We have witnessed a surge in cloud adoption and data exposures, with a similar trajectory. A cloud security report highlights that 95% of organizations experienced cloud-related breaches in an 18-month period. Among them, 92% of breaches exposed sensitive data. It is important to note that most incidents do not germinate from exploits that fall under the “exotic” category; instead, they sprout from day-to-day cloud misconfigurations, weak credentials, and lack of authentication. Another report mentioned that roughly 23% of cloud incidents result from misconfiguration, and over 80% of those stem from human error. The percentage might be a temporary sigh of relief, but even a small oversight in AWS, Azure, or GCP settings can turn an organization’s cloud into a data leak waiting to happen. And, the impact? We cannot just keep waiting to witness that!
Table of Contents
Common Cloud Misconfigurations That Leak PII
Lending platforms use myriad cloud services like object storage, databases, serverless APIs, ML pipelines, etc, each with configuration risks. Many incidents proved that public storage buckets and blobs are frequent culprits. If we take an example, open AWS S3 buckets and Azure Blob containers used to store loan applications and KYC documents. Misconfigured permissions or missing “block public access” settings can expose these buckets to anyone on the Internet.
IAM and access controls are another pain point. Overly broad roles, wildcard (“*”) principals, or hard-coded credentials can grant unintended privileges. Without strict least-privilege policies and multi-factor authentication, a hacker exploiting a compromised or weak credential can roam freely through the cloud environment.
Equally dangerous is the lack of encryption. Not only at rest but in transit as well. If sensitive records like bank statements, IDs, credit reports are stored unencrypted, any leak instantly compromises PII.
Furthermore, many teams neglect logging and monitoring. Without CloudTrail or Azure Monitor enabled for data-access events, misconfiguration incidents can go undetected for months, multiplying impact.
If we talk about practical implementation, common misconfiguration issues reported in cloud environments include –
- Mis-set IAM permissions
- Exposed API keys
- Absence of security monitoring.
Book Your Free Cybersecurity Consultation Today!
Cloud Security Posture Management (CSPM) for Lending Platforms
A modern Cloud Security Posture Management (CSPM) solution is often recommended. As Kratikal highlights, CSPM “CSPM proactively detects risks, enforces compliance, and strengthens security to prevent costly incidents” across AWS, Azure, GCP.
Here’s how CSPM helps –
Real-Time Monitoring & Visibility
Identifies security risks and provides recommendations for securing your cloud environment.
Misconfiguration Detection & Remediation
Identifies and corrects cloud security misconfigurations before they become vulnerabilities.
Compliance & Risk Management
Periodic compliance checks, ensuring your cloud meets security standards and passes audits effortlessly.
Identity & Access Management (IAM)
Safeguards sensitive data with encryption, access controls, and advanced threat prevention.
Data Security & Protection
Protects sensitive cloud data through encryption, access controls, and continuous risk monitoring.
Threat Detection & Incident Response
Detects cyber threats, prioritizes high-risk vulnerabilities, and suggests responses to minimize damage.
Multi-Cloud Security & Governance
Security visibility across AWS, Azure, and Google Cloud, ensuring policy enforcement across cloud environments.
Compliance Mapping
Maps potential threats to the applicable compliance frameworks and regulatory requirements.
Real-World Cloud Misconfiguration Cases That Leaked PII
Each of these cases highlighted below involves either an object storage bucket or a database set publicly accessible or inadequately protected on AWS, Azure or GCP. In every instance, PII like IDs, financial statements, KYC docs, and contact info were leaked because of simple misconfigurations, not any sophisticated hacking the world talks about.
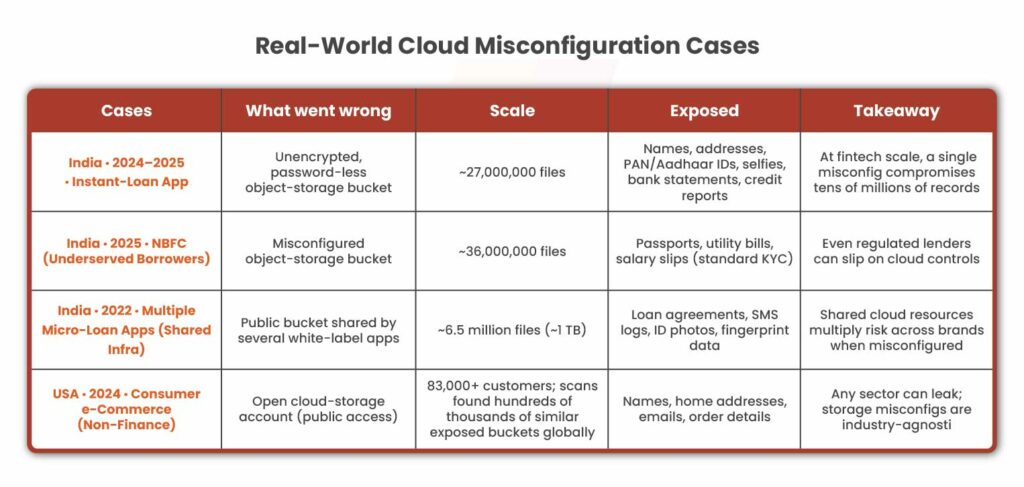
For lending/fintech organizations, the lesson is clear:
“Correct cloud configuration is as critical as any firewall or VPN.“
Regulatory and Privacy Implications If You Leak PII
Exposed customer PII triggers severe legal and compliance consequences worldwide.
- Under the EU’s GDPR, breaches involving personal data can incur fines up to €20 million or 4% of global turnover, whichever is higher. For example, a financial services firm leaking loan applicant data could easily hit those thresholds.
- In India, the new Digital Personal Data Protection (DPDP) Act 2023 similarly imposes huge penalties: violations such as a “breach of personal data obligations” can attract fines up to ₹250 crore (~$30 million) per incident. In fact, Indian rules explicitly classify a misconfigured cloud bucket exposing KYC PDFs as a “personal data breach”.
- Beyond regulatory fines, cloud PII leaks damage customer trust and invite class-action lawsuits. The IBM Cost of a Data Breach report notes that financial firms now face average breach costs of ~$6.08 million per incident. These costs include forensic investigation, remediation, regulatory penalties, customer notifications, and lost business.
- Publicly disclosed cloud breaches erode reputations; your customers will hesitate to apply for loans if they fear their data isn’t secure.
If we summarize the facts, for a lending platform, the combined impact of regulatory fines, legal settlements, and brand damage can far exceed the cost of implementing proper cloud controls upfront.
Mitigation Strategies and Best Practices
To harden cloud posture and prevent misconfiguration leaks, lending platforms should adopt the following practices:
Harden Identity & Access Management (IAM)
- Enforce least-privilege access and zero-trust principles.
- Use IAM roles, not static keys, and avoid wildcard permissions.
- Require multi-factor authentication (MFA) for all console and root/admin access.
- Implement IAM permission boundaries and AWS Organizations Service Control Policies or Azure Policy to centrally block risky configurations.
- Regularly audit IAM users, roles, and service principals. Remove unused accounts and credentials.
Encrypt Data in Transit and at Rest
- Ensure all sensitive data is encrypted.
- All storage, like S3 buckets, Azure blobs, GCP buckets, and databases, should have server-side encryption enabled.
- Transmit data only via HTTPS/TLS to prevent interception.
- For secrets and keys, use managed KMS/HSM services.
Enable Comprehensive Logging and Monitoring
- Turn on cloud audit logs for all data access events. I
- In AWS, use CloudTrail with S3 data events enabled and CloudWatch alarms.
- In Azure, use Monitor and Diagnostic Settings to capture Storage Access logs.
- Regularly review logs for unusual access patterns.
Use CSPM and Scanning Tools
- Deploy Cloud Security Posture Management (CSPM) or Cloud-Native Application Protection Platform (CNAPP) solutions that automatically scan and remediate misconfigurations.
- Leading tools like AutoSecT continuously inventory all cloud resources and flag deviations from best practices.
- Use built-in native controls too. AWS Config rules or Azure Policy can enforce encryption at rest, disable public access, approve security groups, etc.
Regular Security Audits and “Shift-Left” Reviews
- Integrate security checks into the development and deployment pipeline.
- Infrastructure as Code templates should be scanned for security issues before provisioning cloud resources.
- Periodically conduct cloud pentests and configuration reviews.
- Keep an up-to-date asset inventory.
- When new cloud services are added, run a risk assessment immediately.
- Frequent automated scans help catch cloud misconfigurations and other drifts.
Get in!
Join our weekly newsletter and stay updated
As a Takeaway
Lending platforms deal with highly sensitive PII like credit histories, income details, IDs, etc. This signifies the importance of zero tolerance for data leaks. The good news is that recent incidents show that most exposures are preventable as they arise from lapses in cloud configuration. Thus, for CISOs and cloud architects in financial institutions, the mandate is clear. Securing cloud security posture management is mandatory. It protects customers and avoids crippling fines of up to 4% of revenue under GDPR or ₹250 crore per breach under India’s DPDP. By treating cloud misconfiguration as a top threat and investing in IAM hardening, encryption, monitoring, and CSPM tools, finance organizations can lock down their cloud infrastructure. In a time when breach costs average several million dollars, prevention through good cloud hygiene is the most effective risk mitigation of all.
FAQs
- What cloud misconfigurations most commonly leak PII on lending platforms?
Open object storage (S3, Azure Blob, GCS), overly permissive IAM roles (wildcards, hard-coded keys), missing encryption, and disabled logging/monitoring are the top causes. Even a single public bucket or exposed API key can lead to large-scale data exposure.
- How does CSPM help prevent PII exposure across AWS, Azure, and GCP?
Cloud Security Posture Management continuously discovers assets, flags misconfigurations, enforces least-privilege and encryption policies, and can auto-remediate risky settings. It also maps controls to regulations (e.g., GDPR, India’s DPDP) and provides multi-cloud visibility for ongoing compliance.
- What are the legal and business impacts if PII is leaked from a lending platform?
Fines can be severe, up to 4% of global turnover under GDPR and up to ₹250 crore under India’s DPDP, alongside breach response costs, customer notifications, and lawsuits. Reputational damage and loss of borrower trust can exceed the direct penalties, making proactive cloud posture essential.









Leave a comment
Your email address will not be published. Required fields are marked *