your business, and their impact, will allow you to mitigate the impact in case a security emergency occurs.
As a CERT-In empanelled organization, Kratikal can assist you to become better informed about these risks with the help of our VAPT services, both manual and automated, which identify, detect and analyze the vulnerabilities present in your IT framework.
We also offer security auditing for Compliance, such as ISO/IEC 27001, GDPR, PCI DSS, and many others, to help your organization comply with the laws and regulations set by various governments.
Risk Assessment outlines all the present vulnerabilities and risks accompanying the assets and security processes of your organization to prevent a data breach in the future.
Can you think of other benefits provided by risk assessment? Comment down below to share your thoughts!









Leave a comment
Your email address will not be published. Required fields are marked *