Are you aware that CVE-2023-22527, a serious vulnerability, has affected Atlassian Confluence servers? Users of Atlassian products such as Jira, Confluence, Bitbucket, and the macOS Companion app are urgently advised to update their software promptly, as four critical vulnerabilities have been identified, posing a serious risk of remote code execution (RCE). Based on the past exploitation examples using Jira and Confluence vulnerabilities, the Australian Cyber Security Centre asserts that there is a greater chance of exploitation for the vulnerabilities that were made public last week. They are “much more likely than not” to be the focus of malicious campaigns.
Table of Contents
What is CVE-2023-22527 Vulnerability?
A security researcher at Atlassian discovered a template injection vulnerability. This confluence data center and server vulnerability was found to allow an unauthorized attacker to take total control of the impacted remote instance. It has been marked critical which is an object graph navigation language injection.
OGNL is employed in Atlassian application which is a Java-based expression language. An adversary can send a specially crafted ONGL expression in the user interface that leads to remote code execution.
Book Your Free Cybersecurity Consultation Today!
What Happened in Atlassian?
Attackers quickly took advantage of a critical security CVE-2023-22527 that was just three days ago. This affected the Atlassian Confluence Data Center and Server. Highly critical vulnerability (CVSS score: 10.0) exploits outdated software, allowing unauthenticated attackers remote code execution. The impacted Confluence versions include those released before December 5, 2023, and version 8.4.5. Within days of disclosure, security observers noted over 40,000 exploitation attempts from 600 unique global IP addresses, primarily focusing on testing callback attempts and executing ‘whoami’.
On January 21st, 2024, more than 11,000 Atlassian instances were available online, while it is yet unknown which particular variant is susceptible to CVE-2023-22527. Security experts stress on how serious the flaw is, emphasizing how it might allow attackers to insert malicious code and carry out arbitrary commands on compromised systems.
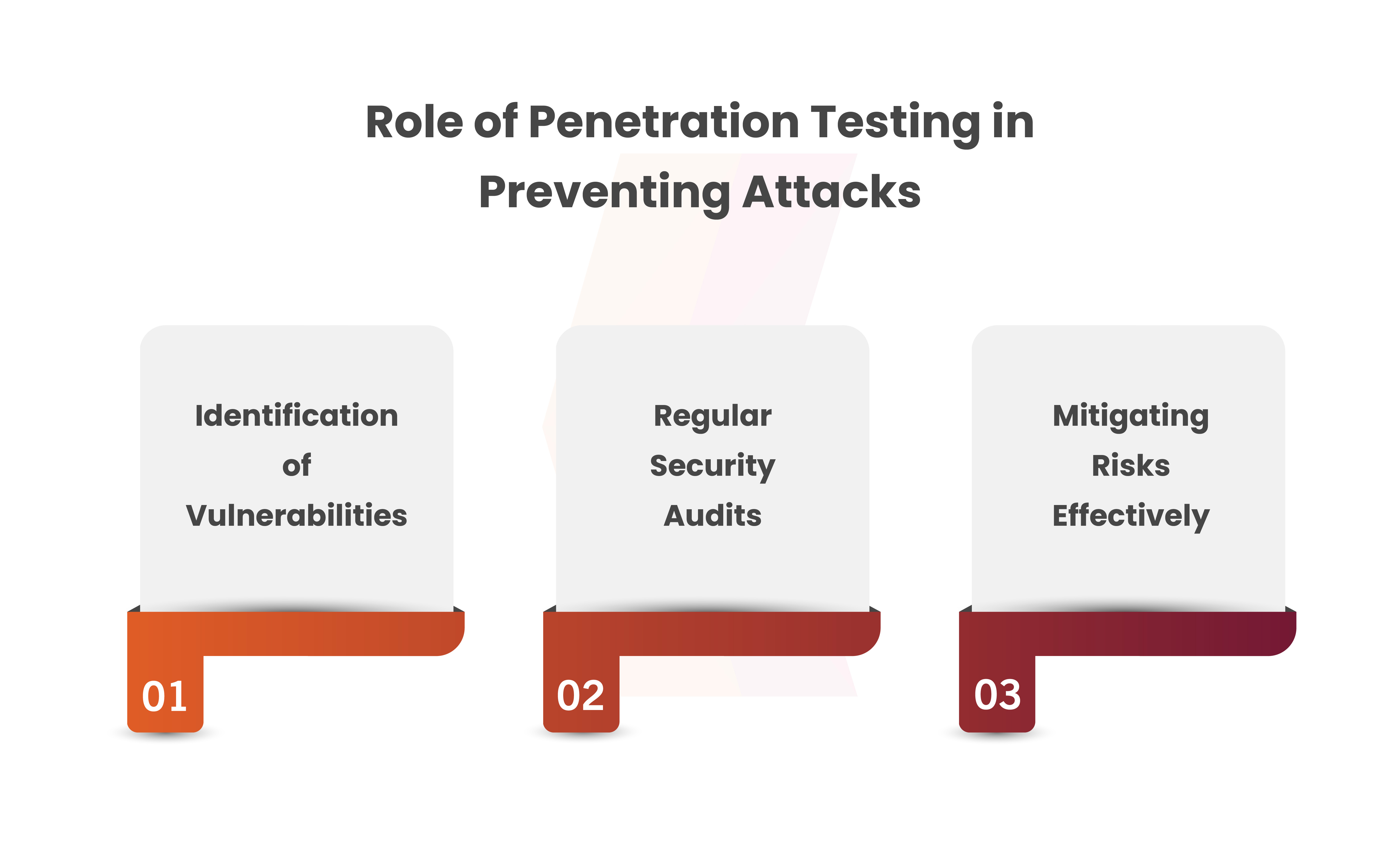
Role of Penetration Testing in Preventing Such Attacks
Identification of Vulnerabilities
Through penetration testing, organizations can proactively identify vulnerabilities of their networks, programs, and systems. Comprehensive assessments that include injection vulnerabilities like CVE-2023-22527, companies can protect their digital assets from possible threats.
Regular Security Audits
The Confluence incident highlights the importance of regular security audits and updates. Regularly updating Atlassian software should protect customers from the mentioned security flaw, as per Atlassian’s security advisory. Penetration testing ensures that these routine audits are comprehensive and effective, leaving no room for oversight.
Mitigating Risks Effectively
By adopting penetration testing practices, organizations can assess their security posture continuously. They may find and fix the flaws with this proactive strategy, thereby reducing risks. Penetration testing should have likely discovered and fixed CVE-2023-22527 before it became a significant risk.
Why is Software Industry Prone to Cyber Attacks?
The increasing proliferation of Internet-connected devices, with 328 million new additions each month, has intensified competition among software providers. This has resulted in the premature release of applications, driven either by a rush to market or opportunistic developers lacking mature software development and secure coding skills, as highlighted by Property Update. The rising demand for interconnectivity and platform compatibility has made software more complex, leading to vulnerabilities.
ENISA notes that the prevalent use of open-source software components, accounting for 80-90% of modern applications, exacerbates the security problem. Despite organizations improving their ability to identify vulnerabilities, there is a simultaneous increase in cyber attackers seeking and exploiting these vulnerabilities. Furthermore, because of supervision or cost-cutting initiatives, antiquated system architectures continue to exist, leaving them vulnerable to cyberattacks. The whole situation emphasizes how important it is to have strong cybersecurity procedures in place in order to identify weaknesses.
Get in!
Join our weekly newsletter and stay updated
Conclusion
CVE-2023-22527 vulnerability exploit in Atlassian Confluence servers emphasizes the need for strong cybersecurity defenses. Various attacks, with over 40,000 exploitation tries in only three days, underscore the gravity of the situation and the doubtlessly catastrophic outcomes for corporations. The speed at which hackers exploit CVE-2023-22527 demonstrates how dynamic and constantly evolving cyberattacks are.
It is becoming more and more essential for organizations to conduct security audits, enforce secure coding strategies, and continue to be alert to cyberattacks as the software industry encounters growing complexity and competition. It ensures that systems are secure, highlighting the significance of having a comprehensive cybersecurity plan in order to prevent cyberattacks.
Kratikal is a CERT-In empanelled auditor with the ability to improve risk awareness. Our VAPT services, encompassing both manual and automated approaches, professionally identify, detect, and evaluate vulnerabilities present in your IT infrastructure. Furthermore, Kratikal offers extensive security auditing services to verify compliance with a range of regulations such as ISO/IEC 27001, GDPR, PCI DSS, and others. This helps your business meet legal requirements established by various governments.
Ref: https://thehackernews.com/2024/01/40000-attacks-in-3-days-critical.html








Leave a comment
Your email address will not be published. Required fields are marked *