In 2025, the average cost of a data breach reached an alarming Rs 22 Crore; a 13% increase from the previous year. This trend highlights how breaches are not only more frequent and sophisticated but also increasingly costly, putting an organization’s reputation and finances at risk. To combat these threats, companies are investing in robust security measures earlier in the software development process. One such proactive measure is Static Application Security Testing. It is a method of finding software vulnerabilities before applications go live. This article will explain what SAST is, why it’s so important, how it works, its key benefits, and how it fits into a secure SDLC.
Table of Contents
What is Static Application Security Testing (SAST)?
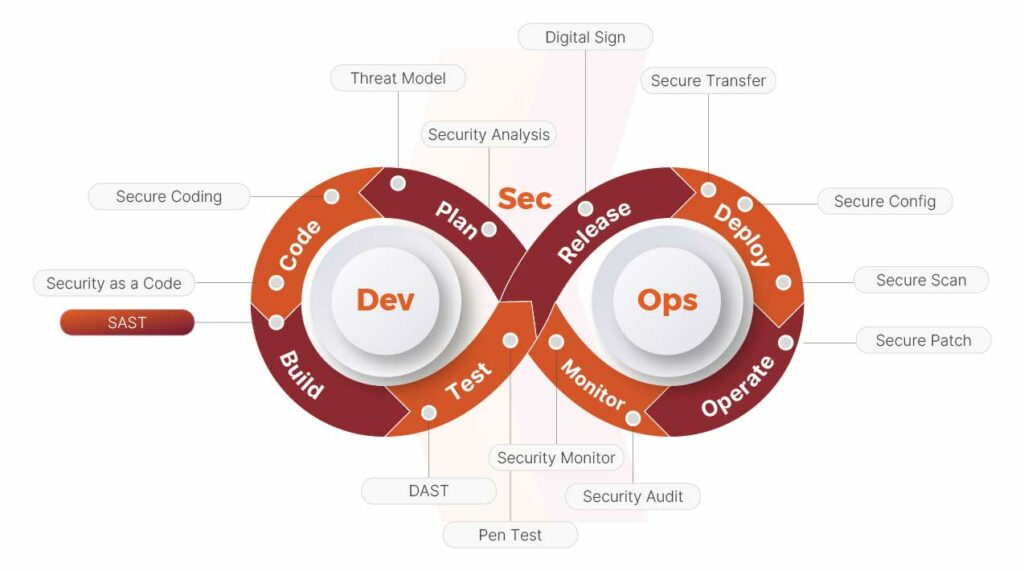
Static Application Security Testing is a white-box testing technique that analyzes an application’s source code for security weaknesses without executing the program. In other words, SAST involves scanning the code itself to spot vulnerabilities or insecure coding patterns, rather than testing the running application from the outside. Because it has full access to the codebase, static application testing is considered “white-box,” where the tester has internal knowledge of the system as opposed to “black-box” testing like dynamic analysis, where the tester interacts with a running application without knowing the internal code. A SAST tool will comb through the source code, bytecode, or binaries of software to flag sections that might be prone to security issues. It leverages large databases of known vulnerability patterns and secure coding rules to pinpoint common mistakes that could lead to exploits.
This testing checks the code for a wide range of known vulnerability types like injection flaws (SQL injection), cross-site scripting (XSS), buffer overflows, insecure use of cryptography, hard-coded secrets, and so on. These categories of bugs align with well-known security standards such as the OWASP Top 10. By scanning the code against these patterns, SAST tools can identify vulnerabilities early in development, long before the application is ever run or deployed. The main goal is to catch weaknesses that could potentially lead to a security breach if left unaddressed.
How Does SAST Work?
Static testing work by performing sophisticated code analysis to uncover weaknesses. The process usually involves parsing the code and building an internal model of the application, for instance, an abstract syntax tree that represents the code’s structure. The tool then applies a variety of analysis techniques:
- Data Flow and Control Flow Analysis: SAST examines how data moves through the code (data flow) and how the application’s logic branches and executes (control flow). By doing so, it can detect issues like user input flowing into a database query without proper sanitization (indicating a possible SQL injection) or sensitive data being mishandled.
- Pattern Matching and Rules: SAST tools use a set of predefined security rules and patterns to hunt for known bad coding practices. These rules are often derived from industry standards and past vulnerability research. When the code matches a dangerous pattern or violates a secure coding guideline, the tool raises an alert. Such modern testing solutions come with extensive rule sets for various languages and frameworks, and many allow custom rules so organizations can enforce their internal security policies.
- Semantic Analysis: Beyond simple pattern matching, advanced SAST engines perform semantic analysis, understanding the context of code usage. For instance, they might not only flag the presence of a risky function call, but also determine if it’s used in an insecure way. They can detect if an encryption function is used with a hard-coded key, or if error messages leak sensitive information. This intelligent analysis reduces false alarms by focusing on real issues.
Once the analysis is done, the SAST tool generates a detailed report of findings. Each finding typically includes the location in code (file and line number), a description of the vulnerability type, severity level, and often remediation guidance (suggestions for how to fix the issue).
Book Your Free Cybersecurity Consultation Today!
SAST Vs DAST
Importantly, SAST is performed without executing the application. This means it can be run in environments where the code might not even be fully functional yet, such as a partial codebase in development. It doesn’t require a deployed environment or test inputs to run. This static approach contrasts with Dynamic Application Security Testing (DAST), which involves running the application and probing it from the outside, often emulating malicious attacks.
Both methods have their place: SAST and DAST are complementary.
- SAST finds vulnerabilities inside the code, like a developer’s mistakes in handling input, whereas DAST finds vulnerabilities by interacting with a running app, like discovering a flaw by sending malicious requests. For example, it might flag a possible XSS (cross-site scripting) issue by spotting unsanitized output in code, while DAST might trigger an XSS by injecting a script into a running application and seeing if it executes.
- A key difference is that SAST catches issues before build/deployment, whereas DAST usually occurs later in a testing stage. By using SAST, organizations can fix problems at their source in the code, rather than after the fact.
Why is SAST Important?
Early Detection of Vulnerabilities: “Shift Left” Security
The foremost benefit of SAST is that it enables finding and fixing security issues early in the development lifecycle. This is often described as “shifting security left”. Developers are still in the context of the code they just wrote, and the fix can be made on the spot.
Reduced Risk of Security Breaches
By eliminating vulnerabilities before release, SAST directly reduces the risk of successful cyberattacks and data breaches. Many high-profile security incidents have been traced back to code-level mistakes for instance, an injection flaw in a web application or a buffer overflow in a piece of software that attackers exploited. SAST acts as a safety net to catch those mistakes.
Cost Savings and Efficiency
Beyond just breach avoidance, there is a significant economic incentive to fix bugs early. We’ve already noted the exponential cost increase of fixes as you move later in the SDLC. By incorporating SAST into normal development, companies save money by not having to retrofit security into code at the last minute or, worse, after an incident.
One analysis by NIST concluded that a flaw caught in development might cost 1/30th of the effort compared to if it were only caught in production.
Improved Code Quality
Modern SAST integrates tightly with developers’ workflows, for example, plugging into code editors/IDEs or running automatically on pull requests. This gives developers near-instant feedback on potential security issues as they write code. Instead of discovering months later that a certain coding practice was insecure, the developer can learn and correct it on the fly.
Enforcing Standards and Compliance
SAST is a great mechanism to ensure that code adheres to both internal security policies and external standards and regulatory requirements. SAST can automatically check every new code change against these rules, acting as a constant gatekeeper for coding standards. Externally, many industries have regulations and standards that call for secure software development practices.
Improved Confidence and Risk Management
Knowing that your code has been scanned thoroughly by SAST can increase the confidence of both development teams and management when deploying software. It’s a form of quality assurance specifically for security.
SAST in the Secure Software Development Lifecycle (SDLC)
SAST plays the role of an early defect detector for security. The software development lifecycle typically includes stages such as requirements, design, coding, testing, deployment, and maintenance. A secure SDLC weaves security practices into each of these stages. SAST comes into play primarily during the coding and testing phases, though its influence starts as soon as developers write code.
In DevSecOps pipelines, SAST acts as an automated gatekeeper, halting builds with critical issues and ensuring security checks happen as quickly as code changes. This reduces friction between teams and ensures that security is a shared responsibility, not a last-minute add-on. Ultimately, SAST helps organizations ship more secure applications while avoiding the high costs of fixing issues post-deployment.
Get in!
Join our weekly newsletter and stay updated
In The End
Instead of asking “How do we fix this vulnerability in production?”, teams with SAST can say “We’ve already fixed it during development.” In today’s threat landscape, where a single overlooked code mistake can expose your money bank, such an approach is not just beneficial, it’s increasingly essential. By embracing SAST, organizations of all kinds can improve their security posture, save time and money, and deliver software that users and stakeholders can trust. As the adage goes, “an ounce of prevention is worth a pound of cure,” and SAST exemplifies this by preventing security issues at their source. Let Kratikal help you build a secure code!
FAQs
- What is SAST and how does it improve application security?
SAST scans source code to find security flaws early, helping prevent breaches and improve code quality before the app runs.
- How is SAST different from DAST in application security testing?
SAST analyzes code without running it, while DAST tests live apps. SAST finds internal flaws; DAST detects real-time behavior issues.
- Why should organizations integrate SAST into their SDLC in 2025?
SAST helps catch vulnerabilities early, cut costs, meet compliance, and build secure software in today’s high-risk threat landscape.









Leave a comment
Your email address will not be published. Required fields are marked *