Red Teaming (also called adversary simulation) is a way to test how strong an organization’s security really is. In this, trained and authorized security experts act like real hackers and try to break into systems, just like attackers would in the real world.
NIST defines a Red Team as a group that is allowed to act like an attacker to see what damage could happen and how well the security team responds.
- The Red Team plays the role of the attacker. They try to find ways to get into systems.
- The Blue Team is the defense. They monitor systems, block attacks, and respond to incidents.
- The Purple Team brings both together so that what the Red Team learns is used to make the Blue Team stronger.
Red Teaming is different from regular vulnerability scans or penetration tests. Instead of just checking for known issues, Red Teams run realistic attack scenarios that can include:
- Hacking systems
- Tricking people (like phishing)
- Even testing physical security
These exercises show how an attacker could move step by step through an organization and help test how well the security team reacts under pressure. This helps companies find weaknesses they might not know about and improve their overall security.
Table of Contents
Realistic Attack Simulation with Red Teaming
Red Teaming copies the same methods that real hackers use. These methods are called Tactics, Techniques, and Procedures (TTPs), basically, the steps attackers follow to break into a company. A Red Team may start by collecting public information about employees or sending fake emails (phishing) or making fake phone calls. If someone clicks a bad link or plugs in a malicious USB, the Red Team may get inside the network. From there, they try to move deeper by exploiting weak or unpatched systems and using tools to gain higher access and understand how the network works.
The goal is not random hacking; every attack is done to reach a specific target, like accessing sensitive data or taking control of a key system. Even though real attack tools may be used, everything is done safely, so nothing gets damaged. This lets the security team see how an attack would really happen, from the first step (finding a target) to the final step (stealing data).
The Cyber Kill Chain in Red Team Operations
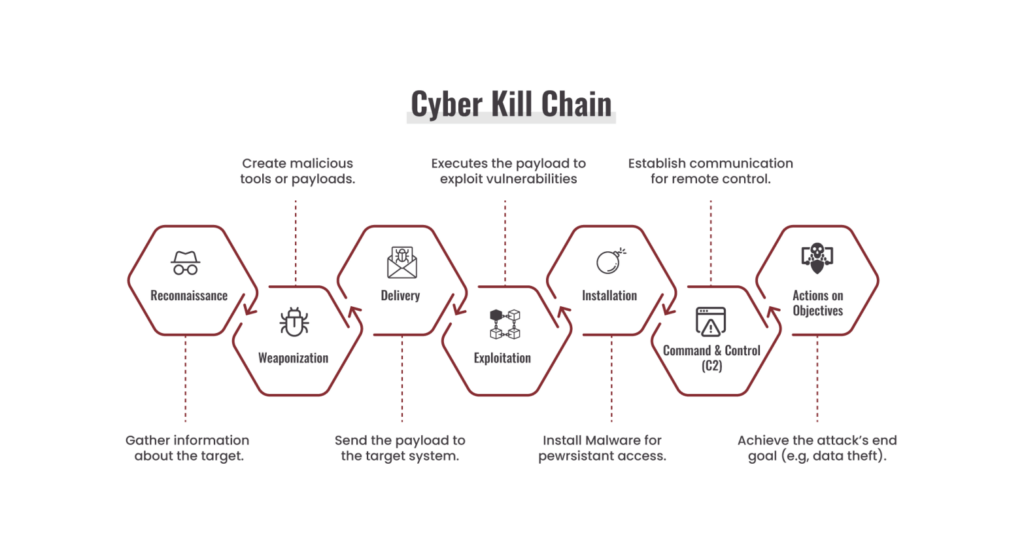
Red Teams often organize an engagement using the Cyber Kill Chain framework, which breaks an attack into phases. This structured model ensures every stage of an intrusion is tested. A typical Red Team campaign aligns roughly with the kill-chain steps:
Reconnaissance
It is the first step in the Cyber Kill Chain. In this stage, attackers gather information about their target, such as systems used, weaknesses, and connected third-party vendors. They look for possible ways to get in, both online and offline, by studying people, technology, and processes to find the easiest path for an attack.
Weaponization
This is the stage where attackers prepare the tools they will use to break into the target’s network. This includes creating or selecting malware, ransomware, harmful payloads, and other malicious software designed to exploit weaknesses in the system.
Delivery
Adversaries try to contact users by sending phishing emails that include harmful links. These messages use tempting or urgent subject lines to trick people into clicking. Once the message is delivered and opened, attackers can gain access to the organization’s network and begin exploiting weaknesses in systems and software.
Exploitation
Attackers push further into the network by using the weaknesses they have already identified. Their goal is to gain more access, move between systems, and reach higher-value targets, especially those that lack proper security protections. They may steal credentials, elevate privileges, and quietly map the network to find critical systems. This allows them to stay hidden while expanding control. Each successful move brings them closer to their final objective, such as data theft or system takeover.
Installation
During the installation phase, attackers place malware or ransomware inside the target network. Their goal is to take control of systems and steal sensitive information. They may also set up backdoors, trojans, or other malicious tools that allow them to keep access and run commands remotely.
Command & Control (C2)
In the command-and-control phase, attackers connect to the malware they have installed in the network. Through this connection, they send instructions to the infected systems and control them from a distance. Using these communication channels, they can run attacks, move data, or even overload websites by directing multiple compromised machines to act together.
Actions on Objectives
This is the final stage, where attackers work to achieve their main goals. Depending on the type of attack, they may try to shut down services, disrupt operations, or force the organization offline. They could steal sensitive data, launch denial-of-service attacks, or use ransomware to pressure the organization into paying a ransom.
Book Your Free Cybersecurity Consultation Today!
How OSINT Helps Red Teams?
Effective Red Teaming relies on thorough reconnaissance. Teams use OSINT (Open Source Intelligence) tools and frameworks to gather publicly available information about people, networks, and systems. This typically includes:
- Domain and network data: using tools like Shodan (internet-connected device search) or WHOIS to find open ports, exposed services, and subdomains.
- Email and identity harvesting: using TheHarvester, Sherlock, or email scraping tools to enumerate employee addresses and aliases.
- Social media and corporate information: scanning LinkedIn, Twitter, company websites, news articles, and more to uncover employee roles, technology stack, or company partnerships.
- GitHub and code repositories: looking for leaked credentials or API keys in public code.
Red Teams usually start by using OSINT checklists to gather public information about a target. These checklists organize hundreds of online sources into categories, making it easier to find details about a company’s systems, employees, and digital footprint. By exploring these sources, a Red Team can learn about domains, email addresses, network details, and even relationships between people and systems. This early research helps them identify potential weaknesses and potential attack paths.
Data Exfiltration: When Stolen Data Leaves Your Network
A key goal of Red Teaming is to see if data can be stolen without anyone noticing. To test this, Red Teams safely simulate data exfiltration, the act of moving sensitive data out of a network. They try different hidden ways to send data out, such as hiding it in internet traffic, sending it through file transfers, or uploading it to external cloud accounts. During the test, they check whether security tools like DLP and SIEM raise any alerts.
If the data leaves the network without being detected, it shows a security gap. After the exercise, the Red and Blue Teams work together to improve monitoring and create better rules so real attackers can be stopped before important data is stolen.
Get in!
Join our weekly newsletter and stay updated
How Can Kratikal Help You With Red Teaming?
Kratikal offers comprehensive Red Teaming services that help organisations identify hidden security gaps before real attackers exploit them. Their expert team begins with detailed intelligence gathering using OSINT and other reconnaissance methods, then carefully plans and executes realistic attack simulations that mirror real-world adversary techniques, including social engineering, penetration methods, and advanced exploitation. Throughout the engagement, Kratikal documents each step and provides actionable insights and detailed reports that show how an attacker could move through your environment, helping you prioritise remediation, strengthen defenses, and improve your incident response capabilities. With a structured methodology and experienced security professionals, Kratikal ensures your security posture is thoroughly tested and made far more resilient against real cyber threats.
FAQs on Red Teaming
- What frameworks are used in Red Teaming?
Red Teaming commonly maps attacks to the Cyber Kill Chain, MITRE ATT&CK, and OSINT frameworks to ensure each phase of a real attacker’s journey, from reconnaissance to data exfiltration, is tested.
- What is lateral movement in Red Teaming?
Lateral movement is when an attacker moves from one compromised system to another inside the network to gain higher privileges or reach critical systems such as domain controllers, databases, or production servers.








Leave a comment
Your email address will not be published. Required fields are marked *