In late 2025 and early 2026, one of the world’s most advanced scientific organizations, the European Space Agency (ESA), faced a string of cyberattacks that exposed severe weaknesses in its cybersecurity posture. Hackers stole hundreds of gigabytes of data. Among the data stolen were proprietary software, credentials, and mission documents. As a final act, the hackers shared them on the dark web. The breach has shattered the illusion that elite research and space agencies are immune to modern cyber threats. This blog compiles the facts to explain exactly what happened, how the ESA security breach occurred, and why it matters.
Table of Contents
The ESA Security Breaches That Shook the Space Sector
The news may still be a lava; but, at its core, this is not a single isolated event, rather a series of attacks. Let’s deal with it in chronological order:
First Strike: 200 GB Leaked Around Christmas
Around December 26, 2025, a threat actor using the alias “888” publicly posted what they claimed was over 200 gigabytes of stolen ESA data on a darknet cybercrime forum called BreachForums. That data reportedly included source code, API tokens, access keys, credentials, configuration files, and confidential documents from systems that support engineering collaboration.
ESA acknowledged the breach, saying the compromised servers were external to its corporate network and supported “unclassified collaborative engineering activities.” They described the impact as “limited,” but the substance of the leaked material paints a more worrying picture.
Second Strike: 500 GB by Scattered Lapsus$ Hunters
Just about a week later, a separate group calling itself Scattered Lapsus$ Hunters claimed to have stolen another 500 gigabytes of data from the same organization, alleging that an unpatched vulnerability was still present and exploitable. That stash reportedly included operational procedures, mission documentation, and data from ESA contractors, including aerospace giants like SpaceX, Airbus, and Thales Alenia Space.
Together, these two incidents are said to total more than 700 gigabytes of data circulating in dark web forums.
What Was Actually Stolen in the ESA Security Breach?
This isn’t just any random junk or public-facing materials. The attackers claim to have harvested a range of internal assets that have significant operational and security value:
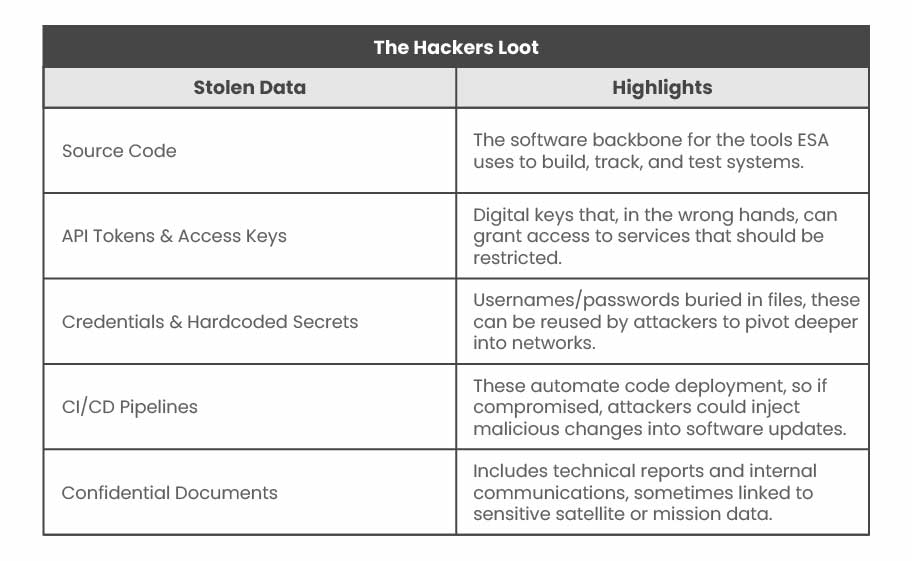
Because the breaches affected external servers, insiders argue that the term “unclassified” doesn’t mean the data was unimportant. Even seemingly mundane engineering details, when combined across multiple leaks, can reveal patterns attackers use to craft deeper intrusions.
Email Credentials on the Dark Web: A Broader Problem
Email credentials and other sensitive staff information from ESA and NASA employees are constantly traded on dark web forums. Here’s the cold truth: attackers don’t need to hit a core network directly if they have valid employee credentials that can bypass perimeters.
Cybersecurity researchers speculate that infostealer malware plays a significant role in these compromises. Once those keys are stolen from laptops or collaboration systems, they are repurposed for larger attacks. That’s not a guess; that’s the modus operandi behind countless modern breaches.
Why The ESA Security Breach Matters
On the surface, ESA has asserted that the leaked data was “unclassified.” But calling something unclassified doesn’t mean it’s harmless; it means it wasn’t officially categorized as sensitive by policy. Attackers don’t care about classification labels; they care about harmful utility.
Here’s why this is serious:
1. Reused Credentials: Meaning Lateral Movement
When password and token dumps hit the dark web, attackers can attempt those credentials across multiple platforms, including corporate mail, VPNs, cloud services, or partner networks. If any of those reuse credentials or tokens, attackers gain footholds without exploiting a network flaw.
2. Operational Visibility
Source code, CI/CD, configuration files – these expose how a system is built and deployed. That makes it easier for attackers to craft targeted malware or pivot into deeper systems.
3. Future Exploits
Attackers can combine this leak with other breaches in the future to build a bigger picture of systems and defenses, potentially enabling more destructive attacks.
4. Industry Partner Data Exposure
Data isn’t just ESA’s; contractors and collaborators like SpaceX, Airbus, and Thales Alenia Space are implicated. That extends the risk surface beyond a single organization.
The Technical Reality Space Agencies Must Face
This isn’t a simplistic “hack” where someone guessed a password and walked in. The pattern in this incident suggests:
- Compromise of external collaboration platforms
- Persistence over days or weeks
- Exfiltration of hundreds of gigabytes
- Publication on underground markets
That’s not opportunistic script-kiddie activity; that’s intentional, sustained exploitation. Modern attackers use multiple tools:
| Tools | Uses |
| Infostealer Malware | To harvest credentials |
| Token Hijacking | To access cloud assets |
| Zero-day Exploits | In third-party tools |
| Misconfigured APIs | To access controls |
So, the simple takeaway is that the attackers didn’t simply stumble onto ESA’s systems by chance. They used recognized tactics that have been publicly documented and are well understood by competent defenders. Yet these same techniques work repeatedly because many organizations, even in high-risk sectors, fail to mitigate them.
Final Take: What Should Have Been Done
Let’s be brutally honest:
ESA, like many complex organizations, is asleep most of the time at the wheel on cybersecurity.
The reality is, external servers often integrate deeply with core development infrastructure. Fragmenting “collaborative” and “core” environments does not prevent exploitation; it just creates blind spots.
If you’re an executive, CISO, or security leader reading this, ignore the gentle reassurances and focus on the facts:
- Credentials and tokens are commoditized on the darknet.
- External systems leak sensitive engineering and mission data.
- Hackers can chain these incidents into larger breaches.
Fixing this requires more than a forensic investigation; it demands a complete reassessment of how ESA manages access, monitors external systems, and secures collaboration platforms.
Until that happens, these breaches aren’t just anomalies; they’re templates for future attacks. And, 2026 has just started!
Your organization doesn’t need annual VAPT but a regular one combined with automated continuous monitoring!
FAQs
- What caused the European Space Agency (ESA) breach?
The ESA security breach was caused by exploited vulnerabilities in external collaboration systems, combined with stolen credentials, API tokens, and possible infostealer malware.
- What type of data was stolen in the ESA security breach?
Over 700 GB of data was allegedly stolen, including source code, credentials, API keys, CI/CD pipelines, and confidential mission documents. Much of this data later surfaced on dark web forums.
- Why does the ESA security breach matter to other organizations?
The breach shows that even “unclassified” data can enable lateral movement, future exploits, and supply-chain attacks. It highlights the need for continuous monitoring, credential protection, and regular vulnerability testing not annual audits.








Leave a comment
Your email address will not be published. Required fields are marked *