Even mature engineering teams often treat threat modeling as an optional exercise, relying instead on VAPT or other post-development assessments with the assumption that “we’ll fix issues later.” But this approach is risky and reactive. Threat modeling is fundamentally proactive: it compels teams to analyze data flows, trust boundaries, attack surfaces, and potential adversary actions before a single line of code is written.
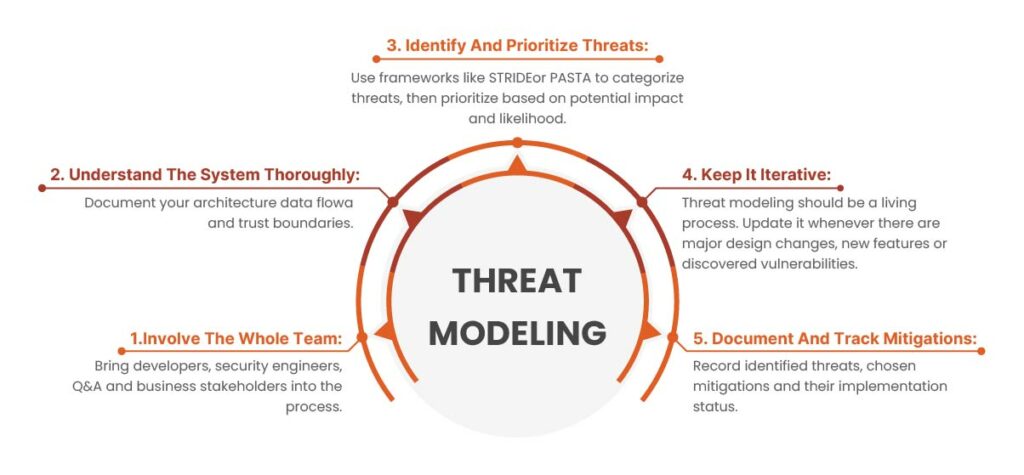
Skipping it leaves hidden design flaws, insecure assumptions, and architectural gaps buried deep in the system, forming long-term “security debt” that later testing may never uncover. SecurityCompass emphasizes that early threat modeling significantly reduces this debt by catching structural weaknesses early, preventing costly last-minute redesigns. Without this mindset, even comprehensive penetration testing can create a dangerous illusion of security, while systemic flaws remain completely unaddressed.
Table of Contents
Threat Modeling vs VAPT
Threat modeling is often compared to Vulnerability Assessment and Penetration Testing (VAPT testing), but it’s neither a subset nor a replacement of those activities. Instead, the three form a layered defense strategy. Vulnerability Assessment (VA) and Penetration Testing (PT) (collectively VAPT) focus on finding and exploiting security flaws in deployed systems. They are largely reactive: a vulnerability scan or pen test inspects an existing application or network for known weaknesses and attempts to exploit them. In contrast, threat modeling is proactive. It anticipates potential threats and design flaws before deployment.
Scope:
Threat modeling examines architecture and design from the ground up, while VA/PT examines compiled code and live systems. In practice, threat modeling typically occurs in early SDLC stages, whereas VAPT is performed on a staging or production environment prior to release.
Output:
A threat model identifies classes of threats and prescribes design changes or controls. VAPT reports list specific vulnerabilities (e.g. a SQL injection in this query string) and fix recommendations.
Overlap
Threat modeling can guide VAPT by highlighting the most critical components and likely attack paths. Conversely, VAPT results can validate a threat model by confirming which threats were valid and unaddressed.
In short, VAPT testing does not replace threat modeling – and vice versa. The two approaches complement each other. A strong security program includes both. Threat modeling equips a team to ask better questions during VAPT (e.g., “Have we fully defended this data flow?”), and VAPT helps validate that threat mitigations were correctly implemented.
Get in!
Join our weekly newsletter and stay updated
Industry Breaches
Recent breaches across various industries underscore the consequences of skipping threat modeling.
Fintech/Crypto
In early 2025, a cryptocurrency exchange lost $1.5B when attackers hijacked a multisig signing process. The flaw wasn’t a simple coding bug but an operational design issue: signers unknowingly approved malicious transactions.
A thorough threat model during design would have flagged missing verification steps and device segregation, preventing the attack. Similarly, fintech firms felt the impact of a May 2024 LockBit ransomware attack on Evolve Bank & Trust: 7.6 million customers’ records were compromised when an employee clicked a phishing link. A threat model here would enforce strict network segmentation and multi-factor authentication around high-value systems, greatly limiting what a single phishing click could do. In short, these scenarios show that design failures (not just code bugs) can trigger mega-breaches in financial services.
Healthcare
Healthcare has become a prime target. For example, the 2024 breach of Ascension (a major US health system) exposed nearly 5.6 million patient records. Attackers move laterally through networked medical devices and EHR systems – weaknesses that a threat model can uncover ahead of time. Comparitech data show healthcare ransomware jumped ~30% in 2025, often via vendor/supply-chain paths. Threat modeling in healthcare IT and MedTech would analyze those complex data flows (from IoT devices to cloud EHRs) and highlight needed controls. (Indeed, regulatory standards like HIPAA implicitly require this kind of risk assessment.) In practice, modeling could force encrypting critical data flows or segmenting networks, stopping many of these attacks before they start.
SaaS/Cloud
Cloud applications and SaaS platforms are beloved by businesses – and by hackers. A 2024 campaign (UNC5537) targeted Snowflake customers: attackers used stolen credentials and weak identity controls to exfiltrate data from hundreds of customer databases. A missed threat here was inadequate identity/credential safeguards: the Cloud Security Alliance notes that “insufficient identity, credentials, key, and access management” enabled the breach.
A threat model would have flagged the need for multi-factor authentication, credential rotation, and strict audit logging on sensitive SaaS accounts. In another case, Cloudflare’s 2024 Atlassian breach stemmed from reused service tokens in their SaaS integrations – an oversight a security-minded architecture review could catch. These examples show that SaaS/data breaches often arise from design and configuration, not faulty code – exactly what threat modeling is meant to spot.
Manufacturing
Manufacturing’s IoT and OT networks are under relentless attack. In 2025, North America’s largest steelmaker, Nucor, detected unauthorized IT access and had to halt production as a precaution. Ingersoll Rand (industrial compressors) suffered a ransomware incident in 2023 that exfiltrated customer data. These breaches came via forgotten IoT devices and insufficient network segmentation. A threat model applied to an industrial control system would highlight critical trust boundaries (e.g., separating corporate networks from OT), unencrypted IoT protocols, and default credentials on legacy equipment – giving teams a chance to remediate before the attack. As Asimily notes, manufacturing accounts for 26% of all critical-infrastructure incidents. In practice, modeling OT/IIoT environments can force better access controls and micro-segmentation, shrinking the blast radius of inevitable breach attempts.
Book Your Free Cybersecurity Consultation Today!
Embading Threat Modeling in Your SDLC
Threat modeling, when embedded early in the SDLC, enables proactive risk management by identifying potential vulnerabilities, deriving clear security requirements, and uncovering design flaws before development progresses. It helps prioritise security issues based on risk exposure, shapes targeted security testing through use- and abuse-case scenarios, and supports informed decision-making before an application’s release by validating mitigation of high-risk threats. Even after deployment or an incident, threat modeling guides additional countermeasures and continuously reassesses emerging risks during future releases or change management, ensuring sustained and adaptive application security throughout its lifecycle.
How Kratikal Can Help You in Threat Modeling?
Kratikal’s threat modeling service empowers organisations to anticipate and mitigate security risks by thinking like an attacker. Using a structured methodology, including creating data flow diagrams and applying the STRIDE framework, Kratikal maps potential threats, evaluates their impact, and identifies key vulnerabilities. Their approach also aligns threats with the MITRE ATT&CK framework, helping clients prioritise risk and design effective security controls. Finally, Kratikal delivers actionable recommendations and supports their implementation, enabling companies to build secure systems right from the design phase and continuously validate them as their architecture evolves.
FAQs
- What is threat modeling in SDLC?
Threat modeling in the SDLC is a forward-looking approach that uncovers, analyses, and addresses potential security threats and vulnerabilities throughout the entire software development lifecycle.
- What is the difference between risk assessment and threat modeling?
A risk assessment evaluates potential countermeasures, while threat modeling goes a step further by defining and applying them. It uncovers vulnerabilities, identifies risks, and outlines mitigation strategies using scenarios that focus on system entry points and the flow of data, whether stored or in transit.









Leave a comment
Your email address will not be published. Required fields are marked *