Security misconfiguration is a significant concern, in the OWASP Top 10. During our web application penetration tests, we often discover numerous vulnerabilities of this nature. According to OWASP, this issue impacts nearly 90% of all web applications. In this blog, we will explore this vulnerability through the lens of the OWASP Top 10, illustrating it with real-world attack scenarios. We also outline the key best practices and preventive measures to safeguard against such threats.
Table of Contents
What is OWASP Security Misconfiguration?
Security misconfigurations occur when errors or oversights are made during the configuration, implementation, or maintenance of an API, creating exploitable security vulnerabilities. These issues typically arise when developers or IT teams fail to follow established security best practices while setting up or managing APIs.
In essence, it means that critical API security settings were either left out or incorrectly applied, resulting in risky gaps that attackers can exploit to launch large-scale attacks and cause data breaches.
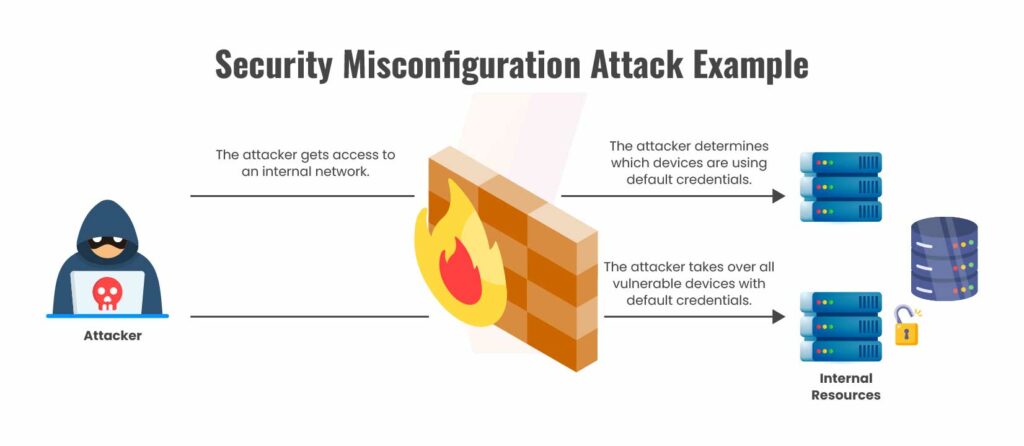
Such misconfigurations can occur at multiple layers of the API stack — including the API server, API gateway, client application, supporting infrastructure, network, system, and application levels. Their impact on APIs is virtually identical to how similar misconfigurations affect web applications.
Cyber Security Incident: AWS S3 Misconfiguration Leads to Exposure of Company and Customer Data
A poorly secured Amazon AWS S3 bucket led to a significant data leak for the Australian Broadcasting Corporation, exposing customers’ password hashes, emails, logins, videos, and licensed content requests. The incident occurred just a week after AWS released official guidance on securing S3 buckets. This case highlights how even a short delay in addressing security vulnerabilities can cause severe damage and major headaches for both businesses and their customers.
Common Attack Vectors in OWASP Security Misconfiguration
Security misconfigurations in mobile applications can be leveraged by attackers through multiple avenues, such as:
- Insecure default settings: Many mobile apps ship with default configurations that include weak security settings or unnecessary permissions, leaving them open to exploitation.
- Improper access controls: Misconfigured permissions can enable unauthorized users to access sensitive information or perform privileged actions.
- Weak encryption or hashing: Using outdated, poorly implemented, or weak encryption and hashing algorithms can allow attackers to compromise sensitive data.
- Lack of secure communication: Failing to implement secure protocols like SSL/TLS can expose data to interception via eavesdropping or man-in-the-middle attacks.
- Unprotected storage: Storing sensitive data—such as passwords or API keys—in plain text or with inadequate encryption increases the risk of unauthorized access.
- Insecure file permissions: Application files with world-readable or world-writable permissions can be easily tampered with or accessed by malicious actors.
- Misconfigured session management: Poor session handling practices can lead to session hijacking, enabling attackers to impersonate legitimate users.
Book Your Free Cybersecurity Consultation Today!
Attack Scenerios of OWASP Security Misconfiguration
The following examples highlight common security misconfigurations found in mobile applications:
Scenerio 1:
A mobile app is launched with default configurations that include weak security measures, such as using insecure communication protocols, keeping default usernames and passwords, and failing to disable debugging features in production builds. Attackers exploit these weaknesses to gain unauthorized access to sensitive data or execute malicious activities.
Scenerio 2:
A mobile app exposes its root directory through an exported file content provider, enabling other applications to access its resources without restriction.
Scenerio 3:
A mobile app stores application shared preferences with world-readable permissions, allowing other applications to access and read sensitive information.
Scenerio 4:
A mobile app makes an internal-use-only activity accessible to external sources, increasing the attack surface and opening the door for potential exploits.
Scenerio 5:
A mobile app requests more permissions than required for its core functions. For example, a basic flashlight app asking for access to a user’s contacts, location, and camera. Such excessive permissions expose sensitive user data to unnecessary risks, whether through intentional misuse or accidental leaks.
Why Does Secruity Miconfiguration Rank in OWASP Top 10 API Vulnerabilities?
Security misconfiguration is one of the most prevalent and risky API security issues, which is why it holds a place in the OWASP Top 10. Missteps in configuration, deployment, or maintenance can create exploitable gaps, leaving APIs vulnerable to attacks. Below are the key reasons it ranks so high.
Severe Consequences
One of the most significant impacts of security misconfigurations is the exposure of sensitive information and critical system details. Such exposure can lead to a complete server compromise, causing potentially devastating damage to the organization.
Security misconfiguration ranks among the OWASP API Top 10 vulnerabilities because it opens the door to a wide variety of attacks, including remote exploits, directory traversal, SSRF, authentication and authorization bypasses, and even cloud-based intrusions.
Another reason it holds this ranking is that misconfigured APIs can create a false sense of security for developers and the organization. Teams may assume their systems are well-protected simply because configurations exist, without realizing that incorrect or incomplete configurations can be even more risky than having none at all. In such cases, attackers can exploit these weaknesses with ease.
High Prevalence and Easy Exploitation
Security misconfigurations carry both a prevalence score of 3 and an exploitability score of 3, making them among the most common API vulnerabilities and also some of the easiest to exploit. With readily available automated tools, attackers can quickly identify and take advantage of these weaknesses.
A major contributor to their high prevalence is the rapid pace of modern development cycles. Under tight deadlines, developers often lack the time to thoroughly test and verify configurations before deploying API functionality to production.
Additionally, the growing complexity of IT infrastructures has reduced visibility into the complete API ecosystem. As a result, it’s not unusual for API features, endpoints, or dependencies to be overlooked entirely.
Get in!
Join our weekly newsletter and stay updated
Prevention Measures for OWASP Security Misconfiguration
- A repeatable hardening process ensures that new environments can be deployed quickly and securely. Development, QA, and production environments should be configured identically, with each using unique credentials. Wherever possible, this process should be automated to reduce the effort needed for setting up a secure environment.
- Use a minimal platform setup, free from unnecessary features, components, documentation, or sample files. Remove or avoid installing unused frameworks and functionalities.
- Incorporate a regular review and update routine as part of patch management (see A06:2021 – Vulnerable and Outdated Components). This should include applying relevant security notes, updates, and patches, as well as reviewing permissions for cloud storage (e.g., AWS S3 buckets).
- Adopt a segmented application architecture to ensure secure separation between components or tenants through segmentation, containerization, or cloud security groups (ACLs).
- Enforce security controls on the client side, such as security headers.
- Finally, implement an automated verification process to regularly confirm the effectiveness of configurations and settings across all environments.
Conclusion
Security misconfiguration remains one of the most pervasive and easily exploitable vulnerabilities, making its place in the OWASP Top 10 well-deserved. From exposing sensitive data to enabling a wide range of complex attacks, the consequences can be severe and long-lasting. The fact that these vulnerabilities are both common and easily identifiable by attackers—often with automated tools—underscores the urgency of addressing them proactively.
By implementing a repeatable hardening process, minimizing unnecessary components, regularly reviewing configurations, segmenting application architectures, and automating verification, organizations can significantly reduce their risk. Security must be treated as a continuous process rather than a one-time task, ensuring that APIs and applications remain resilient against evolving threats.
FAQs
- What OWASP Top 10 risk involves misconfiguration security configurations on an application?
Security misconfiguration refers to inadequate security hardening across the application stack. This may involve misconfigured cloud service permissions, enabling or installing unnecessary features, or leaving default administrator accounts and passwords in place.
- Which vulnerabilities are part of OWASP?
In the risk equation, vulnerability contributes to the likelihood factor.
An exploit is a technique or method used by cybercriminals to take advantage of a security flaw in software or hardware, enabling them to gain unauthorized access, disrupt operations, or steal sensitive data. - What is an example of security misconfiguration?
Leaving default usernames and passwords unchanged is a frequent security oversight. Since these credentials (like “admin/admin”) are easy to guess, they’re often the first thing attackers try. Updating them right away is a simple yet essential step to protect your system and block unauthorized access.









Leave a comment
Your email address will not be published. Required fields are marked *