Vulnerabilities are the anomalies, such as programming errors or configuration issues, of the IT infrastructure. Attackers exploit the weaknesses in the infrastructure and can, in turn, disrupt the digital assets. If these vulnerabilities are exploited, then it can result in the compromise of the confidentiality, integrity as well and availability of resources that belong to the organization.
Table of Contents
What is a Vulnerability Assessment?
Vulnerability assessment is the risk management process that defines, identifies, classifies, and prioritizes vulnerabilities within computer systems, applications, and network infrastructures. This helps the organization in conducting the assessment with the required knowledge, awareness, and risk posture for understanding the cyber threats. Vulnerability assessment is conducted in two ways.
Importance of Vulnerability Assessment
Security vulnerabilities typically stem from either technological flaws or human behavior.
Data breaches can result from employees accidentally sharing sensitive information or from malicious insiders leaking it intentionally. Lost or stolen devices, especially those lacking encryption, also present a significant risk by potentially exposing critical data and providing entry points into corporate networks. Additionally, attackers often deploy malware to steal information or gain control of their infrastructure.
To reduce these risks, organizations must adopt a robust vulnerability management strategy—an ongoing process that involves routine vulnerability assessments. These assessments help security teams detect, analyze, prioritize, report, and fix weaknesses across operating systems, business applications, endpoints, and browsers.
Each year, thousands of new vulnerabilities are discovered, necessitating constant updates and adjustments to maintain strong security postures. However, many organizations lack efficient patch management processes and fail to apply critical updates in time, leaving their IT infrastructure exposed.
Since it’s not feasible to patch every vulnerability immediately, a strong vulnerability management program focuses on identifying and prioritizing high-risk threats. This ensures that the most critical issues are addressed first, helping organizations stay ahead of potential breaches through regular monitoring and remediation.
Book Your Free Cybersecurity Consultation Today!
Types of Vulnerability Assessment
Automated Testing
Automated tools like vulnerability scanners are used to identify security weaknesses in applications. They detect common vulnerabilities such as SQL Injection, Command Injection, Path Traversal, and Cross-Site Scripting. These tools are a key component of Dynamic Application Security Testing (DAST), helping to uncover malicious code, hidden backdoors, and other threats within software and applications.
Manual Testing
Pen testers are the experts that dive deep into the infrastructure that will help them in finding out the vulnerabilities that cyber attackers can exploit. The following are the types of vulnerability assessment and penetration testing:
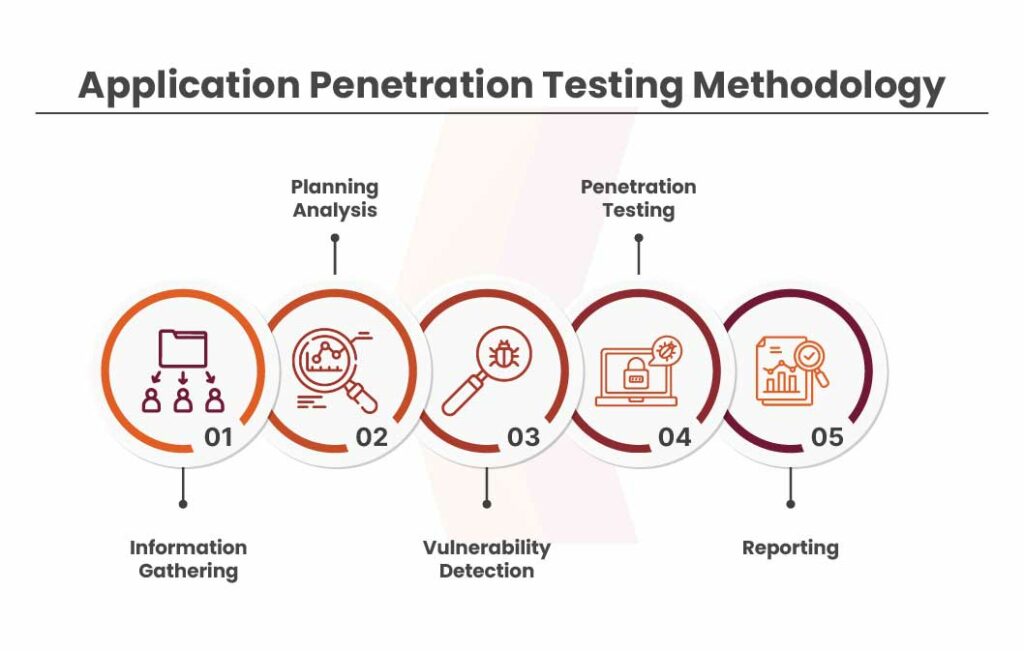
Different Types of Manual Testing
1. Application Security Testing
It is the process of testing and analyzing a mobile or web application. This methodology helps pen-testers in understanding the security posture of websites and applications.
The application security testing process includes:
- Password quality rules
- Brute force attack testing
- User authorization processes
- Session cookies
- SQL injection
2. Server Security Testing
Servers contain information including the source code of the application, configuration files, cryptographic keys as well as other important data. Pen testers perform an in-depth analysis of the server in server security testing. Based on this analysis, testers perform an approach to mimic real-time cyber attacks.
3. Infrastructure Penetration Testing
Infrastructure penetration testing is a proven method to evaluate the security of computing networks, infrastructure, as well as the weaknesses in applications by simulating a malicious cyber attack.
4. Cloud Security Testing
Every organization that keeps its platforms, customer data, applications, operating systems as well as networks over the cloud must perform cloud security testing. Cloud security is essential for assessing the security of the operating systems and applications that run on the cloud. This requires equipping cloud instances with defensive security controls and regular assessment of the ability to withstand cyber threats.
5. IoT Security Testing
With our increasing engagement with technology, we are becoming more advanced in incorporating technology with things that we use on a daily basis. Pen testers are aware of the complexities and how attackers exploit them.
IoT penetration testing considers the entire ecosystem of IoT technology. It covers each segment and analyses the security of the IoT devices. The testing services include IoT mobile applications, communication, protocols, cloud APIs, as well as embedded hardware and firmware.
Which is the Better Method of Vulnerability Assessment?
Manual vulnerability assessment is better than vulnerability scanning tools since automated tools often give false positives. This can seriously hamper the process of vulnerability assessment. Although automated tools make the assessment process faster and less labor-intensive, the tools are not capable of identifying vulnerabilities.
This can be far better done by observant pen testers who use systematic technology with years of experience. Manual vulnerability assessment requires time but it is far more effective and accurate than vulnerability scanning tools. The reason behind preferring manual assessment is the lack of an in-depth understanding of the system to discover vulnerabilities. Consulting a leading cybersecurity company and investing in their VAPT services can help in strengthening your organization’s security infrastructure.
Get in!
Join our weekly newsletter and stay updated
Conclusion
Vulnerability assessment plays a vital role in strengthening an organization’s cybersecurity posture by proactively identifying and addressing potential security gaps. While automated tools offer speed and scalability, manual assessments provide deeper insights and greater accuracy, especially when performed by skilled professionals. A balanced approach that leverages both automated scanning and expert-led manual testing ensures comprehensive protection against evolving cyber threats. Partnering with a trusted cybersecurity firm for VAPT services can empower organizations to stay resilient, compliant, and secure in today’s rapidly changing threat landscape.
FAQs
- What is the main goal of performing vulnerability assessment?
A vulnerability assessment is designed to identify weaknesses within a network and suggest suitable mitigation or remediation strategies to minimize or eliminate associated risks. It typically involves the use of automated network security scanning tools to detect these vulnerabilities.
- Why is vulnerability assessment important?
Vulnerability assessment is a systematic approach used by organizations to identify potential security weaknesses in their systems. It involves analyzing systems for known vulnerabilities, determining the severity of each issue, and providing recommendations on whether the threats should be mitigated or fully remediated.









Leave a comment
Your email address will not be published. Required fields are marked *