Every day a CISO spends their time almost entirely in protecting people, assets, and IT infrastructure. However, are they missing anything? Let’s find out!
Don’t jump to any conclusion that CISOs are completely blind to the cyber threats surrounding them after reading the title of the blog. Let me remind you a CISO is doing much more than one can imagine!
But as the saying goes, “there is always room for improvement!”
If you missed one of our blogs “5 Important Insights for CIOs & CISOs in 2021” then I strongly recommend you check that out as well.
So, wondering what can be done more?
Before you find that out, let’s take a look at some of the things they are doing already.
I said some because there is a reason. If I try to explain all the things a CISO does then one blog wouldn’t be enough. But just a scratch on the surface!
Now being said that, I will try to cover as much as possible.
Table of Contents
Understanding CISO Roles and Responsibilities
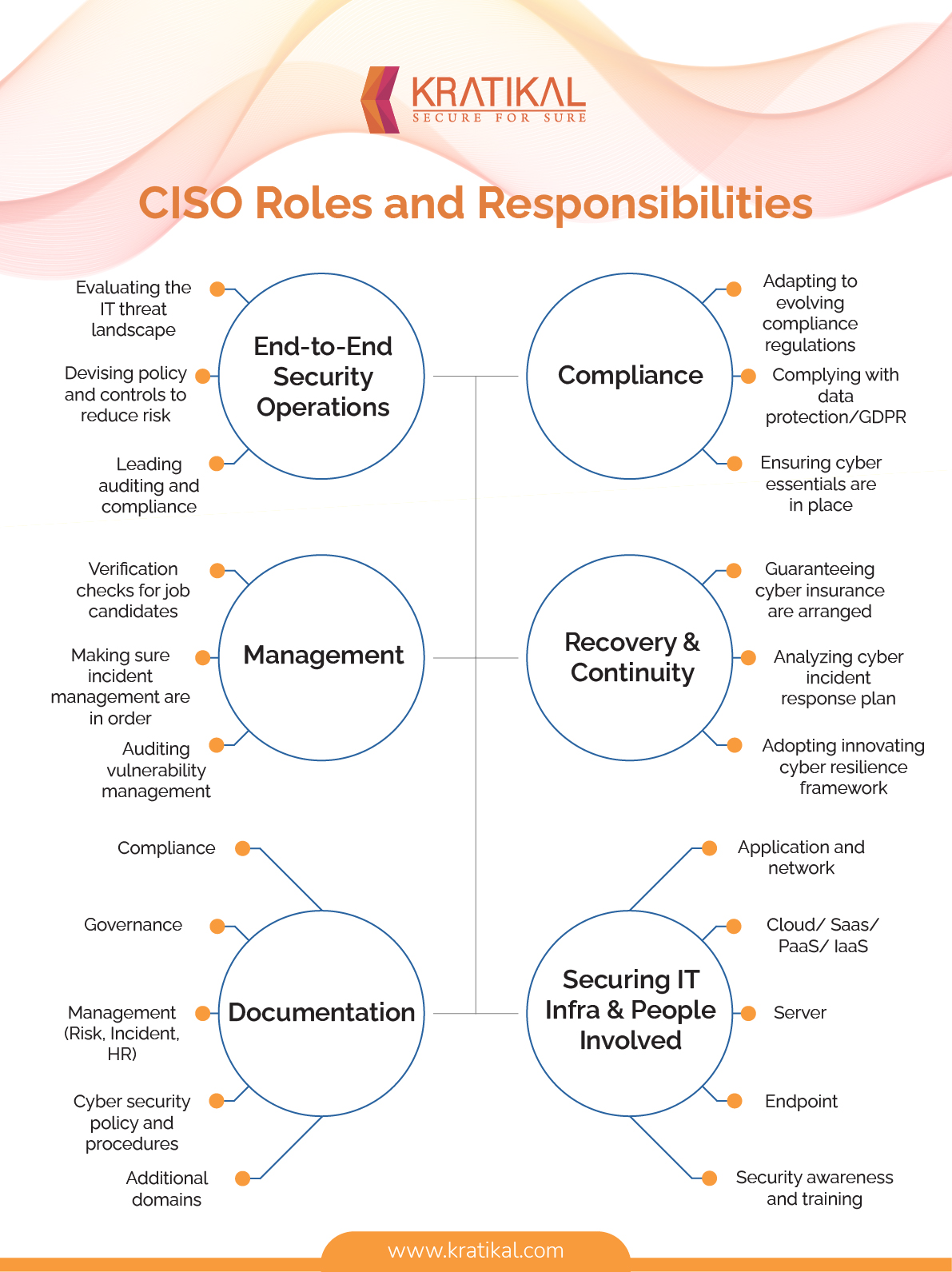
CISO Roles and Responsibilities
When we think of the roles and responsibilities of a CISO, what most people think is that they take care of the cyber security measures of an organization. Yes, that is completely true.
However, when asked what CISOs need to do to secure an organization, we get very limited answers.
So, let’s take a look at some of the roles and responsibilities of a CISO:
Securing the Technology
Today almost every organization has shifted to the technology era or let’s say adapted the latest technologies for better performance and cost-efficiency. However, one big challenge in implementing those technologies is keeping them secure. This is where a CISO’s role comes in. They help in securing:
- Application
- Server
- Network
- Cloud/ SaaS/ PaaS/ IaaS
- Data
- BYOD
- Systems
Analysis
Real-time analysis of cyber threats that are evolving with time and the latest technologies. Also, identifying the loopholes in the IT infrastructure and fixing them accordingly. Analyze the potential threats within an organization so that internal staff does not misuse or steal the data. Moreover, evaluate the new candidates that are to join the particular organization.
Security Strategy
This involves planning and adopting security measures to make sure that IT and network infrastructure is built with the finest security practices in mind. Also, building a strategy to defend the problems that might arise in the future.
Regulatory and Compliance
Making sure that the organization is following and complying with cyber security rules and regulations. That includes data protection, GDPR, and much more. Create a security policy for team members to follow to protect the organization against cyber criminals.
Investigation
Identifying what went wrong in case the organization suffers a cyber attack. Plan and fix the loopholes to avoid the same crisis again. Moreover, if it’s internal then deal with the same to fix the issue.
Governance
Making sure all the cyber security initiatives are running smoothly. Ensure the funds are provided to put the cyber security measures in place. Planning a budget for cyber security in an organization and making sure every security measure is covered within the budget.
Moving Forward
The roles and responsibilities of a CISO go beyond what is listed above. The best CISOs offer security strategic advice and do in-depth industry research. Also, they make sure everyone connected with the organization is safe and protected, including the clients, partners, and employees. That is, protect their personal information, credentials, etc.
“There are many words I might use to describe my job — stimulating, challenging, frantic, stressful, and a couple others I’ll leave out to keep this family-friendly — but boring isn’t one of them.” Says Allison Henry, Chief Information Security Officer at the University of California, Berkeley.
Now, the billion-dollar question is, after all these security best practices, how come an organization falls for a cyber attack? Well, there can be several reasons, such as:
- Not updating software or hardware on time
- Getting infected with virus from third-party applications
- An employee giving away login credentials to a phishing email
There are numerous reasons. Therefore, with the evolving cyber threat landscape, CISOs would also have to step up the game in protecting the organization.
It’s now even more important for cyber security professionals and business leaders to defend against the existing cyber threats and prepare for what might come next.
How Can They Stay Ahead
We believe there are three imperatives for CISOs and organizations to focus on in the second half of this year:
#1. Create a Strategy to Identify the Loopholes
When creating or developing a security strategy, it is important to know and understand how to identify the cyber security loopholes. As CISOs try to build a security strategy for the second half of the year, finding the weak spot of an IT infra should be a top priority.
#2. Leverage Innovations
Trends show a rapid acceleration of sophisticated cyber attacks using advanced technology. Moreover, hackers with low skills are taking advantage of easily available ready-to-use hacking toolkits/services. So, to stay one step ahead, organizations and cyber experts need to invest in solutions that go along with the latest technologies.
#3. Create a Cyber Secure Work Culture
Ensure every staff member realizes that an organization’s cyber security is no longer the sole responsibility of IT and cyber security teams. The organization is as strong as the weakest link in the cyber security chain. Therefore, the security leaders will need to nurture an organization-wide mindset that prioritizes cyber security by providing the employees with adequate training.
To achieve this, you can choose kratikal v-Ciso Services. With the help of the virtual CISO service, top-tier security professionals may be made accessible to enterprises that want security advice and experience. Our team of professionals has decades of expertise in creating information security strategies that support business objectives and demonstrate measurable improvements to security posture.







Leave a comment
Your email address will not be published. Required fields are marked *