28% of organizations have become a part of some gruesome cybersecurity incidents, according to a security report released by IBM in 2024. Among the attack vectors of such attacks were malware infections, phishing scams, and unintentional data leaks. To the rescue comes ISO 27001. It provides a framework that helps organizations like yours fight back against these threats. Further into the picture comes the ISO 27001 remote access policy. It protects sensitive information and builds trust with clients, partners, and regulators. Either done wrong or worse, ignored weak remote access controls open the door to major problems, from costly data breaches to business disruptions. Below, we break down the key risk areas – Technical, Legal, Operational, and Reputational.
Further, let’s understand what’s at stake when your organization doesn’t align with ISO 27001’s remote access policy requirements.
Table of Contents
ISO 27001 Remote Access Policy – Technical Risks
Not following ISO 27001’s remote access controls leads to technical vulnerabilities that are much worse than said. Starting at the basic level are weak or missing security measures, like not using encryption or multi-factor authentication. It makes it far easier for hackers to burgle in. Remote employees often log in over personal Wi-Fi or on unmanaged devices, making it more vulnerable as it lacks enterprise-grade protections.
What Next? These negligencies create cracks that become the welcome door for hackers to steal credentials, eavesdrop on traffic, or install malware. Without an ISO 27001 remote access policy enforcing strong access controls, it becomes less obligatory for organizations to require safeguards such as VPN encryption, device patching, two-factor logins, or MFA, all of which are crucial to prevent unauthorized access.
Do you know what can be the technical fallout in such scenarios? Hackers can penetrate the network, exfiltrate sensitive data, plant ransomware, or spy on controversial communications without anyone even noticing.
Let’s go through some real-life scenarios that took place due to failure in aligning with the ISO 27001 remote access policy –
Case Study: Data Breaches via Unsecured Access
- In 2024, the AlphV ransomware group infiltrated Change Healthcare through a remote access portal that had no multi-factor authentication (MFA).
- Attackers used stolen credentials to get into a Citrix remote desktop system that wasn’t MFA-protected, then moved through the network and stole protected health data.
- Security experts called it “pure negligence” and noted that proper authentication would likely have stopped the breach.
What does this case highlight? It highlights that no MFA, weak passwords, or neglecting other lax remote login security can directly lead to a major data breach, malware outbreak or something more sinister.
Case Study: Network Intrusions from Weak VPN Controls
- A notorious example that highlights network intrusions is the Colonial Pipeline hack.
- In 2021, attackers broke in through an inactive VPN account with no MFA enabled, using a password leaked on the dark web.
- The VPN wasn’t secured, which violated the ISO 27001 best practices. This highlights the importance of complying with the remote access policy.
- Non-compliance allowed hackers to breach the company’s IT network by compromising only a single password.
The lesson learned from such a breach is that one unprotected remote access point can compromise an entire system.
Book Your Free Cybersecurity Consultation Today!
ISO 27001 Remote Access Policy – Legal and Compliance Risks
Your organization qualifies for legal and compliance-related troubles when you don’t align with ISO 27001’s remote access requirements. Not only ISO 27001, many other data protection laws, industry standards, and regulations demand that organizations safeguard sensitive information, including that data accessed by remote workers.
Failing to do the same can persuade your organization to face consequences that can be severe. It can lead to –
- Hefty fines, lawsuits, and regulatory sanctions if your organization fails to protect data.
- Lack of documented security controls and risk assessments can look very bad in audits or worse, in court.
- ISO 27001 compliance helps demonstrate due diligence. It is proof that your team took reasonable measures to secure remote access. Without that, you may be seen as negligent.
- Failure to follow the standard’s remote access controls could result in losing ISO 27001 certifications and important contracts.
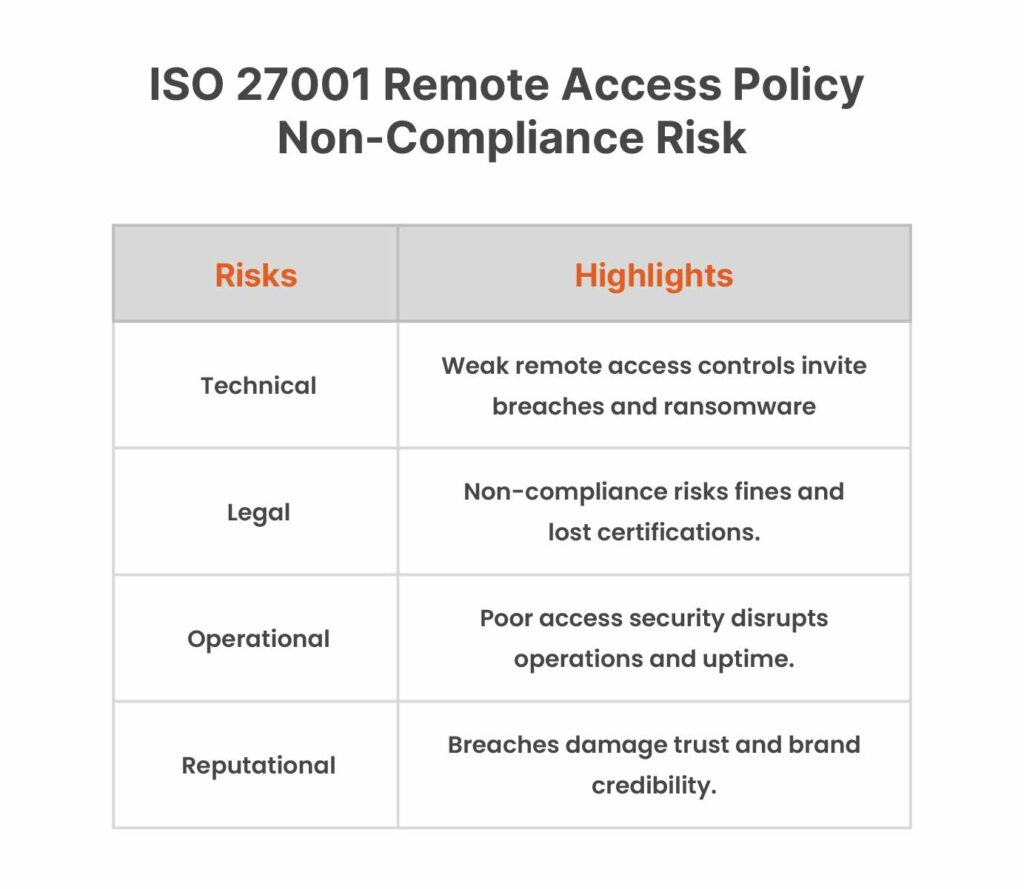
ISO 27001 Remote Access Policy – Operational Risks
You are directly threatening operations and business continuity if your organization does not abide by the ISO 27001 remote access policy. A breach via remote access can disrupt your business operations by forcing systems to go offline. Further, it can compel your organization to take up emergency measures that can bring your organizational operation to a halt for a long period.
Here’s an example that highlights the consequences of operational risks –
Case Study 1
Remember the Colonial Pipeline attack? The attack that led the company to shut down a 5,500-mile fuel pipeline for five days. The aftereffect – it caused gasoline shortages across multiple states.
Case Study 2
A similar incident happened in 2024 – the attack in Change Healthcare. Hackers infiltrating the weak remote access and deploying ransomware led the healthcare organizations medical claims processing systems to come to a halt for over 30 days. The result was worth global news. It not only affected pharmacies and hospitals nationwide but patients as well.
If an intruder compromises your network, what happens?
As an organization, you need to disconnect remote access entirely to contain the incident. Your remote employees cannot work in this scenario, affecting the business. Recovery can take days or weeks, and disruption in business processes leaves customers unserved.
That’s not all! Financial losses come next due to downtime, leading to lost sales and productivity. Furthermore, incident response costs, paying ransoms, or investing in urgent system overhauls further juggle your money bag.
ISO 27001 Remote Access Policy – Reputational Risks
Not following ISO 27001 remote access policy guidelines increases the chance of an incident that could put your organization in unwanted headlines. The reputational damage from such an event can be long-lasting.
- Customers, partners, and the public may start to question your competence and commitment to security if they learn that a breach happened due to lax remote access practices, like no MFA, weak passwords. In one survey, 75% of US consumers said they would stop doing business with a brand after a major cybersecurity incident. Further, 66% of consumers say they no longer trust a company that has suffered a data breach to handle their data.
- Reputational risk can also affect future opportunities. Business clients, especially in sensitive industries, often require partners to have strong security or ISO 27001 certification. If your prospective partner knows you have a security lapse, it could disqualify your organization from contracts or bids.
- It is a known fact that the media and regulators tend to pile on after an incident. Organizations might be publicly criticized for not following known best practices, further tarnishing their image.
Get in!
Join our weekly newsletter and stay updated
End Note
Now that we have discussed the unfortunate aftermath of non-complying with the ISO 27001 remote access policy, it is a risk that no organization can afford. Technical shortcuts in remote security often backfire with breaches. Then comes legal non-compliance, which brings fines and lawsuits. Operational lapses cause costly downtime, and reputational damage drives customers away. Thus, the solution is aligning with the ISO 27001 Remote Access Policy.
FAQs
- What happens if my organization doesn’t follow the ISO 27001 Remote Access Policy?
Ignoring ISO 27001 remote access rules increases risks of breaches, fines, and downtime. Weak authentication or unencrypted access can expose sensitive data and damage trust.
- How does ISO 27001 improve remote access security?
ISO 27001 enforces strong authentication, encryption, and access controls, reducing unauthorized entry and providing compliance to clients and regulators.
- Why is ISO 27001 compliance critical for remote teams?
Remote work widens attack surfaces. ISO 27001 ensures secure user access, maintains compliance, and prevents costly incidents and disruptions.









Leave a comment
Your email address will not be published. Required fields are marked *