Dynamic Application Security Testing (DAST) is a black-box security testing method that analyzes running applications for vulnerabilities by emulating real-world attacks against their exposed interfaces. Instead of analyzing source code, DAST using manual and automated tools interact with a live deployment of the application (web app, APIs, mobile backend, etc.) and inject malicious payloads to observe how the application responds. For example, a DAST scanner will send crafted inputs into form fields, URLs, cookies or API endpoints and check for issues like SQL injection, cross-site scripting (XSS), broken authentication, or insecure configurations; it treats the application as an external attacker would, DAST can uncover flaws that only manifest at runtime. Notably, DAST requires no access to source code or internal details of the application, making it suitable for testing third-party components or legacy systems where code is unavailable.
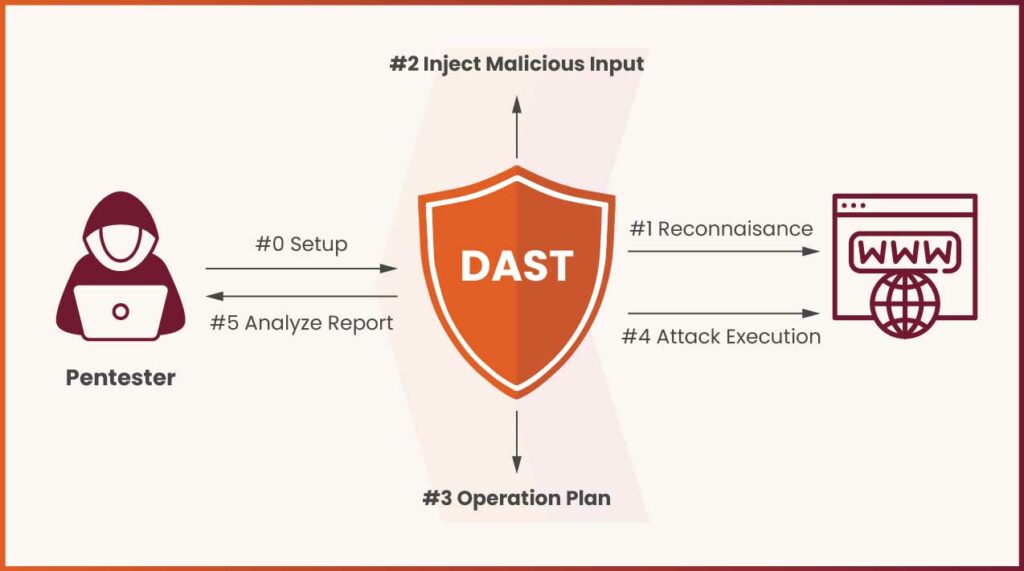
Table of Contents
How Can DAST Help Your Organization?
Implementing Dynamic Application Security Testing offers several tangible benefits for organizations across sectors:
Uncovers Runtime Vulnerabilities
DAST excels at finding security flaws that only appear in a running environment. By sending real attack payloads to the live app, it can detect SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other OWASP Top 10 issues. It will flag any unexpected behavior like a SQL error or injected script execution as a sign of a vulnerability. Because of this, Dynamic Application Security Testing can expose issues in authentication logic, input validation, and session management that static scanning might never see.
No Source Code Needed
Many organizations maintain legacy apps or use third-party components whose source is not available. DAST works without code access. It treats the app as a black box, so it can test compiled binaries, containerized services, or externally hosted APIs just as easily as in-house code. This makes Dynamic Application Security Testing well-suited for complex systems and for organizations that rely on outsourced development. OWASP notes that DAST tools can perform “sophisticated scans on the client side and server side without needing the source code or the framework the application is built on”.
Realistic Attack Emulation
Because DAST mimics how attackers infiltrate an app, it provides a practical measure of security posture. It finds issues under real-world conditions. Unlike static analysis, DAST focuses on runtime behavior and can catch vulnerabilities like authentication bypasses or weak passwords that appear only when the full app is active. In short, Dynamic Application Security Testing tests what an attacker can see and do, which is invaluable for understanding real exploit risks.
CI/CD and DevSecOps Integration
DAST can be automated and integrated into DevOps pipelines to provide continuous security feedback. By adding such scans into a CI/CD workflow, teams get immediate insights into any new vulnerabilities introduced by recent code changes. This “shift-left” approach means security testing happens as part of development. In practice, a DAST scan might be run nightly or on every release candidate, catching flaws before they reach production.
Reduced Risk and Cost
Finding and fixing vulnerabilities early or before deployment is far cheaper than dealing with a breach later. If vulnerabilities are left unchecked and the app is deployed, this could lead to a data breach, resulting in major financial loss and damage to your brand reputation. By contrast, catching issues via DAST during development or testing significantly lowers remediation costs. Dynamic Application Security Testing’s broad coverage helps prevent breaches in the first place, a proactive risk reduction.
Enhanced Overall Security Posture
DAST provides organizations with a continuous, up-to-date view of security. Regular DAST scans demonstrate due diligence to auditors and can help with compliance. Many standards call for dynamic scanning or penetration testing of live systems. By fulfilling these requirements, DAST helps organizations meet regulatory mandates while actually improving security.
Book Your Free Cybersecurity Consultation Today!
DAST – The Phases
DAST typically proceeds through several phases: launching or pointing the scanner at a deployed instance, discovering application pages and inputs (crawling), injecting various attack vectors, and analyzing the responses. In practice, this may look like:
- Setup: A test instance of the application is deployed (e.g. in a QA or staging environment) and made available on the network. It is configured with the base URL and any required authentication.
- Discovery/Crawling: It automatically explores the application’s interface, following links, forms, and API endpoints, to build a map of pages, parameters, and inputs.
- Attack Injection: The scanner sends malicious payloads (e.g. SQL snippets, script tags, overlong strings) through identified inputs, simulating attacks such as SQL injection, XSS, CSRF, and others. In doing so, it attacks the application like a malicious user would.
- Response Analysis: It monitors responses, looking for anomalous behavior like error messages, data exposure, failed sanitization, etc. that indicate a vulnerability.
- Reporting: Detected issues are compiled into a report with details on the vulnerability type, affected endpoints, and suggested fixes.
DAST vs SAST and IAST
DAST differs fundamentally from other common testing approaches:
SAST (Static Application Security Testing)
SAST examines source code without running the application. This testing parse code to find insecure patterns. In contrast, DAST tests the active application. This means SAST can catch deep code-level flaws and enforce coding standards early in the SDLC, but it might miss issues that only arise when the app executes. For example, SAST wouldn’t see a SQL injection flaw if the vulnerable code path was never reached or if a vulnerability arises from an environment misconfiguration.
Complementary Coverage
DAST is particularly effective for discovering vulnerabilities that emerge when the application is executed, whereas SAST finds flaws before execution. An organization typically uses both: SAST to catch code defects early (during coding or build) and DAST to validate the running system. Many modern DevSecOps pipelines include both for this reason.
IAST (Interactive Application Security Testing)
IAST blends elements of SAST and DAST. It typically involves an agent or sensor that is instrumented inside the application during testing. This agent observes the application’s internal behavior (data flows, executed code paths) while it’s running. In practice, IAST can monitor a live app during functional tests or DAST scans and report vulnerabilities with very precise context (often including exact code locations). Compared to DAST, IAST has more insight (because of instrumentation) and can pinpoint the code behind a flaw. However, IAST requires a lighter-weight sensor and typically only works on the same machine/process.
DAST is black-box (external, no code access); SAST is white-box (internal code analysis, no execution); IAST is grey-box (instrumented runtime analysis). Dynamic Application Security Testing can test third-party or legacy apps without code, but cannot see inside them. SAST sees every line of code but doesn’t run it. IAST provides rich context but depends on internal access at run time. Each approach finds some issues the others cannot, so industry best practice is to use them in combination.
DAST in the SDLC and DevSecOps
Dynamic testing does not exist in isolation; it should be part of a secure software development lifecycle. In a DevSecOps context, it is typically integrated as one of several automated security checks. For instance, a modern pipeline might look like:
- Build Stage: SAST (static code scanning) runs during build/compile.
- Unit/Integration Testing: The application is deployed to a test environment (in containers, cloud, etc.), where automated tests and DAST scans run.
- Release Candidate: Before promotion to production, a full DAST scan is executed, possibly using a copy of the production environment.
- Production Monitoring: Post-release, regular or continuous DAST scans of the live system help catch any emerging issues (e.g. from a new library or config change).
Finally, DAST aligns with industry guidelines. For example, the OWASP DevSecOps guideline highlights DAST scanning as a key testing activity suggesting nightly scans after configuration. NIST’s guidance on microservices and DevSecOps (SP 800-204C) explicitly defines Dynamic Application Security Testing as part of continuous testing in CI/CD. These frameworks make clear that DAST is a recommended practice for securing applications in any sector.
Get in!
Join our weekly newsletter and stay updated
Take Away
As OWASP and NIST emphasize, incorporating DAST into a secure development lifecycle and DevSecOps pipeline is crucial. DAST scans from cybersecurity experts like Kratikal provide fast feedback to developers, reduce the risk of breaches, and ultimately help all kinds of organizations ensure their software is safer when it goes live. In today’s threat landscape, dynamic testing is an indispensable part of building and maintaining secure applications.
FAQs
- What is Dynamic Application Security Testing (DAST) and how does it work?
DAST is a black-box testing method that scans live applications for security flaws by simulating real-world attacks. It doesn’t need source code and tests exposed interfaces like APIs, forms, and URLs to detect issues like SQL injection and XSS during runtime.
- How can DAST benefit my organization’s cybersecurity strategy?
DAST helps find runtime vulnerabilities missed by other tools. It supports third-party and legacy app testing, integrates into CI/CD for early detection, lowers remediation costs, and strengthens compliance with standards like OWASP and NIST.
- Is DAST better than SAST or IAST for application security testing?
DAST isn’t better, but complements SAST and IAST. SAST checks code, DAST tests the running app, and IAST offers runtime insights. Using all three gives broader security coverage across the development lifecycle.









Leave a comment
Your email address will not be published. Required fields are marked *