Do you think cyberattacks are headlines anymore? Given the frequent occurrences, it has turned headlines into a day-to-day reality, and that’s scarier! Organizations that are big names to small organizations that are still growing, every one of them is being hit one way or the other. From supply chain attacks to data breaches, the impact these attacks gives back is nothing less than brutal. Millions lost, operations disrupted, and in worst cases, your organization’s name can fade out forever. But the bad also brings out the good! In situations that are inevitable, what can you do to remain in a safe spot?
A cyber crisis plan is no longer a “good-to-have.” It’s a survival requirement. Let’s cut short to what you need to build a strong and effective cyber crisis management plan:
Table of Contents
- 1 Book Your Free Cybersecurity Consultation Today!
- 1.0.1 Plan Your Communication: A Silence Plan is Never Well Executed
- 1.0.2 Assign Roles Clearly: Everyone Must Know Their Job
- 1.0.3 Cover Legal and Compliance Requirements
- 1.0.4 Strengthen Your Backup Protocols: The Real Lifeline
- 1.0.5 After the Crisis: Review and Improve
- 1.0.6 Tailor the Plan to Your Organization’s Size
- 2 Get in!
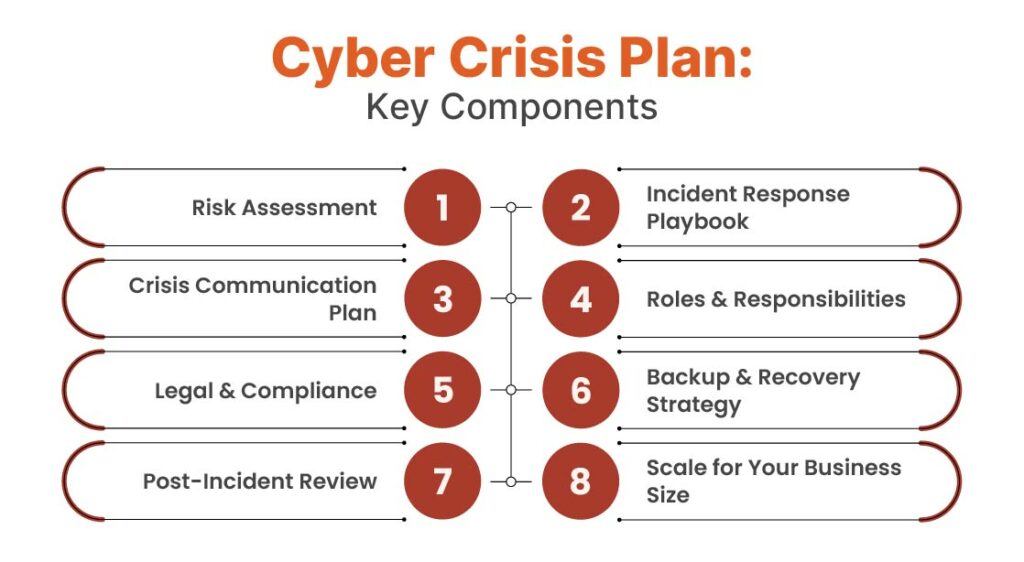
Essential Components of A Cyber Crisis Plan
In fact, over 80% of small businesses have suffered a security breach, and nearly one in five of those attacked had to file for bankruptcy or close their doors. Thus, having a plan is not enough! You need to make sure that your ‘cyber crisis plan’ becomes the invisible door that ensures the utmost protection your organization needs. Here’s what you need to:
Start With a Risk Assessment: Know What Matters Most
Before you plan how to respond to a crisis, you need to understand what you’re protecting. A risk assessment helps you:
- Identify your crown jewels – the most critical asset
- Map out potential threats like ransomware, insider misuse, etc
- Spot vulnerabilities in your asset inventory
- Prioritize where to invest your defenses
For Large Organizations: It usually involves formal tools, audits, and teams.
For Small Organizations: Think of it as a straightforward checklist.
The Common Goal: Know what will hurt the most if attacked and plan around those areas first.
Build a Clear Incident Response Playbook
During a cyber incident, panic leads to mistakes. A structured cyber crisis plan prevents that. A strong incident response process includes six key steps:
| Steps | Highlights |
| Preparation | Set roles, tools, and policies in advance |
| Detection and Analysis | Identify the incident quickly and understand its scope |
| Containment | Limit the spread of the attack |
| Eradication | Remove malware, shut down vulnerabilities |
| Recovery | Restore systems from clean backups and monitor stability |
| Lessons Learned | Review what happened and improve the plan |
This playbook ensures your team follows a logical, organized sequence instead of scrambling in confusion.
Book Your Free Cybersecurity Consultation Today!
Plan Your Communication: A Silence Plan is Never Well Executed
A cyber crisis impacts trust just as much as technology. People want clarity. Your communication plan should cover:
- How employees will be informed?
- What customers and partners should be told?
- Who speaks to media and regulators?
- Pre-approved templates for common scenarios?
- Backup communication channels (in case email or internal systems are down)
Early, honest, and consistent communication can prevent panic and protect your reputation, even during a tough incident. A lie in the beginning takes extra minds and time to carry it forward, which no organization can afford at the time of a cyber crisis.
Assign Roles Clearly: Everyone Must Know Their Job
A cyber crisis is not the time to figure out responsibilities. Assign them beforehand. Proactiveness in cybersecurity is always the right step. At the broad level, key roles usually include:
- Executive Leadership: Makes final decisions
- IT & Security Teams: Handle investigation, containment, and recovery
- Communications/PR: Manage internal and external messaging
- Legal/Compliance: Manage regulatory reporting and notifications
- External partners: Forensics, incident responders, cyber insurance
Keep a list of names, contacts, and backups, as cyber incidents don’t wait for office hours. This ensures no critical task goes untouched.
Cover Legal and Compliance Requirements
Data breach laws often require quick notification,s and sometimes within 72 hours.
Your plan should include:
- Which laws apply to your business?
- When to notify regulators?
- When to inform customers?
- How to maintain legal privilege?
- When to involve attorneys?
Being legally prepared prevents costly fines and compliance failures during a crisis.
Strengthen Your Backup Protocols: The Real Lifeline
If ransomware strikes or data is corrupted, backups are your fastest path to recovery. Follow the 3-2-1 rule. It means:
- 3 copies of your data
- 2 different storage types
- 1 offline/offsite backup
Also, test your backups regularly. Put simply, a backup that doesn’t restore is just wishful thinking. Good backups can turn a potentially devastating attack into a manageable recovery.
After the Crisis: Review and Improve
A cyber incident is a learning opportunity. Hold a post-incident review to discuss:
- What worked?
- What didn’t?
- What slowed the response?
- Which vulnerabilities need fixing?
- How the plan needs to be updated?
Do this within a week or two while the details are fresh. Why? This step ensures your plan gets stronger over time.
Tailor the Plan to Your Organization’s Size
Every organization needs an individual cyber crisis plan that is based on their goals, assets, and operational needs. Here are some common aspects that organizations need to focus on irrespective of their industry type and size:
For Large Organizations:
- Build detailed, scenario-based plans
- Conduct regular tabletop drills
- Involve multiple departments
- Keep external partners on retainer
- Ensure smooth coordination across teams.
For Small Businesses:
- Keep it simple
- Assign clear roles
- Train employees
- Know which external expert you’ll call
- Maintain basic cyber hygiene
Scale the plan to your reality, but make sure you have one and an effective cyber crisis management plan.
Get in!
Join our weekly newsletter and stay updated
Don’t Wait for the Attack to Start Planning: Get Your Cyber Crisis Plan with Kratikal’s Help
Cyber threats are rising, and no business is immune. A well-prepared cyber crisis plan can turn a potentially devastating attack into a controlled, recoverable situation. And, there is no time better than ‘now’. Before you build a cyber crisis plan, get in touch with cybersecurity experts like Kratikal. We can help you in understanding your risks, defining roles, planning communication, meeting legal requirements, and maintaining reliable backups, which are the foundation of a strong response strategy. Because the only time you cannot build a good cyber crisis plan is during a crisis.
FAQs
- What is a cyber crisis plan, and why is it important?
A cyber crisis plan outlines how your organization prepares for and responds to cyberattacks. It’s essential because it reduces downtime, financial loss, and chaos during an incident.
- What should a cyber crisis management plan include?
It should cover risk assessment, an incident response playbook, communication steps, assigned roles, legal requirements, and reliable backup processes.
- How often should a cyber crisis plan be updated?
Review it at least once a year and after every incident to reflect new threats, system changes, and lessons learned.









Leave a comment
Your email address will not be published. Required fields are marked *