Concerned about the vulnerability of WordPress plugins jeopardizing your website’s security? Did you know? Vulnerable plugins are the primary cause of WordPress site hacks, accounting for 55.9% of attacks. But should you stop using plugins altogether? In website development, it’s challenging to operate a WordPress site without plugins, as they enhance functionality and features.
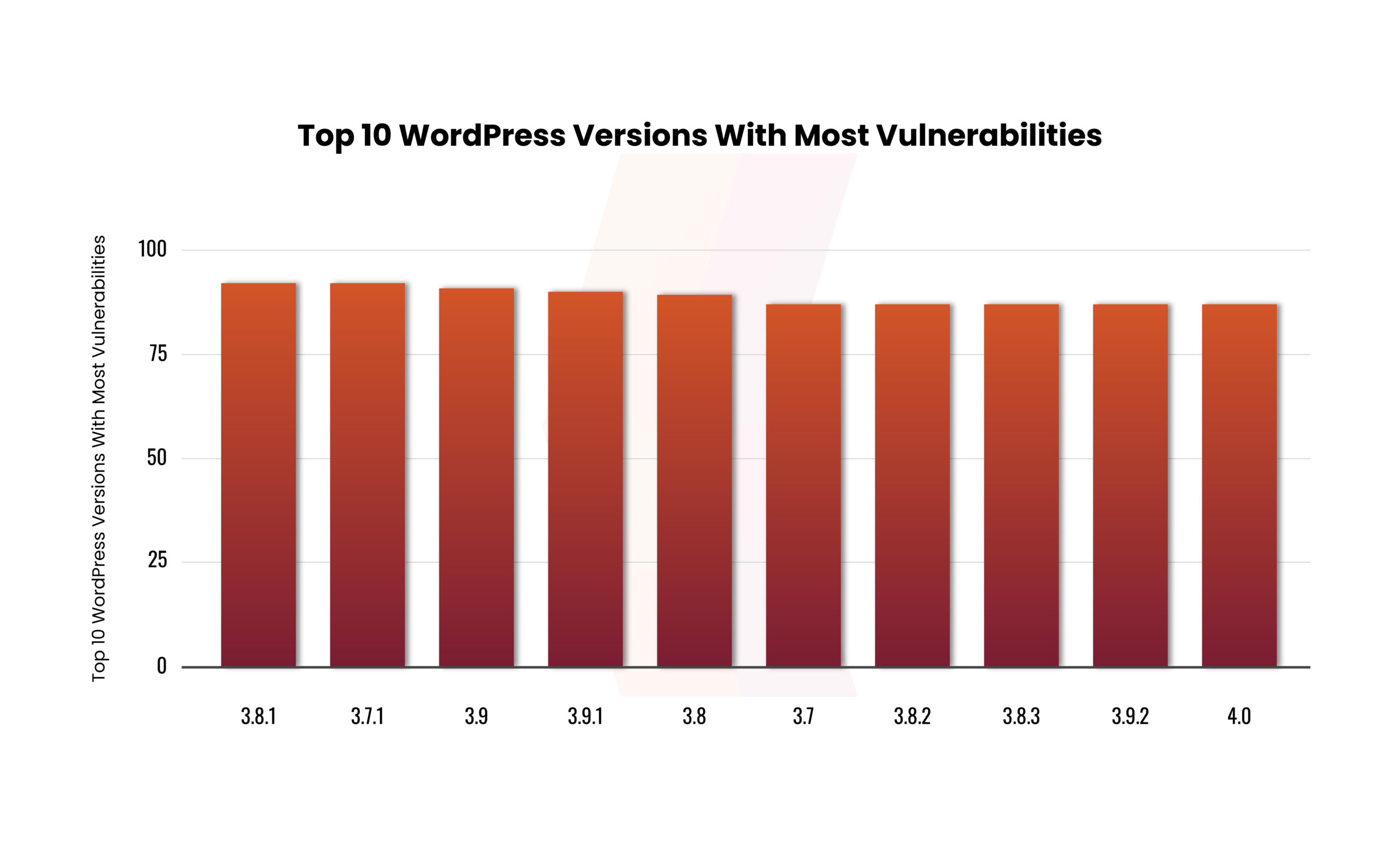
The following graph showcases the top 10 WordPress core versions most susceptible to vulnerabilities, with versions 3.7.1 and 3.8.1 at the forefront, each boasting 92 vulnerabilities. Coming in second is WordPress version 3.9, with 91 vulnerabilities.
Thankfully, there’s a way to utilize plugins while safeguarding your site. When plugin developers detect vulnerabilities, they promptly address them by releasing updated versions. Once you update the plugin on your site, it becomes secure for use. Unfortunately, many WordPress users postpone updates, leaving their sites open to hackers. A hacked site can be exploited for various malicious activities, including data theft, unauthorized ads, and website defacement. Such breaches can have severe consequences for your business, leading to account suspension, and loss of visitors, customers, and revenue. That’s why understanding vulnerable plugins and their security issues is crucial. In this blog, highlight the most recent incident that happened in MiniOrange plugins via WordPress and the impact on organizations and businesses.
Table of Contents
Which Organizations mostly use Plugins?
In the dynamic landscape of online presence, WordPress emerges as a powerhouse for a multitude of industries seeking to establish and enhance their digital footprint. From personal blogs to e-commerce ventures, and photography portfolios to agency websites encompassing design, news, marketing, and law firms. WordPress offers a user-friendly platform that caters to diverse needs.
Industries such as hotels and restaurants, consultants, and freelancers also find immense value in harnessing the capabilities of WordPress for their online endeavors. The flexibility of WordPress shines through with its extensive array of themes and plugins, both free and premium, enabling users to customize their websites with ease.
With its intuitive interface and robust features, WordPress serves as a compelling tool for showcasing skills, products, services, and achievements across various sectors. Whether you are a budding entrepreneur looking to launch an e-commerce store or a seasoned consultant aiming to bolster your online presence, WordPress stands out as a versatile solution that empowers businesses and individuals alike to craft engaging and impactful websites.
Embrace the power of WordPress to unlock endless possibilities for your online presence and propel your brand toward digital success across diverse industries.
Get in!
Join our weekly newsletter and stay updated
How can your WordPress Plugin be Vulnerable?
It’s essential to understand that WordPress plugins are developed by third-party developers, not the WordPress team. While most plugins are accessible in the WordPress repository, they can also be found in popular marketplaces like CodeCanyon or on the plugin’s website.
With over 50,000 WordPress plugins currently available and new ones being created daily, developers diligently manage and maintain their plugins to ensure security, particularly for premium offerings. These plugins adhere to specific guidelines to guarantee user safety and security. However, developers continually strive to improve their products and may face time constraints when releasing new features.
Once hackers identify a vulnerability, they can exploit it to execute various hacks, including redirecting visitors to unknown sites, injecting spam ads and content onto your site, installing malware such as wp-feed.php malware, creating rogue admin accounts, and utilizing your server resources to launch DDoS attacks and send spam emails. Such hack attacks can significantly degrade your site’s performance, negatively impacting your SEO rankings and posing risks to your business, revenue, and reputation. Given that vulnerable plugins are the primary root cause of most website hacks, it’s crucial to identify which plugins are most susceptible and understand the available fixes.
Book Your Free Cybersecurity Consultation Today!
What Happened at MiniOrange?
In a recent security alert, WordPress administrators are strongly advised to take immediate action and remove miniOrange plugins from their websites due to a critical flaw that poses a severe risk to site security. The vulnerability, identified as CVE-2024-2172, has been rated 9.8 out of 10 on the CVSS scoring system, highlighting its critical nature. This flaw impacts specific versions of the Malware Scanner and Web Application Firewall plugins, prompting the urgent need for their deletion. The security risk arises from a missing capability check in the function mo_wpns_init(), which could allow unauthenticated attackers to manipulate user passwords and escalate their privileges to that of an administrator.
Once attackers gain administrative access, they could have compromised the entire site by uploading malicious files, modifying content, and redirecting users to harmful sites. Notably, the maintainers of these plugins have permanently closed them as of March 7, 2024, emphasizing the seriousness of the situation. With over 10,000 active installs of Malware Scanner and more than 300 active installations of Web Application Firewall, the scale of potential risk is significant. This urgent call to action underscores the critical importance of promptly addressing security vulnerabilities to protect WordPress websites from exploitation and maintain a secure online environment. Stay vigilant, prioritize security measures, and act swiftly to safeguard your WordPress site from potential compromises.
Implications for Businesses + Organizations
The recent incident highlights the urgent need to promptly resolve vulnerabilities in WordPress plugins. Given the vast array of plugins in use, website owners must maintain vigilance and take proactive steps to enhance security. Consistently updating plugins, performing security assessments, and swiftly uninstalling discontinued or vulnerable plugins are crucial measures to protect WordPress websites from potential attacks.
Conclusion
The recent security incident in miniOrange plugins underscores the critical importance of promptly addressing vulnerabilities in WordPress plugins. With the prevalence of vulnerable plugins posing significant risks to website security, WordPress administrators must remain vigilant and proactive in implementing security measures. Regular updates, security assessments, and timely removal of discontinued or vulnerable plugins are essential steps to safeguard WordPress websites from potential attacks. By prioritizing security and taking swift action, website owners can mitigate risks and maintain a secure online environment for their businesses and organizations.
Kratikal, a CERT-In-empanelled auditor offers comprehensive cybersecurity services to secure your IT infrastructure. In addition to assuring security through our services such as Web Application Security Testing, Network Security Testing, IoT Testing, and others, our team of experts ensures to provide businesses with a variety of VAPT services as per the company’s requirements. Kratikal protects businesses from online attacks and help them fix flaws, as well as comply with standard and regulatory compliances.
Watch our video to learn more about the flaws in miniOrange plugins
FAQs
- Q1: What is a critical error on the WordPress plugin page?
Ans: The critical error in WordPress can stem from various causes, but it typically originates from a problem with PHP. This may include surpassing your memory limit or encountering an error in your code, plugins, or theme.
- Q2: How to disable critical error emails in WordPress?
Ans: Typically, when a fatal error occurs on a WordPress website, it automatically sends an email notification to administrators. If you wish to disable these email notifications for any reason, you can add the following line of code to the wp-config.php file: define( ‘WP_DISABLE_FATAL_ERROR_HANDLER’, true );









Leave a comment
Your email address will not be published. Required fields are marked *