Protecting cloud and hybrid networks is critical, as unknown vulnerabilities can pose serious risks to enterprises. NetOps teams must oversee the performance and security of on-premises and cloud-based applications, software, devices, and instances—all while cyber attackers constantly exploit weaknesses in enterprise networks. These threats impact organizations across industries. Gartner forecasts that by 2025, 45% of global enterprises will face software supply chain attacks. Statista also reported that in Q3 2022, approximately 15 million data records were exposed in breaches—an alarming 37% increase from the previous quarter. Even the most avid security enthusiasts sometimes get confused when it comes to differentiating between vulnerability management and vulnerability assessment. So, here is a detailed blog explaining the fine differences between the two.
Table of Contents
What is Vulnerability Management?
In this evolving world of a complex IT landscape, we get to hear numerous cybersecurity buzzwords and strategies every day. Vulnerability assessment, penetration testing, and vulnerability management are among the most used terms when we talk about the protection of critical assets in an organization. But ever wondered do these terms mean? Let’s break them down one by one.
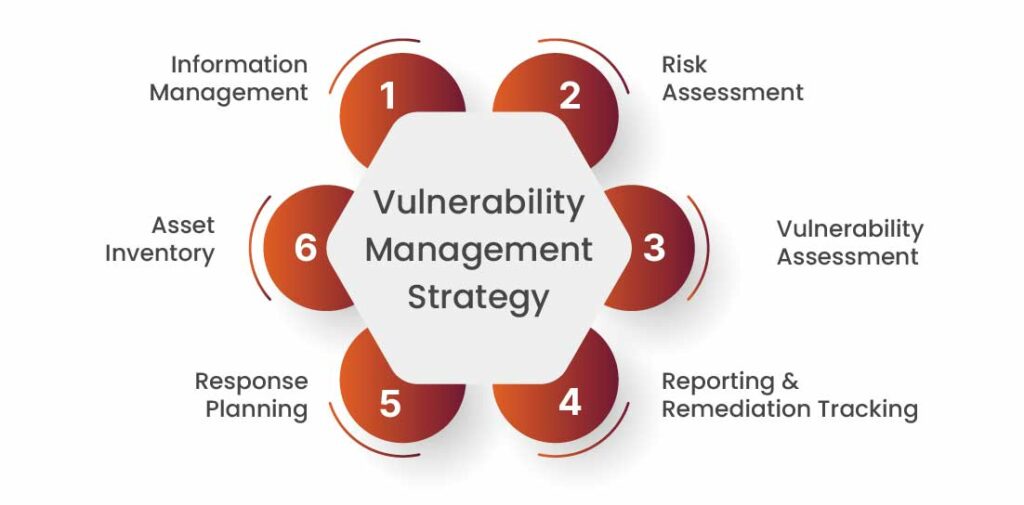
The term vulnerability management is an essential component that is required in creating an organization’s solid cybersecurity foundation. It is a broad ongoing process that manages an organization’s vulnerabilities constantly in a holistic manner. In this cyclical process, the software vulnerabilities are discovered, assessed, remediated, and verified. Follow the image to understand the vulnerability management process cycle more clearly.
This ongoing process requires scanning to assess the vulnerabilities continuously in order to ensure and fix the weaknesses. It is an integral part of computer and network security.
Book Your Free Cybersecurity Consultation Today!
What is Vulnerability Assessment?
The foremost step to fix security vulnerabilities is to identify them in the first place. Vulnerability assessment security testing identifies the gaps and loopholes present in the networks, endpoints, and applications. It is a one-time security testing program that is performed with a defined start and end date.
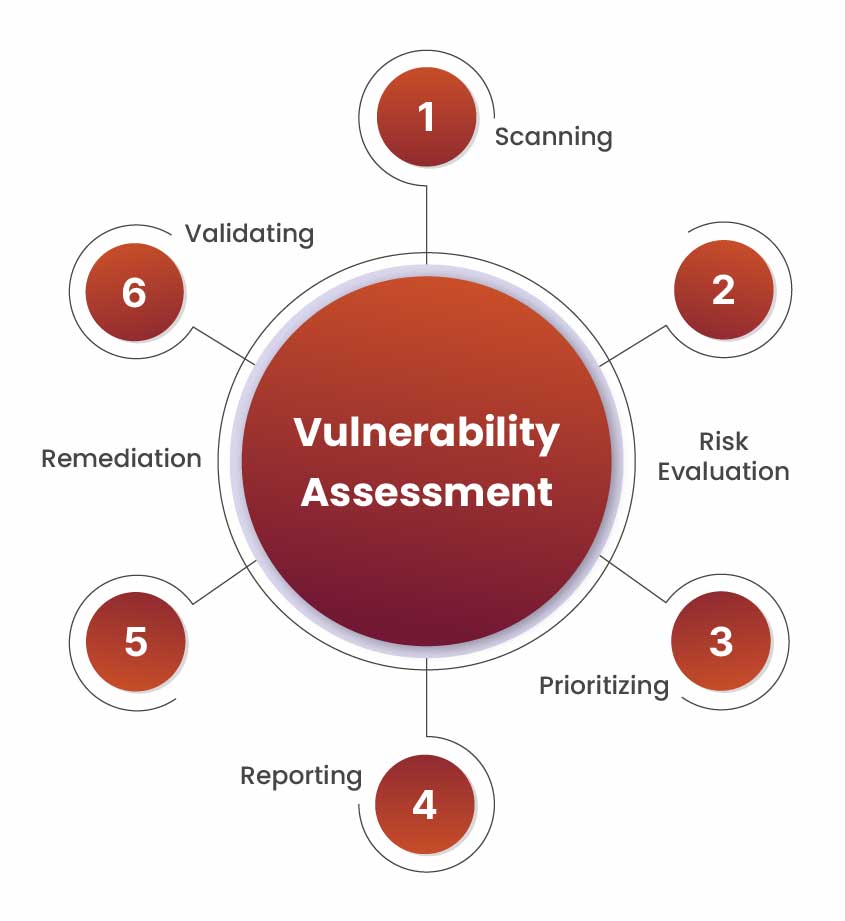
Vulnerability assessment is a risk-based approach that targets the different layers of technology, such as the host layer, network layer, and application layer. The purpose of this testing is to help organizations identify vulnerabilities existing in their software and IT infrastructure before any compromise takes place.
Vulnerability Management vs Vulnerability Assessment
| Aspect | Vulnerability Management | Vulnerability Assessment |
| Nature | Continuous process with no defined task or end date. | One-time or periodic start of vulnerabilities. |
| Objective | Helps organizations manage vulnerabilities effectively over time. | Identifies security gaps and guides fixes. |
| Scope | Ongoing monitoring, remediation, and improvement. | Focuses on detecting flaws in design configuration or application weaknesses. |
| Approach | Proactive risk management and mitigation strategy. | Diagnostic testing to assess the current security posture. |
| Outcome | Long-term security enhancement and reduced exposure to threats. | Provides immediate insights for the security team to fix vulnerabilities. |
| Dependency | Requires continuous assessment and updates. | Functions as an essential first step but is not sufficient on its own. |
Interdependence of Vulnerability Assessment and Management
Consequently, the vulnerability assessment process has a start and end date. But in order to secure IT assets, an ongoing approach like vulnerability management should be a part of it. The identification of strengths and weaknesses through assessment testing is basically the beginning process of IT infrastructure security. It is more of a part of vulnerability management where a proper plan is required to be created to prioritize and mitigate the cyber risks discovered. On the whole, the vulnerability assessment dictates the recommendations and objectives of the entire vulnerability management process.
The Significance of Security Risk Assessment and Management
It is important to assess and fully manage cyber risks with vulnerability assessment and security testing audits to secure the organization’s network security. With constantly evolving cyber attacks, it is highly important to understand the weaknesses existing in your IT infrastructure or web applications.
Regularly performed vulnerability assessment and proper vulnerability management practices play the role of cornerstones in the success of a complete cybersecurity program. Timely discovery of cyber threats helps patch networks and web application vulnerabilities. Also, both assessment and management security programs mitigate the risk elements and help in preventing the possibilities of the following cyber risks:
- Data breaches
- Ransomware infections
- IT Infrastructure damage
- Reputation damage
- Financial loss
Get in!
Join our weekly newsletter and stay updated
Conclusion
Both vulnerability management and vulnerability assessment are vital components of a comprehensive cybersecurity framework. While vulnerability assessment serves as the initial step in identifying gaps and weaknesses within an organization’s IT infrastructure, vulnerability management takes a broader, ongoing approach to monitor, remediate, and enhance the overall security posture. Together, these processes are essential in minimizing risks, preventing potential cyber threats, and ensuring the long-term safety of critical assets. By regularly assessing vulnerabilities and adopting comprehensive management practices, organizations can effectively secure their networks, applications, and reputation in the face of ever-evolving cyber threats.
FAQs
- How does vulnerability management integrate into broader risk management strategies?
Modern programs combine vulnerability and risk management to address critical weaknesses. Risk management focuses on strategic threats, while vulnerability management targets technical issues. Together, they align vulnerabilities with exploit potential and business risks.
- What objectives should a vulnerability management program aim to achieve?
Vulnerability management aims to close exploit windows, ensure compliance, scan updated systems, confirm risks are patched, and maintain IT security. Businesses may track patch times or reduce recurring vulnerabilities to keep environments secure.









Leave a comment
Your email address will not be published. Required fields are marked *