Let’s talk about a scenario in detail about the importance of zero false positives! In a mid-sized SaaS company, the security and DevOps teams worked in sync to support rapid deployments across multiple client environments. To ensure code security, they integrated a basic vulnerability scanner. Initially, this seemed like a solid step. However, within weeks, the tool began flagging hundreds of vulnerabilities per release cycle, most of which were false positives. For every build, developers had to sift through long lists of “critical” alerts that turned out to be non-issues like outdated but unused libraries, misinterpreted configurations, or internal tools misclassified as external threats. This constant mis-sorting took a toll. Developers spent valuable time investigating fake threats instead of shipping features. Security teams were overwhelmed verifying noise, and eventually, both teams grew desensitized to alerts.
The tipping point came when a real vulnerability, a leaked database credential, was buried among 300+ low-quality alerts. It wasn’t caught in time, leading to a data exposure that damaged the company’s credibility with clients. What became clear was this: false positives weren’t just a blockage, they actively prevented the team from catching real issues. If we analyse the scenario, the core problem wasn’t tooling, it was the lack of precision. Their security tools didn’t distinguish real threats from false alarms, leading to alert fatigue, burnout, and inefficiency across both dev and security teams. Therefore, considering how cyber threats are becoming more advanced and targeted, AI-powered scanning tools like AutoSecT, that offer zero false positives, ensure organizations that security efficiency isn’t about finding everything, it’s about finding what truly matters.
Table of Contents
What Does “Zero False Positives” Mean in Vulnerability Scanning?
When it comes to vulnerability scanning, when a scanner identifies a vulnerability that isn’t present or exploitable, it is referred to as a false positive. If we take an example, when a tool reports a software version as vulnerable even though proper patching has been done or misinterprets normal system behavior as malicious, it is said to be showing false positive results. On the contrary, zero false positives means that every vulnerability identified by the scanner is valid and requires patching, with no time wasted on inaccurate alerts. In practice, this is a very high accuracy standard, one that many vendors aim for, even if achieving zero false alarms is extremely challenging. The goal is to minimize false alerts so that security teams can trust that any flagged issue is real.
Achieving zero false positives is not just about strict rules or filtering; it requires intelligent analysis. Most of the scanners often rely on broad signatures and pattern matching, which “often misinterpret normal variations in behavior as malicious activity”, leading to many false alarms. A scanner that flags everything suspicious might catch more potential issues, but if many of those are false, it overloads analysts and diminishes trust.
As one expert aptly put it, “A tool that proudly reports ‘zero false positives’ but silently misses critical bugs is far more dangerous than one that occasionally cries wolf”. In other words, the ultimate goal is high accuracy, maximizing true positives while minimizing false positives. So that the scanner finds real issues and never cries wolf. This is exactly what AutoSecT does.
Book Your Free Cybersecurity Consultation Today!
How AutoSecT Ensures Zero False Positives?
AutoSecT is an AI-powered pentest and VMDR platform that uses GenAI technologies to ensure 100% zero false positives. AutoSecT can analyze vast amounts of data and learn complex patterns to distinguish real threats from harmless conditions. Here are some of the key approaches and features that help AutoSecT achieve zero false positives:
- Machine Learning Pattern Recognition: Instead of just checking for known threats, AutoSecT uses Agentic AI to spot real vulnerabilities more accurately. It learns from past scan results, known attacks, and system settings to understand what’s truly risky and what’s not. For example, a normal scanner might flag an open port as dangerous. But AutoSecT’s AI model could recognize that this port is safe in a protected internal network. By recognizing patterns from millions of past cases, AutoSecT avoids common false alarms and focuses on actual threats.
- Contextual Learning and Risk Analysis: One of the biggest reasons scanners report false positives is that they don’t understand context. AutoSecT uses AI to analyze the full environment around each issue, like network layout, how critical the system is, existing security controls, and how the system is configured. For example, if a vulnerability is found on a server, AutoSecT checks whether that server is protected by firewalls, isolated from the internet, or already patched. If it’s not a real risk, AutoSecT can safely ignore it. On the other hand, if that same issue is found on a critical, internet-facing system, AutoSecT flags it as high priority. And, all this is done using AI, and all vulnerabilities are AI-verified.
- Behavioral Analysis and Anomaly Detection: AutoSecT doesn’t just scan for weaknesses; it watches how your systems behave in real time. Using AI, it learns what “normal” looks like for your network, systems, and users. Then it monitors for anything unusual that might signal an attack. If a vulnerability is found, AutoSecT checks for signs of suspicious activity, like strange network scans, unexpected errors, or unusual user behavior. If everything looks normal, the issue may be low risk or a false positive. But if even small changes are detected, like a spike in traffic targeting that flaw, AutoSecT knows it could be a real attack. This kind of AI-powered behavioral analysis helps cut out noise and focus on real threats. It connects vulnerability data with live system behavior, so you don’t waste time on issues that aren’t being exploited.
- Automated Validation and Proof-of-Concept Exploits: AutoSecT doesn’t just report vulnerabilities, it proves they’re real. Using AI, it can safely test whether a vulnerability can actually be exploited. This is called proof-based scanning. Here’s how it works: when AutoSecT finds a possible issue, it tries to exploit it. If the test works, AutoSecT confirms the vulnerability is real and provides proof. If it fails, the issue is dropped or marked as low priority. AI makes this smarter by selecting or even creating the right test for each system, tailoring the payload to fit the environment. It’s like having an automated pentester built into your scanner. This approach drastically cuts down false positives and gives your security team clear evidence to act on what was tested, how it worked, and what needs to be fixed.
Why Zero False Positives Matter?
As per reports, 62% of security professionals say reducing false positives is more important than finding new vulnerabilities. Here are two important reasons that highlight the importance of zero false positives:
The Cost of False Positives and Operational Inefficiencies
False positives waste time, money, and energy. Every time a scanner reports a possible vulnerability, your team must stop, investigate, check logs, and often involve developers. If it turns out to be a false alarm, all that effort is wasted. When false positives happen often, they overwhelm your team, delay real fixes, and slow down your overall security response. Analysts get stuck chasing problems that don’t exist, while real threats may go unnoticed. Each false positive can take hours to verify. Multiply that by thousands of alerts per year, and you’re spending hundreds of hours and salaries on non-issues.
The result?
Wasted resources, burnout, slower response times, and higher risk of breaches. That’s why reducing false positives isn’t just nice to have, it’s essential for strong, efficient security.
Productivity Gains and Improved Incident Response with Zero False Positives
When scanners give accurate alerts, your security team works smarter. No more wasting time debating if a threat is real; every alert is trusted and actionable. This means faster fixes, quicker incident response, and less back-and-forth between security and dev teams. Instead of sorting through noise, teams can prioritize real issues, improve security, and respond to threats faster, just like a smoke alarm that only rings when there’s real danger. When developers see that security alerts are accurate, they take them seriously. This improves collaboration and speeds up remediation. Security staff stay focused on meaningful work, fixing real problems, not chasing ghosts. That leads to higher job satisfaction and a stronger, more effective security program. With zero false positives, your team saves time, builds trust, and strengthens defenses without adding more headcount.
Get in!
Join our weekly newsletter and stay updated
AutoSecT Vs Other Vulnerability Scanning Tools
Traditional scanners rely on static rules and signature-based detection. While useful, they often trigger false positives, flagging safe systems just because they match a version or pattern. These tools don’t understand context and rarely verify issues, leaving security teams to sort out the real threats manually. This leads to alert fatigue, wasted time, and delayed fixes. AutoSecT changes that. Powered by AI, it understands your environment, learns from past scans, and even validates vulnerabilities using safe, automated tests. Where traditional scanners might return 50 vague alerts, AutoSecT reports only the real, proven ones, often with evidence.
AutoSecT Network Scanner – Built Entirely on AI
AutoSecT Network Scanner by Kratikal is RAG-powered and uses Agentic AI to scan for vulnerabilities by generating exploit codes through AI. All the vulnerabilities detected by the scanner are AI-verified, thus ensuring 100% zero false positives.
Let’s understand with an example how RAG keeps AutoSecT’s knowledge base always up-to-date.
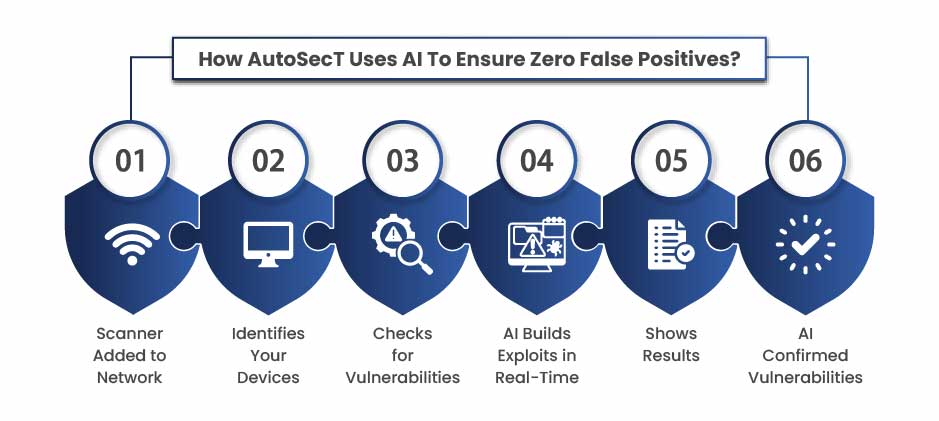
Once AutoSecT Network Vulnerability Scanner is added to your network, it starts by identifying, let’s say, your MAC devices using their addresses through fingerprinting. It then gathers information about the environment and matches it with known vulnerabilities from CVE databases. Based on this, it generates custom exploit codes tailored to your network setup and runs them to test if the vulnerabilities actually exist. After running the tests, it generates AI-verified, confirmed vulnerability reports.
The diagram below shows how it works –
In today’s threat landscape, more alerts don’t mean better protection. What organizations truly need is accuracy, alerts that are real, validated, and relevant. That’s exactly what AutoSecT delivers. By eliminating false positives through AI verification, behavioral analysis, and proof-based scanning, AutoSecT doesn’t just help you find vulnerabilities; it helps you trust what you find. For CISOs, this means fewer distractions, faster decisions, and security workflows that actually work.
In an era where missing one real threat can cost millions, AutoSecT empowers your organization to move faster and act smarter.
FAQs
- What makes AutoSecT better than traditional vulnerability scanners?
AutoSecT uses advanced AI and proof-based scanning to eliminate false positives, unlike traditional tools that rely on static rules and often misidentify safe conditions as threats.
- How does AutoSecT achieve zero false positives?
AutoSecT uses Agentic AI, contextual learning, behavior monitoring, and safe proof-of-concept exploits to confirm every vulnerability. By validating threats before reporting, it ensures your team only sees real risks, no guesswork, no noise.









Leave a comment
Your email address will not be published. Required fields are marked *