Cyberattack continued to climb worldwide in 2025. Organizations saw an average of roughly 1,900 – 2,000 attacks per week. Compared to 2024, it’s a mid-single-digit percentage increase. Certain regions experienced especially sharp growth. For example, Europe’s attack volume jumped ~22% year-over-year. Critical infrastructure remained a focal point; approximately 70% of all incidents involved organizations in critical sectors like energy, manufacturing, finance, transportation, healthcare, etc., as per IBM.
Table of Contents
Top Sectors Under Cyberattack in 2025
Below, we break down the key sectors under cyber siege in 2025, including prevalent cyberattack types and the impact on each.
Analysis
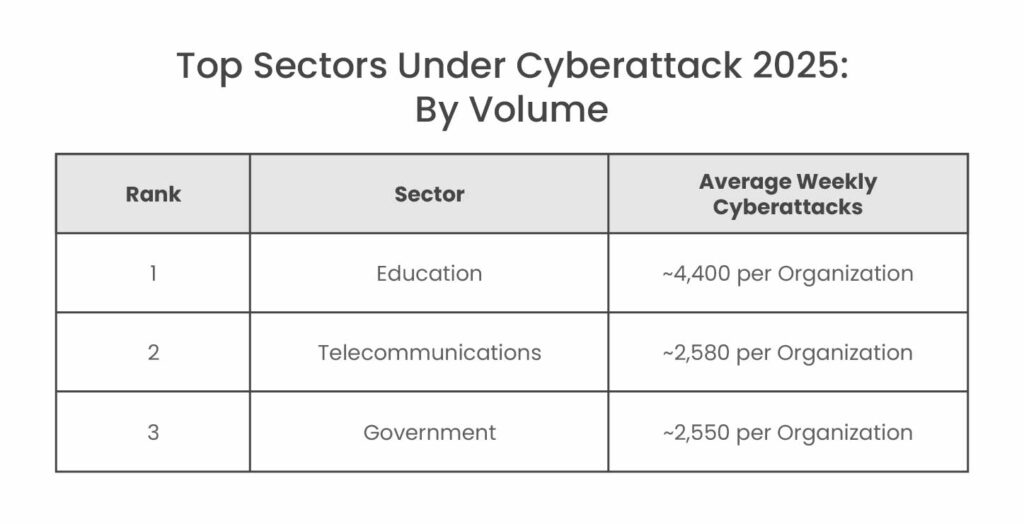
These far exceeded the global per-organization weekly attack average standing at ~1,938. The education sector in particular endured more than double the average attack load. Government agencies and telecom firms also saw elevated cyberattack rates due to the sensitive data and critical services they handle.
Analysis
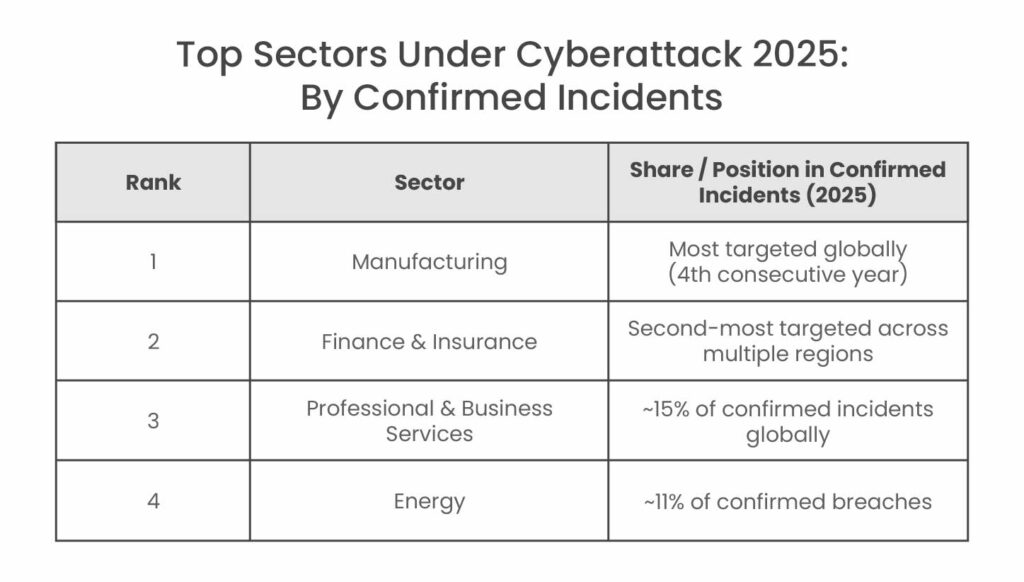
Looking at significant breaches and incidents as tracked by IBM X-Force and others, a somewhat different ranking emerges. IBM’s global incident response data showed these industries as the most targeted:
- Manufacturing – the most-attacked industry globally, for the 4th year in a row
- Finance & Insurance – consistently the second-most targeted sector in many regions
- Professional and Business Services – ranked third globally, comprising ~15% of cases, including consulting, IT services, law firms, etc.
- Energy – among the top four or five, comprising roughly 11% of breaches in IBM’s dataset.
Other sectors like healthcare and retail/wholesale also featured in the top 5 – 7 globally in 2024, with their share of cyberattack increasing year-over-year per IBM analysis. Healthcare sector comprises ~8% of incidents in Europe. Notably, public sector organizations were heavily targeted, especially in Europe – ENISA recorded public administration as the single most targeted sector with ~19% of recorded incidents in the EU during the latest reporting period.
Book Your Free Cybersecurity Consultation Today!
Government & Public Sector
By volume of attempts, the government was in the top three most-targeted industries worldwide, averaging ~2,500 cyberattack per week per organization. Public sector entities attract both nation-state actors for espionage and disruption and malicious hackers for data theft or ransom, putting this sector at high risk.
Cyberattack on government organizations were up ~26% year-over-year by mid-2025. A significant portion of these were Distributed Denial-of-Service (DDoS) and disruption attempts. ENISA noted that DDoS attacks predominantly hit government/public administration targets, where 34% of observed DDoS incidents.
Education Sector
Educational institutions, including schools, universities, and research organizations, have emerged as a top target, experiencing the highest volume of attacks of any sector in 2025. Check Point data shows education faced an average of 4,400+ attacks per week per organization, more than double the global average. This made education the #1 most-attacked sector by volume of attempts.
A notable trend in 2025 was a 40% year-over-year jump in attacks on the hospitality sector leading into the holiday season, but education still remained the most attacked industry worldwide each month. Despite increased awareness, the education sector will likely remain in ‘adversaries’ crosshairs’ due to the combination of high-value data and often inadequate security measures.
Manufacturing & Industrial Sector
The manufacturing sector, including industrial and critical manufacturing organizations, endured some of the most frequent and severe cyberattack in 2025. By many measures, manufacturing is the single most attacked sector globally in recent years. IBM’s data shows that for the 4th consecutive year, manufacturing was the top-attacked industry worldwide.
In IBM’s 2024 incident response dataset, manufacturing had the highest percentage of cases, even above finance. Similarly, Palo Alto’s Unit 42 found that manufacturing was the most common sector appearing on ransomware leak sites, about 25% of all victims. This indicates it bore the brunt of ransomware extortions globally.
According to IBM X-Force, extortion was the objective in ~29% of attacks on manufacturing, followed by data theft in ~24%. The “double-extortion” model is especially effective against manufacturers. OT vulnerabilities also put this sector at risk; legacy industrial control systems often have unpatched flaws. In fact, of all ICS security advisories issued in 2024 – 25 by CISA, nearly 46% involved vulnerabilities in critical manufacturing systems, given that it has the single largest share.
Financial Services Sector
While finance did not top the list in raw attack frequency, it consistently ranked among the most attacked sectors by confirmed breaches, often standing at #2 globally behind manufacturing. In some regions, finance was the #1 targeted vertical; for example, across the Middle East & Africa, nearly 38% of incidents in 2023 were aimed at the finance/insurance industry.
According to ENISA, the finance sector was among the targets of DDoS and other availability attacks as well. Approximately 9% of significant DDoS attacks in Europe hit banking/finance in the past year. Some of these were extortionate DDoS attacks, where hackers demand payment to stop flooding a bank’s public-facing services.
IBM’s 2025 Cost of a Breach report found that breaches in highly regulated industries like finance tend to cost well above the global average of $4.45M, once compliance and notification costs are considered.
Healthcare Sector
Ransomware is still the number-one menace for hospitals and healthcare providers. In the first 9 months of 2025, at least 293 ransomware attacks struck hospitals and direct care providers worldwide, plus another 130 attacks on health sector business associates like pharmaceutical vendors and billing firms. Attacks on frontline providers remained roughly flat compared to 2024, while attacks on healthcare third-party vendors rose by 30%.
Through Dec 2025, over 42 million individuals’ data were affected by healthcare cyberattacks in the U.S. alone. This figure, while lower than the anomalous 270 million impacted in 2024 due to one mega-breach, is still enormous. Personal health information (PHI) is extremely valuable on black markets, fueling these breaches. In 2025, a single attack on a major U.S. healthcare provider (DaVita) by the Interlock ransomware group exposed about 2.7 million patient records.
Healthcare data breaches carried the highest average cost of any industry, about $9.7 million per breach as of 2024, according to IBM. Ransom demands on hospitals in 2025 were often in the multi-millions, averaging ~$500K for smaller incidents, with one UK lab attack seeing a $50M demand. Attacks on health sector vendors also had ripple effects: a breach at a widely used software or cloud provider can simultaneously expose dozens of hospitals, as occurred in the 2024 Change Healthcare incident that impacted 3/4 of U.S. hospitals.
Energy & Utilities Sector
In 2024 – 25, 21% of discovered ICS (industrial control system) vulnerabilities affected energy systems, the second-highest sector exposure after manufacturing. Check Point’s tracking of ransomware in Q2 2025 showed “Industrial manufacturing” and “Construction & Engineering” among the top three most-hit industries on ransomware leak sites. These sectors are closely tied to critical infrastructure.
Two threat categories loom large for the energy and utilities sector. They are ransomware/extortion and state-sponsored APT intrusions. Nation-state actors engaged in espionage and pre-positioning: for instance, malware implants were found in some national grid networks as revealed by government alerts that could potentially be used to disrupt systems, echoing the tactics of the 2015 and 2016 Ukraine grid attacks. ENISA reported that transportation and energy infrastructure were frequent targets of DDoS and intrusion attempts in the context of geopolitical conflicts.
As one data point, critical manufacturing and energy together accounted for ~67% of the ICS vulnerabilities reported in 2024 – 25, underscoring how these sectors’ systems are in the danger zone and must be patched and protected proactively.
Get in!
Join our weekly newsletter and stay updated
What to Carry Forward in 2026?
Core Strategy (All Sectors)
- Shift from periodic VAPT to continuous, risk-based VMDR
- Prioritize vulnerabilities using CVSS + exploitability + threat intel
- Correlate vulnerabilities across network, cloud, web apps, APIs, and endpoints
- Eliminate false positives using AI-driven validation
- Track vulnerabilities across their entire lifecycle: detect, prioritize, remediate, and revalidate
What to Enforce
- Continuous scanning, not quarterly or annual assessments
- Attack-path analysis to identify real breach routes, not isolated findings
- Automated mapping of vulnerabilities to compliance requirements.
- Integration with ticketing tools for accountable remediation
Modern Approach
- Combine automated pentesting with targeted manual validation
- Focus on business logic flaws, not just OWASP checklist issues
- Include API, cloud misconfigurations, IAM abuse, and privilege escalation paths
- Validate whether vulnerabilities are actually exploitable, not just theoretically present
- Re-test automatically after fixes to ensure true closure
Sector-Specific VAPT Focus
| Sector | Mitigation Strategy |
| Manufacturing & Energy | OT/ICS vulnerability scanning with safe, non-intrusive methods. Identify IT-OT attack paths and insecure remote access |
| Finance | API security testing and authentication/authorization flaws. Misconfigurations in cloud and IAM are leading to fraud |
| Healthcare | Asset discovery across legacy systems and third-party integrations. Prioritize vulnerabilities affecting availability and patient safety |
| Government & Education | Internet-facing asset discovery and misconfiguration scanning. Rapid detection of exposed services and outdated software |
FAQs
- Which sectors are most targeted by cyberattacks in 2025?
In 2025, the most targeted sectors include education (highest attack volume), manufacturing (most confirmed breaches for the 4th year), finance & insurance, government/public sector, healthcare, and energy & utilities.
- Why is the manufacturing sector the most attacked industry globally?
Manufacturing is heavily targeted because of ransomware profitability, legacy OT/ICS systems, and weak IT-OT segmentation. Nearly 29% of attacks aim at extortion, and the sector accounts for the largest share of ICS vulnerabilities, making operational disruption highly effective for attackers.
- What cybersecurity approach should organizations adopt going into 2026?
Organizations should move from periodic assessments to continuous, risk-based VMDR, combining CVSS scoring, exploitability, threat intelligence, attack-path analysis, and automated revalidation.









Leave a comment
Your email address will not be published. Required fields are marked *