Operational Technology (OT) security encompasses a set of practices and procedures aimed at protecting cyber-physical systems and industrial control systems (ICS) from cyber threats and exploitation. ICS are essential OT components widely used across industries to automate and manage production processes.
As critical infrastructure increasingly adopts digital technologies to boost efficiency and innovation, it also becomes more vulnerable to cyber incidents that can disrupt essential services like electricity, water, and transportation.
The significance of ICS and OT security lies in the unique risks tied to operational technology. Disruptions or failures in OT systems can directly compromise the safety, availability, and reliability of critical industrial processes. Due to this high impact potential, cyber attackers increasingly view OT environments as valuable and strategic targets.
Table of Contents
Overview on OT Security Market
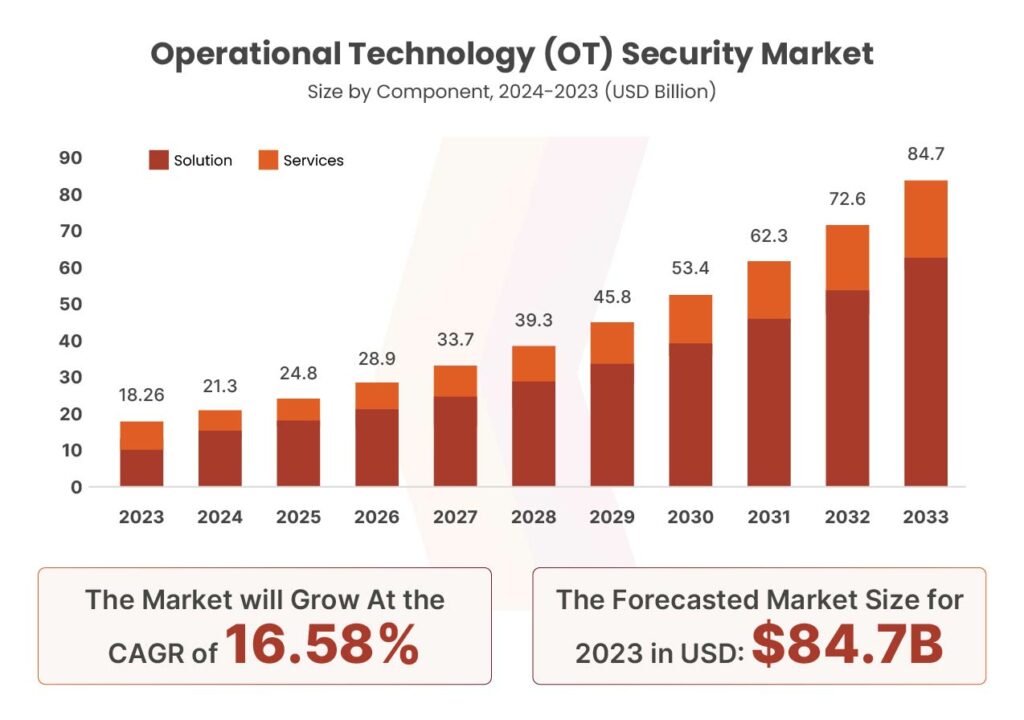
The global OT security market will grow from USD 18.26 billion in 2023 to USD 84.7 billion by 2033, with a strong CAGR of 16.58%. In 2023, North America led the market, accounting for over 39% of the global share and generating around USD 7.12 billion in revenue.
OT Cyber Security Highlights
A recent call has been made for structural reform in OT cybersecurity reporting, emphasizing that current models are outdated and reactive. As regulations like NIS2, TSA directives and sEC disclosure rules expand the scope of accountability, there’s a growing need for clearer authority and visibility at the leadership level. The recommendation includes establishing pre-defined reporting pathways conducting annual incident response exercises, and aligning OT risk with enterprise level impact models. This shift would ensure that cybersecurity in operational technology is not just IT’s responsibility but a critical, organization-wide priority focused on safety and business continuity.
The Purdue Model: A Framework for OT Network Architecture
Organizations that use operational technology commonly structure their technology architecture into five distinct layers, following the industry-standard Purdue Model. This model offers a clear framework for understanding the specific roles and functions of technologies at different levels within an organization.
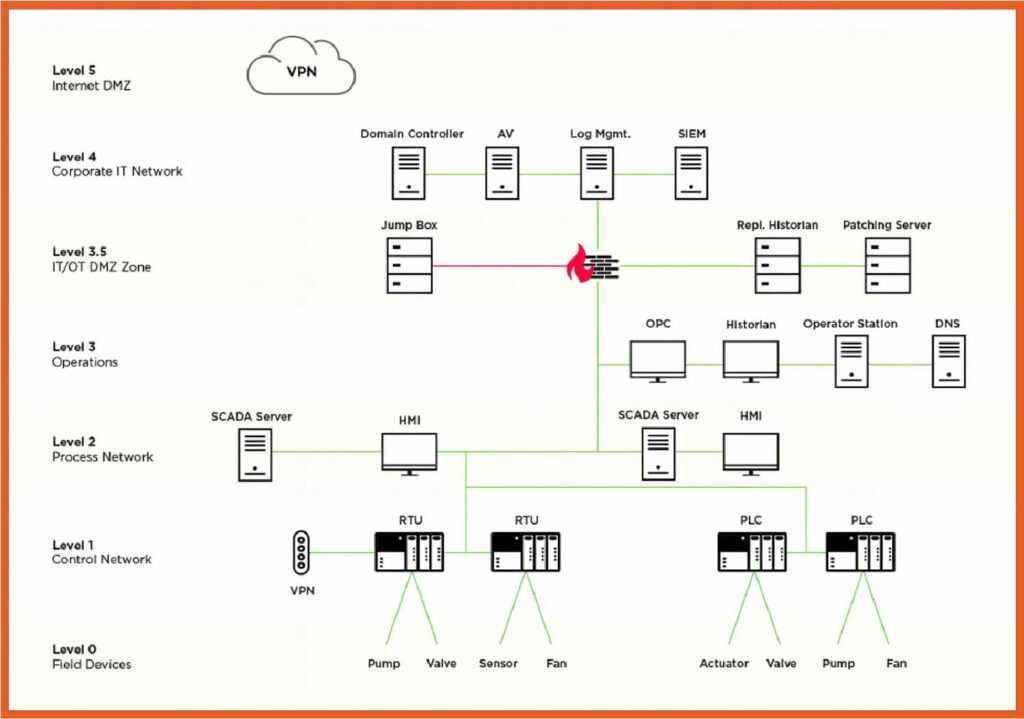
The Purdue Model has long served as a reliable framework for securing OT/IT environments, outlining best practices for managing the interaction between industrial control systems and IT networks. Structured into six levels, the model begins at Level 0, which includes physical sensors and actuators that transmit process data to PLCs, HMIs, and historian databases, and extends up to Level 5, representing enterprise IT networks.
However, despite its usefulness, the model isn’t without limitations. Experts often identify Level 3, which focuses on manufacturing operations control, as the point of greatest cybersecurity risk within the architecture.
Short Summary of an OT Cyberattack
The attacks have revealed that vulnerabilities can be found at every layer of the network architecture.
In September 2024, a cyberattack forced Arkansas City, Kansas, to shift its water treatment facility to manual operations. Local authorities, with support from Homeland Security and the FBI, are investigating the incident and have implemented enhanced security protocols.
Although the water supply remains safe, residents may experience reduced water pressure over the weekend as issues with several pumps are resolved. Notably, the attack came just two days after Water ISAC issued a warning about potential Russian-linked cyber threats targeting the water sector.
This event highlights the urgent need for:
- Comprehensive monitoring of OT assets
- Stronger cybersecurity protocols for water infrastructure
- Proactive threat intelligence sharing across the industry
Book Your Free Cybersecurity Consultation Today!
Challenges of OT Cybersecurity
ICS and OT assets were once isolated from enterprise networks and the internet. However, as organizations embrace digital transformation and the need for seamless integration between IT, cloud, and operational systems has grown—significantly increasing the exposure of ICS and OT environments to serious cyber threats.
Limited Visibility
Many OT assets are old and weren’t built to handle today’s cyber threats like DDoS attacks or known vulnerabilities. The bigger issue is that most organizations don’t have a clear, updated list of all their OT assets. Without this, it’s hard to find risks, spot internet exposure, or fix settings that could let attackers in.
Lack of Control
Poor segmentation in industrial networks allows attackers to move laterally across systems undetected, letting malicious traffic spread quickly. Remote access is common, often through cellular gateways or unmanaged software, which IT teams typically don’t oversee. Additionally, traditional IT security tools aren’t designed to understand the unique communication protocols used in ICS and OT systems, making it harder to spot potential threats.
Weak Collaboration
In many organizations, the CISO and IT teams are responsible for cybersecurity, but they often lack deep knowledge of operational and process control systems. Meanwhile, OT teams may hesitate to let IT into their networks, leading to a “keep out” mindset. This lack of trust and teamwork between IT and OT can seriously weaken the organization’s overall security.
Get in!
Join our weekly newsletter and stay updated
How Kratikal Can Help Organizations in OT Security?
Kratikal offers end-to-end OT security services designed to protect industrial control systems (ICS) and critical infrastructure from evolving cyber threats. By combining deep expertise in operational technology with advanced security assessment tools, Kratikal helps organizations identify vulnerabilities, segment networks, monitor threats in real time, and implement tailored mitigation strategies. From asset discovery and risk assessment to incident response and compliance support, Kratikal ensures comprehensive protection across all layers of the OT environment—enabling businesses to maintain operational continuity, meet regulatory standards, and secure their IT infrastructure against targeted attacks.
Conclusion
As operational technology continues to merge with IT systems and adopt digital innovations, the risk of cyber threats targeting critical infrastructure is growing rapidly. From water treatment plants to energy grids, the potential impact of an OT cyberattack can be severe—affecting safety, service availability, and public trust. Frameworks like the Purdue Model offer a structured approach to securing OT environments, but real-world incidents show that vulnerabilities still exist at every layer. To stay ahead of evolving threats, organizations must prioritize OT security through continuous monitoring, better visibility, cross-team collaboration, and proactive threat management. With Kratikal’s specialized OT security services, businesses can build resilient, compliant, and future-ready operational networks.
FAQs
- What is the primary goal of OT security?
IT focuses on safeguarding data by ensuring its availability, integrity, and confidentiality. In contrast, industries like manufacturing, energy, utilities, transportation, and healthcare use OT to control and monitor physical processes and equipment.
- What is OT security assessment?
A technical assessment of OT assets and their dependencies to uncover vulnerabilities and related risks that, if exploited, could lead to significant business disruptions.









Leave a comment
Your email address will not be published. Required fields are marked *