2025 has already proven to be a defining year in the cybersecurity landscape. With attackers leveraging AI-driven automation, deepfake social engineering, and highly targeted supply-chain compromises, cyberattack is no longer just disruptive; they’re strategically engineered for maximum impact. Attackers have targeted every organization, from global enterprises to fast-growing startups. In this blog, we break down the Top 10 Cyberattacks of 2025, highlighting what went wrong, how the attacks unfolded, and the critical lessons security leaders must take forward to strengthen their defense posture in an increasingly hostile digital world.
Beyond headlines and numbers, these incidents expose deeper gaps in visibility, response readiness, and third-party risk management. More importantly, they reveal how quickly today’s minor vulnerabilities can escalate into full-blown business crises. Whether you’re leading security strategy or shaping technology decisions, this analysis will help you anticipate threats before they strike.
Table of Contents
- 0.1 Inside the Biggest Breaches of 2025
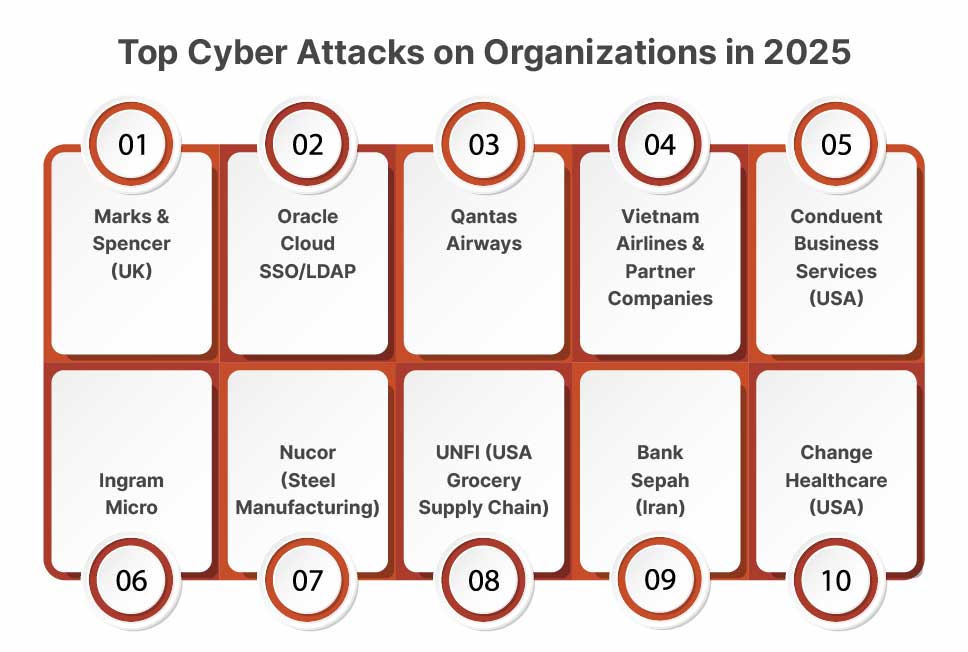
- 0.1.1 Marks and Spencer (M&S) – UK Retail Operations Hit
- 0.1.2 Oracle Cloud SSO/LDAP Breach: 6 million Identity Records Compromised
- 0.1.3 Qantas – 5.7 million frequent flyer profiles leaked
- 0.1.4 Vietnam Airlines and Partners – 23M traveler records
- 0.1.5 Conduent Business Services: 10.5M+ Records
- 0.1.6 Ingram Micro – Multi‑TB Corporate Data Theft
- 0.1.7 Nucor – Steel Manufacturing Outages
- 0.1.8 UNFI Cyberattack Disrupts US Grocery Supply Chain
- 0.1.9 Cyberattack Cripples Bank Sepah, Iran’s Banking Giant Goes Dark
- 0.1.10 Change Healthcare Massive PHI Exposed
- 1 Book Your Free Cybersecurity Consultation Today!
- 2 Get in!
Inside the Biggest Breaches of 2025
Behind every major breach lies a chain of overlooked risks, delayed detection, or misconfigured defenses. The following list unpacks the biggest cyber breaches of 2025, outlining how they unfolded.
Marks and Spencer (M&S) – UK Retail Operations Hit
In April 2025, M&S was hit by a ransomware cyberattack by Scattered Spider, deploying DragonForce ransomware. Retail operations, including contactless payments, online orders, and inventory systems, collapsed, forcing manual workarounds in 1,400+ stores. The breach involved stolen customer data and is expected to cost roughly £300 million in lost profit.
Investigators traced the attack to compromised credentials and weaknesses in third-party access controls, highlighting the growing risk of supply-chain exposure. M&S immediately isolated affected systems and worked with cybersecurity experts and law enforcement to contain the breach. The incident underscores the urgent need for stronger identity security, continuous monitoring, and ransomware preparedness across the retail sector.
Oracle Cloud SSO/LDAP Breach: 6 million Identity Records Compromised
On 21 March 2025, CloudSEK’s XVigil discovered a threat actor – “rose87168” – offering for sale 6 million records allegedly exfiltrated from Oracle Cloud’s SSO and LDAP infrastructure. The leaked data reportedly included JKS files, encrypted SSO passwords, key files, and enterprise-manager JPS keys, potentially affecting over 140,000 tenants. The attacker claims the breach exploited an undisclosed vulnerability in a login endpoint, demanding ransom for data removal and encouraging decryption help. CloudSEK rated the incident as “High” severity, raising serious supply-chain and credential-security concerns.
Qantas – 5.7 million frequent flyer profiles leaked
Hackers, the group Scattered Lapsus$ Hunters, leaked personal data of around 5 million Qantas customers on the dark web after a ransom deadline expired. Data originated from a June 2025 breach of a third-party contact-center platform tied to Salesforce. The exposed details include names, email addresses, phone numbers, birthdates, and frequent-flyer numbers; financial data and passports were reportedly not compromised. The leak raises serious risks of phishing, identity fraud, and social-engineering attacks targeting affected customers.
Vietnam Airlines and Partners – 23M traveler records
Hackers released 23 million customer records belonging to Vietnam Airlines and other firms on dark-web forums after compromising a third-party customer-service platform used by the airline. The exposed data, spanning may include names, email addresses, phone numbers, dates of birth, and frequent-flyer (Lotusmiles) membership numbers. Vietnam Airlines clarified that sensitive information such as payment, passport, and itinerary data remained secure.
The cyberattack highlights the growing risk posed by third-party service providers and supply-chain dependencies. While core airline systems were not reportedly compromised, the scale of the leak significantly increases the risk of phishing, identity theft, and targeted fraud. The incident has triggered regulatory scrutiny and renewed calls for stricter data-protection controls across the aviation sector.
Conduent Business Services: 10.5M+ Records
In January 2025, Conduent confirmed a massive data breach that impacted over 10.5 million individuals across the United States. The SafePay ransomware group accessed Conduent’s network as early as October 2024, and the company discovered the breach in mid-January 2025. Attackers reportedly stole around 8.5 TB of sensitive data, including names, Social Security numbers, dates of birth, addresses, and health and insurance information. Conduent has restored its systems, notified affected individuals, and informed law enforcement, while advising victims to monitor their credit activity closely.
Ingram Micro – Multi‑TB Corporate Data Theft
Hackers from the group Safepay claim to have stolen 3.5 TB of internal data from Ingram Micro and are threatening to publish it unless a ransom is paid. According to the group, the leak includes sensitive internal information, though the exact scope is still under investigation by Ingram Micro, which pulled some systems offline after detecting the attack. The attackers set an August 1 deadline for releasing the leaked data, increasing pressure on the company and showing how ransomware-style extortion now relies more on data theft than just encryption. The attack underscores the growing risks of supply-chain vulnerabilities and the critical need for strengthening cybersecurity monitoring, incident response plans, and employee awareness to prevent similar large-scale breaches.
Nucor – Steel Manufacturing Outages
In May 2025, Nucor, North America’s largest steel producer, suffered a cyberattack after an unauthorized party accessed parts of its IT infrastructure. To contain the incident, the company took multiple systems offline and temporarily shut down several production facilities while engaging cybersecurity experts and law enforcement. In a later regulatory filing, Nucor confirmed that a limited amount of data had been exfiltrated. Although the company gradually restored operations, the incident exposed major cyber risks in the manufacturing sector and reinforced the need for stronger cybersecurity resilience across industrial and supply-chain operations.
UNFI Cyberattack Disrupts US Grocery Supply Chain
In June 2025, grocery wholesaler UNFI detected unauthorized activity across its IT systems and shut down critical infrastructure as a precautionary containment step. The incident disrupted order fulfillment and distribution operations, impacting deliveries to more than 30,000 retail stores, including major supermarket chains. As systems went offline, retailers faced supply delays and temporary shortages of essential goods. UNFI engaged cybersecurity experts and law enforcement to investigate and recover affected systems. The company gradually restored core operations but acknowledged that short-term residual disruptions would continue, highlighting the growing cyber risks to food supply chains and critical infrastructure.
Cyberattack Cripples Bank Sepah, Iran’s Banking Giant Goes Dark
The hacktivist group Predatory Sparrow claimed responsibility for a cyberattack on Bank Sepah, a major state-owned Iranian bank linked to the military. The bank’s website, ATMs, and online banking services went offline, and branches closed, blocking customers from accessing accounts or making transactions. According to media reports, the attackers said they “destroyed data” as retaliation against the bank’s alleged financing of illicit regime activities. The cyberattack on Bank Sepah’s infrastructure underscored how adversaries increasingly use cyber warfare to target critical financial systems, severely disrupting civilian access to banking services.
Change Healthcare Massive PHI Exposed
In February 2024, Change Healthcare, a major billing and claims-processing provider, was hit by a ransomware attack by the ALPHV/BlackCat group. The breach forced the company to take down large parts of its infrastructure, crippling billing, insurance verification, pharmacy benefits, and claims processing nationwide. Attackers reportedly stole around 6 TB of sensitive data, including patient records, insurance, and payment details. The disruptions left many hospitals, clinics, and pharmacies unable to process claims or receive payments, triggering severe cash-flow and operational crises. The aftermath exposed deep vulnerabilities in third-party dependencies, compliance protocols, and industry-wide cyber-resilience.
Book Your Free Cybersecurity Consultation Today!
High impact CVEs Behind Major Breaches
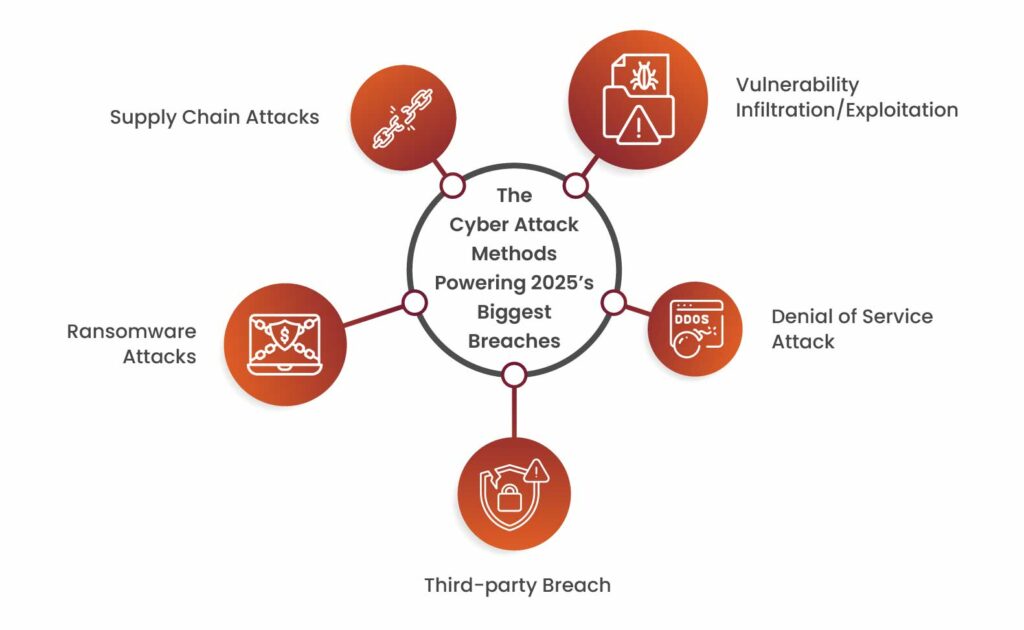
Many of today’s biggest security incidents didn’t begin with advanced attacks, but with well-known, exploitable flaws left unaddressed. The following high-impact CVEs opened the door to major breaches, highlighting just how critical rapid patching and proactive vulnerability management truly are.
CVE-2025-54236 – Adobe ColdFusion
Adobe Commerce and Magento Open Source were hit by a critical vulnerability, tracked as CVE-2025-54236, with a high severity score of 9.1. The flaw stems from improper input validation in the platform’s REST API, allowing attackers to hijack customer sessions and take over user accounts without proper authentication. Soon after Adobe released the patch, researchers observed large-scale exploitation attempts, with hundreds of attacks recorded within a short span. Security teams found a significant number of online stores unpatched, making them easy targets for attackers. Successful exploitation can lead to unauthorized access to customer data, financial fraud, and the deployment of persistent backdoors. The incident highlights the urgent need for rapid patching in e-commerce environments, where delayed updates can directly impact customer trust, business continuity, and revenue.
CIVN-2025–0163 High-Risk Apple OS Vulnerabilities
Multiple high-severity vulnerabilities have been discovered across Apple operating systems, including iOS, iPadOS, macOS, watchOS, tvOS, and visionOS. These flaws originate from memory corruption issues, logic errors, improper input validation, and weak privilege controls. If exploited, attackers could gain unauthorized access, execute arbitrary code, steal sensitive data, bypass built-in security protections, or cause system crashes. Both personal users and enterprise environments are at risk, especially on unpatched devices.
CVE-2025-10035 – Fortra GoAnywhere MFT
A critical deserialization flaw in GoAnywhere MFT’s License Servlet (affecting versions ≤ 7.8.3) allows an attacker, with a forged license‑response signature, to inject malicious data, triggering arbitrary command execution and full remote code execution. A threat actor group tracked as Storm-1175 has already exploited this vulnerability since early September 2025, deploying remote‑management tools, backdoors, and in some cases, ransomware payloads such as Medusa. Rated with a CVSS score of 10.0, the issue highlights the urgent need for organizations to immediately patch vulnerable instances and strengthen their defenses to prevent active exploitation.
How Organziations Can Prevent These Attacks?
Below are the ways in which the organizations can prevent the cyberattack:
Implement Continuous Vulnerability Management
Cyber risk is no longer static; it changes daily as new assets, configurations, and threats emerge. Continuous vulnerability management ensures that organizations are not relying on outdated scan results. With an always-on approach to vulnerability discovery, validation, and prioritization across IT, cloud, and OT environments, security teams gain real-time visibility into their true exposure. This proactive approach prevents attackers from exploiting newly introduced weaknesses that often go unnoticed for weeks or months.
Prioritise Rapid Patch Management
Several of the biggest breaches in 2025 originated from known but unpatched vulnerabilities. Organizations must move away from “monthly patch cycles” to risk-based patching. Critical vulnerabilities with active exploitation should be patched within hours, not weeks. Automated patch deployment, asset inventory accuracy, and vulnerability-to-business impact mapping are essential to shrinking the attacker’s window of opportunity.
Strengthen Identity & Access Management (IAM)
Stolen credentials remain one of the most reliable entry points for attackers. Strong IAM must go beyond basic MFA and include least-privilege enforcement, conditional access policies, device trust validation, and real-time identity threat detection. Security teams must continuously monitor cloud identity platforms, SSO systems, and privileged accounts for abnormal access patterns to prevent account takeovers and lateral movement.
Harden Cloud, API & Application Security
As cloud identity platforms and APIs become primary attack surfaces, organizations must implement secure API gateways, encrypted authentication flows, strict input validation, and cloud security posture management (CSPM). Misconfigured cloud resources, exposed keys, and weak API authentication are now the fastest paths to large-scale data breaches.
Get in!
Join our weekly newsletter and stay updated
Conclusion
The year 2025 has made it unmistakably clear that no organization is immune from a cyberattack. From ransomware attacks and massive data breaches to supply-chain compromises and the exploitation of unpatched vulnerabilities, these incidents underline the growing sophistication and strategic intent behind modern cyberattacks. The recurring themes, third-party risk, delayed detection, weak patch management, and inadequate incident response, highlight the urgent need for a proactive, layered cybersecurity approach. Organizations must prioritize rapid vulnerability remediation, continuous monitoring, and robust supply-chain security to reduce cyberattack.
Cybersecurity is no longer just an IT responsibility; it is a core business resilience function that directly impacts revenue, brand reputation, regulatory standing, and customer confidence. Organizations that continue to treat security as a reactive cost center will find themselves increasingly exposed to operational paralysis and long-term reputational damage.
Looking ahead, organizations will define resilience by speed and intelligence, how quickly they identify vulnerabilities, how effectively they prioritize risks, and how decisively they execute response actions. The integration of automation, AI-driven threat detection, and continuous compliance monitoring will become essential pillars of modern security strategies.
FAQs
- How are attackers exploiting supply-chain vulnerabilities?
Many breaches originated from third-party service providers or software dependencies. Attackers target weaker links in the supply chain to gain access to larger networks, steal sensitive data, or deploy malware across multiple organizations.
- What are 90% of cyber attacks?
90% of Cyber Attacks are Human Error.









Leave a comment
Your email address will not be published. Required fields are marked *