Cybersecurity teams face mounting pressure to find vulnerabilities faster. AI-powered scanners are emerging as force multipliers: they use machine learning and intelligent agents to automate and accelerate the pentesting process. Unlike traditional signature-based scanners, an AI vulnerability scanner can learn from massive datasets, spot anomalous patterns, and continuously update its knowledge of threats. The result is faster, scalable scanning and smarter risk prioritization, drastically reducing manual effort and overall pentesting time.
Agentic AI vulnerability scanners can dramatically accelerate tasks like network scanning and vulnerability detection. For example, AutoSecT’s AI-powered scanner advertises “80X Faster Vulnerability Detection” while producing near-zero false positives. Such agentic scanners autonomously enumerate hosts, probe each system with custom logic, and update themselves from new threat feeds. In practice, this means mapping thousands of devices and running checks in minutes or hours – a task that might take days or weeks manually. By continuously “learning” new CVEs and exploits (even generating its own exploit code in hours), an AI scanner stays up-to-date without waiting for slow signature releases. The bottom line: an AI scanner turns pentesters into strategic overseers rather than clerks, slashing routine workload and speeding up the entire engagement.
Table of Contents
How AI Vulnerability Scanner Improves Efficiency?
An AI vulnerability scanner fundamentally improves security testing efficiency by replacing manual, repetitive, and time-consuming pentesting tasks with intelligent automation. Unlike traditional scanners that follow fixed rules, an AI scanner adapts its testing approach based on application behavior, attack surface context, and real-world threat intelligence. This allows security teams to identify, validate, and prioritize vulnerabilities faster and with greater accuracy.
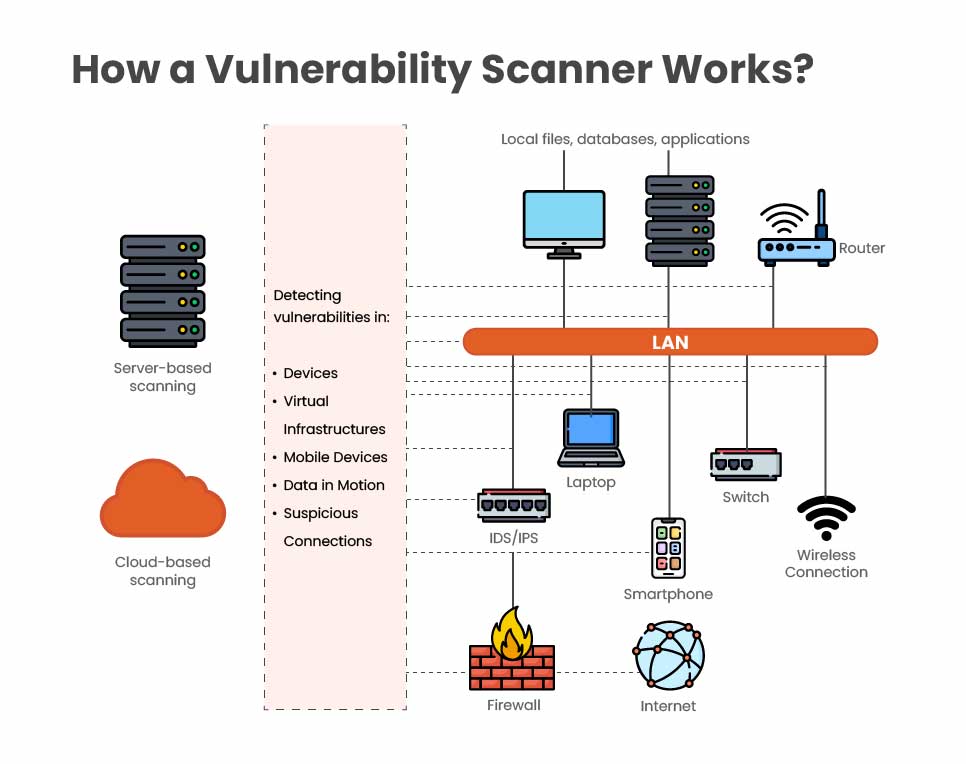
Automated Attack Surface Discovery
An AI vulnerability scanner continuously maps the entire attack surface by identifying applications, APIs, cloud assets, network services, and configuration changes in real time. Unlike manual reconnaissance or periodic scans, the AI scanner dynamically updates its view as environments evolve. This ensures no asset is missed during testing and removes the need for repetitive manual discovery, significantly reducing the time spent preparing for pentesting.
Intelligent and Adaptive Vulnerability Detection
Traditional scanners rely on static rules, while an AI scanner analyzes application behavior, data flows, and system responses to detect vulnerabilities. Using machine learning, the AI vulnerability scanner adapts its testing strategy based on findings, automatically exploring deeper attack paths when weaknesses are discovered. This enables the detection of complex issues such as business logic flaws, chained vulnerabilities, and misconfigurations that typically require extensive manual testing.
Faster Validation with Near-Zero False Positives
One of the biggest efficiency challenges in pentesting is validating scanner results. An AI vulnerability scanner improves this by confirming exploitability through contextual analysis and simulated attack scenarios. By filtering out non-exploitable findings, the AI scanner delivers cleaner, more accurate reports. This reduces time wasted on manual verification and allows security teams to focus on real, high-impact vulnerabilities.
Risk-Based Prioritization for Faster Remediation
AI vulnerability scanners automatically prioritize vulnerabilities by analyzing exploitability, asset criticality, exposure level, and potential business impact. Instead of overwhelming teams with long vulnerability lists, the AI scanner highlights the most critical risks first. This enables faster decision-making, more effective remediation planning, and a significant reduction in overall pentesting and risk mitigation timelines.
Book Your Free Cybersecurity Consultation Today!
Inside AI Driven Vulnerability Scanning
Modern AI scanners employ machine learning (ML), natural language processing (NLP), and sometimes large language models to analyze code, configurations, and network data. They go beyond static signatures by recognizing patterns and anomalies. For example, an AI tool might learn that a certain API usage or misconfiguration often leads to an exploit, flagging it even if no exact signature exists. In practice, this means feeding the AI vast amounts of vulnerability data and letting it generalize. Some tools use RAG (Retrieval-Augmented Generation): they have an internal knowledge base of vulnerabilities and can even generate new exploit tests on the fly.
Key Capabilities of AI Scanners Include:
Scalable identification:
AI scanners analyze huge datasets from applications, networks, and endpoints. They can crawl and test thousands of input combinations or host configurations in one pass. For example, deploying an AI scanner in a large network can quickly flag misconfigurations or unpatched systems across all devices. This scale is far beyond what human teams can cover in a reasonable time.
Intelligent prioritization:
Not all findings are equal. AI-enabled vulnerability management ranks each issue by risk – considering factors like system criticality, exploit likelihood, and business impact. By automatically triaging and contextualizing vulnerabilities, it directs human attention to the most risky flaws first. This risk-based focus cuts down endless low-priority alerts and helps teams fix the big problems swiftly.
Proactive Threat Learning:
Traditional scanners rely on predefined rules or CVE databases. AI scanners continually retrain on new data, enabling them to spot novel or zero-day issues. For example, if an AI learns the pattern of how attackers exploit a remote code execution bug, it can identify similar logic issues elsewhere even if no exact rule exists. In effect, AI scanners act as “24/7 pentesters” that adapt as code changes.
An AI scanner behaves more like a persistent, adaptive team member. It reasons about the system, tries multiple exploit paths, and learns from every outcome, much like an experienced penetration tester would. This “thinking” ability allows it to discover issues beyond static checks.
How AI Helps Security Teams Focus on the Right Vulnerabilities?
As attack surfaces expand and vulnerability data grows, distinguishing critical risks from background noise becomes challenging. AI helps bring focus by prioritizing vulnerabilities based on real exploit potential, asset criticality, and business impact.
Ranks Vulnerabilities by Risk:
Instead of relying only on CVSS scores, AI evaluates how likely a vulnerability is to be exploited in real-world attack scenarios. It considers threat intelligence, attacker behavior, and system context, helping teams focus on vulnerabilities that pose real business risk.
Connects Technical Findings to Business Impact:
AI prioritization maps vulnerabilities to critical assets, applications, and data flows. This allows security teams to understand which issues could impact operations, customer trust, or compliance, making it easier to communicate risk to leadership and drive faster decisions.
Identifies Exploitable Attack Paths:
AI analyzes how multiple low- or medium-severity vulnerabilities can be chained together into a successful attack. By highlighting complete attack paths rather than isolated findings, it provides a clearer picture of how attackers could compromise systems.
Get in!
Join our weekly newsletter and stay updated
Conclusion
AI-powered vulnerability scanners are reshaping the way organizations approach pentesting by moving beyond periodic, manual assessments to continuous, intelligence-driven security testing. Through automated attack surface discovery, adaptive analysis of application and infrastructure behavior, and validation of vulnerabilities using real exploit scenarios, AI significantly reduces the time and effort required to identify meaningful security risks.
Instead of overwhelming teams with raw findings, AI-driven prioritization highlights vulnerabilities that carry genuine exploit potential and business impact, enabling faster, more confident remediation decisions. As attack surfaces continue to expand and threats evolve rapidly, AI vulnerability scanners provide the clarity, speed, and scalability needed to reduce pentesting time by up to 80% while strengthening overall security posture.
FAQs
- How does an AI scanner reduce pentesting time?
An AI scanner automates reconnaissance, vulnerability detection, validation, and prioritization. By replacing manual, repetitive tasks with intelligent automation, it significantly shortens the overall pentesting lifecycle.
- Does an AI scanner eliminate false positives?
AI scanners drastically reduce false positives by validating exploitability through contextual analysis and simulated attack scenarios, ensuring only real and actionable vulnerabilities are reported.









Leave a comment
Your email address will not be published. Required fields are marked *