As mobile technology becomes more integrated into our daily lives, mobile app security testing is more essential than ever. With 6.92 billion smartphone users worldwide—about 85% of the global population—mobile devices are everywhere. The app market is now saturated with nearly five million apps, making competition fierce. Notably, 71% of users uninstall apps due to crashes, highlighting the importance of thorough testing.
To ensure apps meet high standards of quality, performance, and usability, they must be rigorously tested across various devices, platforms, and operating systems. This helps identify vulnerabilities, optimize functionality, and deliver a seamless user experience.
For CTOs, investing in a comprehensive mobile app security testing strategy not only ensures software reliability but also minimizes risk, supports regulatory compliance, and drives better business outcomes. Early detection of issues also reduces production-level bugs, speeds up time to market, and improves resource planning through data-driven insights.
Table of Contents
Some Key Insights of Mobile Application Security Market
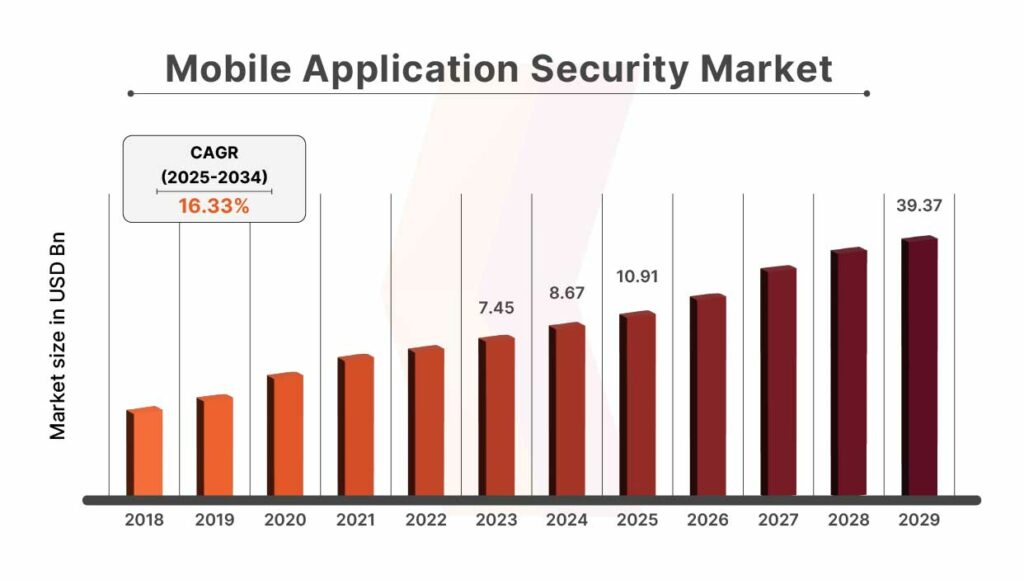
The Mobile Application Security Market has shown consistent growth over the years and is projected to expand significantly in the coming decade. With a market size of $10.91 billion expected by 2025, it is forecasted to reach $39.37 billion by 2034, growing at a CAGR of 16.33% between 2025 and 2034. This sharp rise reflects the increasing demand for mobile security solutions as mobile apps continue to dominate the digital landscape and cyber threats evolve rapidly.
Common Vulnerabilities Found in Mobile App Security Testing
E-commerce apps face many of the same weaknesses as other mobile software. Key vulnerabilities to watch for include:
Insecure Data Storage
Sensitive data (user credentials, payment tokens, personal information) improperly stored on the device can be stolen if the phone is compromised. Research warns that storing data without strong encryption or secure platform storage (e.g. Android Keystore or iOS Keychain) invites intrusion and massive data leaks.
Reverse Engineering and Tampering:
Attackers can unpack or decompile app binaries to discover secrets or insert malware. Without code obfuscation and binary hardening, apps are vulnerable to reverse-engineering (especially on Android) which lets attackers bypass protections.
Weak Authentication/Authorization:
Weak login mechanisms or improper session management can allow attackers to hijack user identities. Flaws in authentication logic and missing authorization checks often lead to privilege escalation or user impersonation.
Insecure Communication:
Failing to encrypt network traffic leaves data exposed in transit. If an app sends data in plaintext or with weak TLS configuration, attackers on the same network can sniff or manipulate the data. Mobile apps must enforce strong TLS, SSL certificate pinning, and protect against man-in-the-middle attacks.
Aside from these, mobile-specific threats—such as malware or ransomware on user devices, and malicious apps distributed through untrusted app stores—also pose significant risks. However, the root cause of many of these threats often links back to core vulnerabilities that can be identified and mitigated through comprehensive mobile app security testing. Overall, eCommerce CTOs should operate under the assumption that all apps contain flaws: one study found that 83% of mobile apps had at least one security issue at initial assessment.
Get in!
Join our weekly newsletter and stay updated
Best Practices For Mobile App Security Testing
E-commerce CTOs should build security throughout the app lifecycle, not just at the end. Key best practices include:

Compherensive API Security Validation:
Since mobile applications are merely front-ends to powerful backend APIs, securing these APIs is critical. Perform fuzz testing and endpoint enumeration to identify weaknesses like broken object-level authorization (BOLA), excessive data exposure, or insecure deserialization. Also, verify that token-based authentication mechanisms (e.g., OAuth 2.0, JWT) are correctly implemented and rotated. Enforce rate-limiting, API gateways, and WAF rules to reduce surface area for attacks.
OWASP Top 10 Risk Coverage
The OWASP Mobile Top 10 provides a structured framework to assess common mobile threats such as insecure storage (M1), poor cryptographic implementation (M5), or code tampering (M9). Security tests should be mapped to these risks, ensuring coverage across categories like code, data, platform, and interaction layers.
TLS/SSL Certificates Validation
Misconfigured or weak TLS implementations open the door to MITM attacks. Validate the implementation of TLS 1.2 or higher, disable weak ciphers, and ensure proper server certificate validation. Certificate pinning (hardcoding or dynamic) adds another layer of trust by binding the app to a known certificate or public key.
Static and Dynamic Code Analysis
SAST parses the mobile app’s source or binary code to uncover vulnerabilities such as insecure data storage, improper use of cryptographic APIs, or insecure logging. DAST tools analyze the running application for flaws in session handling, authentication, and data exposure during communication. Combined, these approaches offer in-depth coverage across both code-level and runtime vulnerabilities. CTOs should mandate periodic scans and baseline thresholds for security scores as part of quality gates.
Book Your Free Cybersecurity Consultation Today!
Actionable Takeaways for E-commerce CTOs
To build secure and resilient eCommerce platforms, CTOs must prioritize mobile app security from the outset—incorporating threat modeling, adopting standards like OWASP MASVS, integrating automated SAST/DAST scans into CI/CD, and combining tool-based testing with expert audits. Ensuring end-to-end encryption, maintaining compliance with regulations like GDPR and PCI, staying current with CVEs, and fostering a security-aware development culture are essential. Ultimately, mobile app security testing should be continuous and proactive, aiming not just for compliance, but for earning and retaining customer trust.
FAQs
- What is the role of APIs in mobile app security testing?
Mobile apps rely heavily on backend APIs for data and functionality. Testing APIs is crucial to detect issues such as broken object-level authorization (BOLA), insecure data exposure, token mismanagement, and input validation flaws. Weak APIs can undermine an otherwise secure mobile front-end.
- How can CTOs ensure secure communication in mobile apps?
Ensure all data in transit is encrypted using TLS 1.2 or higher. Implement SSL certificate validation and use certificate pinning to protect against MITM (man-in-the-middle) attacks. Avoid sending sensitive data in plaintext or via insecure channels.









Leave a comment
Your email address will not be published. Required fields are marked *