Let’s start with a reality check: “Pentest” only helps if it’s timely, repeated, and connected to remediation. A beautifully written penetration test report that arrives once a year, gets filed away, and never gets retested is basically a fancy screenshot of yesterday’s risk.
Classic penetration testing is well-described in well-accepted guidance like plan, discover, attack (confirm exploitability), and report, while explicitly distinguishing “scanner says it might exist” from “tester proved it’s exploitable.”
Table of Contents
What’s The Buzz Around The Pentest Model: Penetration Testing as a Service (PTaaS)
Penetration Testing as a Service (PTaaS) is not a new kind. It’s a delivery model: human-led testing plus a software platform that makes the work continuous, collaborative, and easy to retest. Vendors define PTaaS as combining expert manual testing with a modern platform to support ongoing programs and integrations. Retesting is a core mechanic in that model. For e.g., platform workflows that let you request targeted retests of specific findings or all open findings after fixes land.
People oversell pentest or PTaaS when they imply it would have “stopped” every famous breach. It won’t. PTaaS cannot retroactively patch a vendor’s zero-day. It can’t force MFA onto a neglected VPN. It can’t guarantee your build pipeline won’t be infiltrated by a nation-state.
What it can do is brutally practical: find exploitable paths earlier, validate fixes faster, and keep your attack surface from drifting out of reality, which is exactly where many “major breaches” are born.
Book Your Free Cybersecurity Consultation Today!
What Makes PTaaS Important?
Two context stats make the “timing” problem obvious. The Cost of a Data Breach Report put average breach cost at $4.44 million globally, with lost business and response costs as major drivers. And the DBIR shows how dominant modern intrusion patterns have become. Ransomware is tied to a large share of “system intrusion” breaches, and exploitation of edge systems keeps climbing.
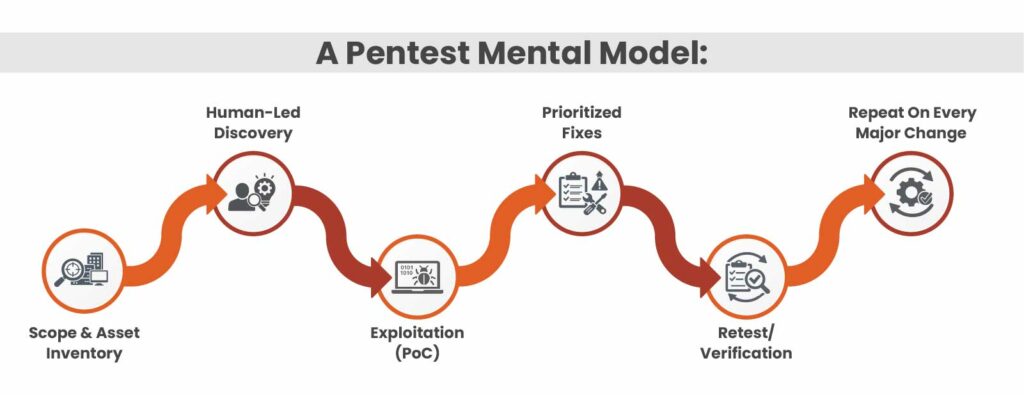
Scope & asset inventory → Human-led discovery → Exploitation (PoC) → Prioritized fixes → Retest/verification → Repeat on every major change
That loop is what the following breach stories keep screaming for.
7 Cyber Breaches Pentest Could Have Prevented
The incidents below were selected because
- Authoritative primary reporting exists (official disclosures, regulator documents, government advisories, and SEC filings),
- The exploited weakness is specific enough to map to testing methodologies, and
- The impact is measurable via records, operational disruption, or documented financial/regulatory consequences.
Sources used include: U.S. government materials (e.g., FTC, DOJ, FBI/CISA advisories), UK regulatory penalty notices, public SEC filings, and first-party incident pages and disclosures from affected organizations.
Breach 1:
Affected Organization: Equifax
Attack Type: Unpatched web app RCE (CVE-2017-5638), web shells, credential pivot.Unpatched web app RCE (CVE-2017-5638), web shells, credential pivot.
Impact: 47M people affected; settlement ≥$575M up to $700M.
How Pentest Could Have Helped: Continuous discovery + exploit validation + enforced retesting after patching; stop treating “scan” as “fixed.”
Breach 2:
Affected Organization: Marriott/Starwood
Attack Type: Long-term compromise; data exported from the reservation DB; detection lag.
Impact: 383M records upper limit; UK fine £18.4M; U.S. multistate settlement $52M
How Pentest Could Have Helped: PTaaS-driven M&A due diligence; recurring “crown jewel” testing and retesting to uncover persistent access paths pre- and post-integration.
Breach 3:
Affected Organization: Capital One
Attack Type: Misconfigured WAF enabled access to sensitive data (cloud-hosted).
Impact: ~106M individuals; est. $100–$150M incremental costs.
How Pentest Could Have Helped: Cloud-aware PTaaS: WAF validation, SSRF-style testing, IAM privilege escalation simulation, rapid retest after config fixes.
Breach 4:
Affected Organization: SolarWinds Orion
Attack Type: Build pipeline supply-chain compromise; trojaned updates distributed Mar–Jun 2020.
Impact: Up to ~18k potentially vulnerable customer downloads; $26M settlement (investor litigation).
How Pentest Could Have Helped: PTaaS pointed at CI/CD and build security: continuous testing of signing, secrets, and “can we ship tampered code?” workflows.
Breach 5:
Affected Organization: Colonial Pipeline
Attack Type: Ransomware via an exploited legacy VPN profile; single password theft reported.
Impact: Operational shutdown across 5,500 miles; ransom 75 BTC; DOJ seized 63.7 BTC ($2.3M).
How Pentest Could Have Helped: Continuous external access testing: stale VPN profiles/accounts, password spraying checks, MFA enforcement validation, and retesting after hardening.
Breach 6:
Affected Organization: Microsoft Exchange Mass Exploitation
Attack Type: Zero-day chain (incl. SSRF), followed by web shells and follow-on exploitation.
Impact: >20k U.S. orgs compromised reported; thousands of servers affected in telemetry.
How Pentest Could Have Helped: PTaaS mitigates (not prevents) zero-days: continuous exposure discovery, patch verification retests, segmentation validation, and compromise-assumption exercises.
Breach 7:
Affected Organization: MOVEit Exploitation Wave
Attack Type: Zero-day SQL injection (CVE-2023-34362); LEMURLOOT web shell; data theft.
Impact: Maximus 8–11M individuals; ~$15M expense estimate; broader estimates: 2,600+ orgs; ~$15B total cost (estimate).
How Pentest Could Have Helped: Vendor-side PTaaS to catch injection flaws earlier; customer-side PTaaS to keep exposed instances inventoried and fixes verified via retesting.
A PTaaS Playbook that Matches Real Failure Modes
If you look across these seven breaches, the lesson is not “everyone should buy PTaaS.” The lesson is: most organizations fail at the same three loops: asset reality, exploit proof, and fix verification. PTaaS is valuable because it can industrialize those loops.
Treat these as non-negotiables:
- First, asset truth beats asset hope. The MOVEit and Exchange waves spread fast because anything internet-facing becomes a race condition. A PTaaS program should begin every cycle with discovery and inventory
- Second, proof beats severity scores. NIST explicitly notes that scanners only indicate possible existence; the “attack” phase confirms exploitability. That difference is the gap between “we had a CVE on a dashboard” and “we demonstrated RCE on your production dispute portal.”
- Third, retesting is the bridge between security and engineering. Many breaches aren’t caused by ignorance; they’re caused by unfinished remediation. Retesting turns “we think it’s fixed” into “it’s verifiably closed,” and it creates accountability for the exact exploit path that mattered.
Get in!
Join our weekly newsletter and stay updated
Finally, be precise about where PTaaS belongs. Equifax and Capital One are “customer-side PTaaS should catch this.” SolarWinds and MOVEit are “vendor-side PTaaS should catch this, customer-side PTaaS should reduce exposure and validate patching.” Colonial Pipeline is “PTaaS should continuously pressure-test your gates like VPN, identity, and access, because attackers only need one neglected door.”
FAQs
- Can pentest or PTaaS really prevent major cyber breaches?
Pentest and PTaaS cannot stop every breach, especially zero-day or nation-state attacks. However, continuous pentesting through PTaaS can identify exploitable paths early, validate patches, and prevent common failure points, exactly the gaps seen in breaches like Equifax, Capital One, and MOVEit.
- Why is retesting critical in modern pentest and PTaaS programs?
Most breaches happen due to unfinished or unverified remediation. Retesting, a core to PTaaS, confirms that vulnerabilities are actually closed, not just marked “fixed” in reports, bridging the gap between security findings and real-world risk reduction.









Leave a comment
Your email address will not be published. Required fields are marked *