In today’s technologically advanced world, our online accounts provide access to everything from personal information and funds to professional networks and interactions. Securing these accounts with strong passwords is critical. However, a recent spike in brute force attack emphasizes the need for even stronger security measures. A recent report warns of a significant increase in brute-force attacks targeting everything from VPNs and Web Applications to SSH services.
Table of Contents
Surge in Brute Force Attacks Targets Networks Worldwide
The latest report issued a warning regarding a global rise in brute force attacks. Since at least March 18, 2024, these attacks have targeted various devices and services, including:
- Virtual Private Networks (VPNs)
- Web Application Logins
- Secure Shell (SSH) services
These known services that were affected by the brute force attacks are:
- Cisco Secure Firewall VPN
- Checkpoint VPN
- Fortinet VPN
- SonicWall VPN
- RD Web Services
- Miktrotik
- Draytek
- Ubiquiti
The brute-forcing attempts use both generic and valid usernames for specific organizations. These attacks appear to be indiscriminate, with no specific region or industry targeted. The source IP addresses of this traffic were frequently associated with proxy services, which are not limited to:
- TOR
- VPN Gate
- IPIDEA Proxy
- BigMama Proxy
- Space Proxies
- Nexus Proxy
- Proxy Rack
What is Brute Force Attack?
A brute force attack is a hacking technique in which automated systems repeatedly test a large number of password combinations until they find the correct one. Consider it like trying every key on a keyring until you find the one that unlocks the door.
These kinds of attacks are particularly harmful because they do not use advanced techniques or exploit software vulnerabilities. Hackers just use easily available tools to exploit weak passwords.
The attacks rely on automated tools that systematically attempt a vast number of username and password combinations until they gain access.
How did it Happen?
These attacks exploited the key flaws:
Get in!
Join our weekly newsletter and stay updated
Weak Passwords: Hackers often target accounts with weak or easily predictable passwords. This could be anything from simple dictionary words to personal information like birthdays or pet names. A web application might be vulnerable to a brute-force attack if it does not have a lockout mechanism in place for failed login attempts. This is why web application security is important. If businesses implement web application pentesting, such attacks can be avoided.
Anonymity Services: Brute force attack originated from anonymizing services like Tor and various proxy servers. This makes it difficult to trace the source and hold attackers accountable.
Vulnerability in Networks: A network might be vulnerable to a brute-force attack if it does not have strong password requirements in place for user accounts.
Potential Impact of this Attack
A successful brute-force attack can have severe consequences for businesses, including:
Unauthorized Network Access: Hackers can gain access to a company’s internal network, potentially compromising sensitive data, disrupting operations, or launching further attacks.
Account Takeover: Personal or corporate accounts accessed through VPNs or web applications can be compromised, leading to identity theft, financial losses, or data breaches.
Denial-of-Service (DoS) Attacks: Brute-force attempts can overwhelm login servers, making them inaccessible to legitimate users.
A successful brute-force attack can have severe consequences. Hackers could gain unauthorized access to a network, steal sensitive data, or even disrupt critical operations.
What to do to mitigate the risk of Brute Force Attacks?
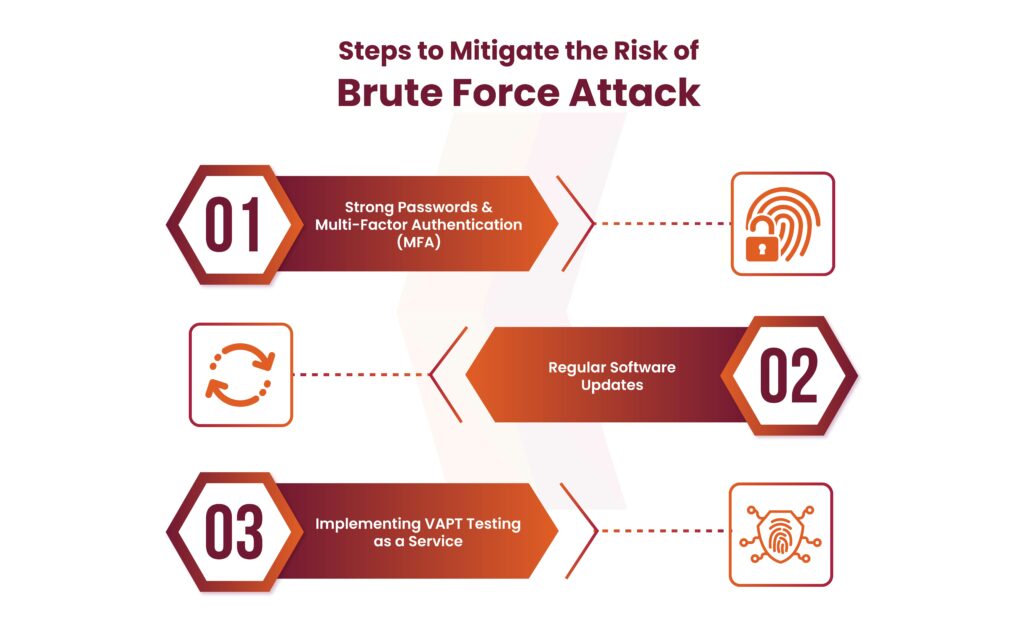
Here are some steps to mitigate the risk of brute force attacks:
Strong Passwords & Multi-Factor Authentication (MFA): Enforce strong, unique passwords for all accounts and implement MFA wherever possible. MFA adds an extra layer of security beyond just a password.
Regular Software Updates: Ensure all software and firmware are updated with the latest security patches to address potential vulnerabilities.
Implementing VAPT Testing as a Service: Consider regular Vulnerability Assessment and Penetration Testing (VAPT) testing as a service to identify and address flaws in your network security posture.
Let’s further take a look at why network pentesting must be done regularly to avoid such attacks.
Why Network Security Testing is Important?
Book Your Free Cybersecurity Consultation Today!
Our networks are the basis of our digital functioning. They enable us to access the internet, our devices, and crucial programs. A successful brute-force attack on a network could allow unauthorized access to a wealth of sensitive data, interrupt operations, or even result in financial loss. This would damage the brand reputation of organizations. This is why network security testing is important.
Network security testing is critical for preventing brute force attacks by identifying vulnerabilities such as weak passwords and misconfigurations. These security tests function as a way of exposing loopholes where attackers could acquire an entry point and attempt brute-force attacks. By identifying and addressing these vulnerabilities, you successfully prevent these types of attacks.
How Kratikal can help Businesses prevent Brute Force Attacks?
Kratikal, being a CERT-In empanelled auditor, offers VAPT services that go beyond basic security checks. Our expertise could help your business in:
- Identify and address network vulnerabilities
- Strengthen password policies and enforce MFA
- Simulate real-world attacks to test security measures
Don’t wait for an attack to occur! Secure your businesses with our VAPT services today!
Reference Source:
https://blog.talosintelligence.com/large-scale-brute-force-activity-targeting-vpns-ssh-services-with-commonly-used-login-credentials/
FAQ
- What is brute force attack?
A brute force attack is a hacking technique that involves trial and error to crack passwords, login credentials, and encryption keys.
- How can businesses prevent brute force attack?
Businesses can prevent brute-force attacks by enforcing strong passwords & MFA and performing regular VAPT (pentesting) to identify vulnerabilities.








Leave a comment
Your email address will not be published. Required fields are marked *