Financial applications, ranging from mobile banking apps to payment gateways, are among the most targeted systems worldwide. In 2025 alone, the Indusface State of Application Security Report revealed that banks and financial institutions endured 1.2 billion attacks, with each financial app experiencing double the attack frequency compared to other industries. This surge highlights the urgent need for Vulnerability Assessment and Penetration Testing (VAPT). VAPT services combine automated vulnerability scanning with manual penetration testing to identify, validate, and remediate exploitable weaknesses. When paired with mobile application testing, it provides a comprehensive defense against attackers exploiting APIs, mobile ecosystems, and business logic flaws.
Table of Contents
- 0.1 How Attackers Target Financial Applications?
- 1 Get in!
- 2 Book Your Free Cybersecurity Consultation Today!
How Attackers Target Financial Applications?
Financial applications remain one of the most lucrative targets for hackers due to the direct access they provide to money, sensitive customer data, and critical business systems. Modern attacks are no longer opportunistic; they are calculated, automated, and designed to exploit both technical and operational gaps.
Exploiting Known Vulnerabilities
Attackers actively scan financial applications for unpatched Common Vulnerabilities and Exposures (CVEs). In 2025, exploitation of known vulnerabilities surged by 74%, driven largely by automated attack frameworks. Outdated third-party libraries, legacy payment gateway components, and weak SSL/TLS configurations are frequent entry points. Once exploited, these vulnerabilities allow attackers to gain unauthorized access, execute remote code, or escalate privileges within critical financial systems.
API Abuse in Open Banking Ecosystems
APIs form the backbone of fintech platforms, enabling integrations across payment processors, banks, and third-party services. However, poorly secured APIs are a prime target. Attackers exploit weak authentication mechanisms, excessive API permissions, broken object-level authorization (BOLA), and unvalidated inputs to manipulate transactions.
Business Logic Exploitation
Unlike technical vulnerabilities, business logic flaws abuse the intended functionality of financial applications. Attackers reverse-engineer workflows to bypass transaction limits, reuse or stack promotional discounts, manipulate fee calculations, or exploit weaknesses in loan approval and refund processes. These attacks are particularly risky because they mimic legitimate user behavior and frequently evade traditional security controls.
Misconfigurations and Shadow Assets
Financial institutions often maintain multiple environments, including staging servers, customer support portals, legacy admin panels, and third-party integrations. These “shadow assets” are frequently misconfigured or insufficiently monitored. Attackers target exposed databases, weak access controls, and unsecured cloud storage to gain an initial foothold, then pivot laterally into core banking or payment systems.
How VAPT Prevents Attacks on Financial Applications?
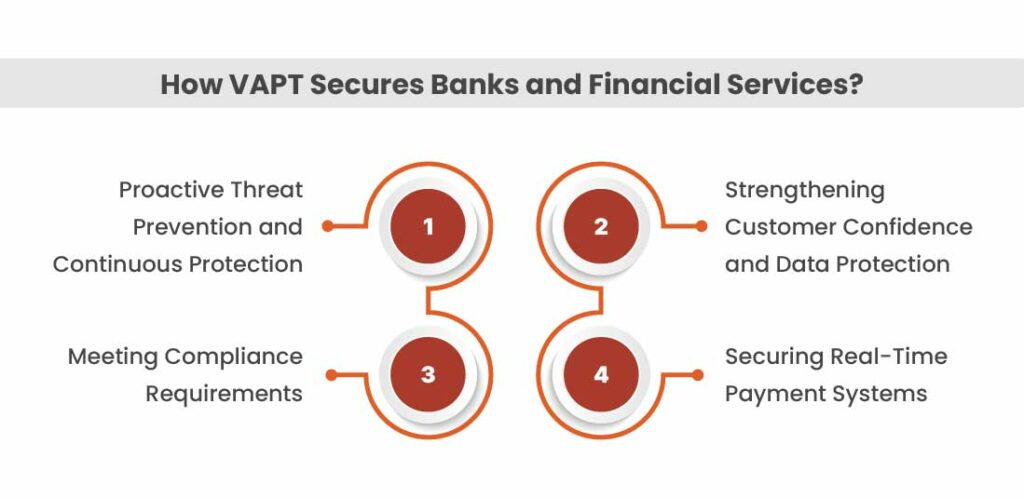
Proactive Threat Prevention and Continuous Protection:
Instead of reacting to cyber incidents after they occur, VAPT allows banks and fintech organizations to proactively strengthen their security posture. Through structured vulnerability assessments, security gaps are identified and remediated before attackers can exploit them. Penetration testing then replicates real-world attack scenarios to reveal how multiple weaknesses could be chained together to cause a major breach. When conducted annually or after significant system changes, this proactive strategy ensures continuous protection against an evolving threat landscape—significantly reducing the risk of costly downtime and financial losses.
Strengthening Customer Confidence and Data Protection
In the financial sector, customer trust is paramount, and VAPT plays a critical role in reinforcing it. By demonstrating a strong commitment to protecting sensitive financial and personal data through rigorous security assessments, organizations instill greater confidence in their customers. Preventing major data breaches not only safeguards the institution’s reputation but also protects clients’ financial interests, creating a powerful and lasting competitive advantage.
Meeting Compliance Requirements
The financial services industry is among the most heavily regulated sectors, governed by stringent cybersecurity mandates from bodies such as the Reserve Bank of India (RBI) and global standards like PCI DSS. Regular VAPT is often a mandatory requirement for compliance. By providing detailed, actionable reports, VAPT enables financial institutions to demonstrate proactive risk identification and remediation, helping them avoid regulatory penalties, reduce legal exposure, and maintain a strong, audit-ready security posture.
Securing Real-Time Payment System
VAPT delivers comprehensive vulnerability discovery by identifying security gaps across multiple layers, including network configurations, exposed API endpoints, and misconfigured payment gateways. Simulating real-world attack scenarios, it allows organizations to assess the resilience of their payment systems against common threats such as SQL injection and cross-site scripting (XSS). VAPT also validates transaction integrity by emulating man-in-the-middle attacks to confirm proper end-to-end encryption and secure data transmission. In addition, detailed API security testing ensures strong authentication, effective data handling, and appropriate access controls, significantly reducing the risk of exploitation and safeguarding the core infrastructure behind real-time financial transactions.
Get in!
Join our weekly newsletter and stay updated
Technical Benefits of VAPT
| Attack Vectors | How VAPT Counters It? |
| Known CVEs | Security testers manually verify whether reported CVEs are exploitable in the specific environment, attempt proof‑of‑concept exploits, and confirm impact instead of relying solely on automated flags. |
| API Abuse | Pen testers craft custom payloads, bypass weak authentication, manipulate rate limits, and fuzz API endpoints to uncover logic flaws and privilege escalation opportunities. |
| Malicious Apps | Through mobile application testing, testers reverse engineer APKs/IPA files, analyze code for hardcoded secrets, simulate runtime attacks, and manually validate encryption/storage mechanisms. |
| Misconfigurations | Manual reviews of server configs, SSL/TLS setups, and exposed services are performed; testers attempt direct exploitation to validate the risk. |
| Credential Stuffing | Testers replicate brute force and credential stuffing attacks with controlled datasets, evaluate lockout/MFA bypass mechanisms, and confirm whether protections withstand sustained manual attack attempts. |
Book Your Free Cybersecurity Consultation Today!
How Kratikal Can Help You With VAPT Services?
Kratikal helps financial institutions stay ahead of evolving cyber threats through comprehensive VAPT services designed specifically for banking and fintech environments. By identifying vulnerabilities across applications, APIs, networks, and payment systems, Kratikal uncovers security gaps before attackers can exploit them. Our expert-led penetration testing simulates real-world attack scenarios to reveal how weaknesses could be chained into serious breaches, while detailed, actionable reports support faster remediation and regulatory compliance. With Kratikal’s VAPT services, organizations can strengthen their security posture, protect sensitive financial data, and build lasting trust with customers in an increasingly hostile threat landscape.
FAQs
- How does VAPT help secure financial applications?
VAPT helps financial institutions detect exploitable vulnerabilities early, understand real-world attack paths, and remediate risks before they can be exploited by attackers.
- How does VAPT protect APIs used in banking and fintech platforms?
VAPT evaluates API security by testing authentication mechanisms, access controls, rate limits, and input validation. Pen testers attempt to exploit broken object-level authorization (BOLA), excessive permissions, and logic flaws to ensure APIs cannot be abused for unauthorized transactions or data exfiltration.








Leave a comment
Your email address will not be published. Required fields are marked *