In order to ensure maximum security, organizations must constantly adapt to emerging vulnerabilities across complex IT environments. The threat landscape is growing at an alarming rate, and traditional vulnerability scanners are not able to keep up with the pace. This is because traditional scanners rely on static signatures and rule-based checks. This is not helpful when it comes to dealing with sophisticated attack vectors and zero-day exploits. However, with an AI-powered vulnerability scanner, organizations can leverage machine learning, behavioral analysis, and real-time threat intelligence. It can scan, detect, prioritize, and remediate security weaknesses with exceptional speed and accuracy.
Table of Contents
Why Organizations Prefer AI-Powered Vulnerability Scanner Over Traditional Scanners?
Over the years, conventional vulnerability scanners have played their part as one of the best foundational tools in the cybersecurity realm. However, as technology evolved, so did the scope of attack for hackers. The traditional vulnerability scanners lagged behind in defending organizations from these sophisticated attacks.
- Signature Dependence
Rule‑based scanners can only catch known vulnerabilities for which signatures exist, leaving blind spots for novel exploits. As traditional scanners detect only known vulnerabilities, they leave zero-day exploits and novel attack patterns undetected.
- Possibility of High False-Positive Rates
Static checks often flag benign behaviors, overwhelming security teams with noise. Rule‑based scanners often mistake harmless activity for threats, flooding security teams with false alarms and fatigue.
- Slow Adaptation
Rule-based scanners depend on human input to analyze threats, create signatures, and roll out updates. This process can take days or weeks. During this delay, attackers can exploit the gap, breaching systems before defenses catch up.
- Limited Context Awareness
Without insight into how an application functions or its role in business operations, traditional scanners may misjudge the severity of vulnerabilities. They might either be overlooking critical flaws or over-prioritizing low-risk issues. This can lead to ineffective risk management and wasted remediation efforts.
Book Your Free Cybersecurity Consultation Today!
The AI Advantage in Vulnerability Scanning
Here is why shifting to AI-powered vulnerability scanning is vital for your organization’s security:
Detection is Fast and Accurate
AI scanners train on vast datasets of code patterns, network behaviors, and historical exploits. By recognizing subtle anomalies such as unusual API calls or encrypted traffic surges, they flag vulnerabilities that rigid rule sets miss.
Contextual Prioritization
Not all vulnerabilities pose equal risk. AI‑driven tools assess exploitability, business impact, and threat intelligence feeds to rank issues. This enables security teams to focus on high‑impact flaws first, optimizing remediation efforts.
Adaptive Learning
Through continuous feedback loops where confirmed findings feed back into the model AI scanners evolve in real time. They automatically refine detection thresholds and update risk profiles without manual rule rewrites.
Behavioral Analysis
By profiling normal application and network behavior, AI systems can detect deviations that hint at advanced persistent threats (APTs), supply‑chain attacks, or insider misuse even if no known CVE exists.
How to Choose the Right AI-Powered Vulnerability Scanner?
Here are a few factors that you can consider when choosing the right AI-powered vulnerability scanner:
- Compatibility With Your IT Infrastructure: Ensure that your AI-powered vulnerability scanner supports your IT infrastructure, whether you need vulnerability scanning for specific assets or entire security coverage.
- Integration Capabilities: Works seamlessly with SIEM and supports MCP-enabled multi-integration and other tools to ensure smooth workflow integration.
- Risk-Based Prioritization: AI-Powered Vulnerability Scanner uses contextual analysis to focus on the most dangerous and high-impact vulnerabilities based on real-world context.
- Threat Intelligence Feeds: With an AI-verified vulnerability scanner, your organization can detect emerging attack vectors and live exploit campaigns by leveraging real-time threat data.
- Automation & Response: AI-powered vulnerability scanner enables faster resolution through auto-ticketing, remediation scripts, and orchestration, thus, reducing Mean Time to Respond (MTTR).
The Best AI-Powered Vulnerability Scanner – AutoSecT
AutoSecT, powered by Kratikal, is an AI-powered vulnerability scanner that provides real-time monitoring of AI-verified vulnerabilities with CVSS scores and vulnerability severity. Along with that, organizations get access to AI-powered POCs for each exploit done by all the scanners of AutoSecT. Here are the scanners that AutoSecT provides:
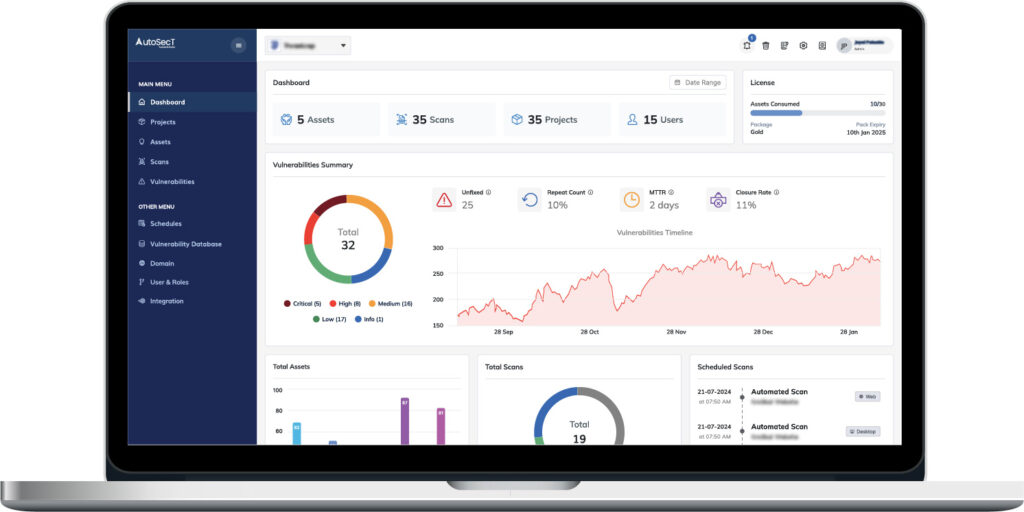
AutoSecT Network Vulnerability Scanner
AutoSecT Network Scanner is the world’s first RAG-powered, AI-agentic vulnerability scanner, delivering zero false positives and AI-verified results. It redefines network security with intelligent IP and MAC-based scanning, real-time exploit validation, and in-depth detection of misconfigurations, exposed services, and high-risk vulnerabilities.
AutoSecT Cloud Vulnerability Scanner
AutoSecT excels in Cloud Security Posture Management (CSPM) across AWS, Azure, and GCP, delivering real-time risk detection, vulnerability exposure management, and agentless asset and vulnerability discovery. It offers deep visibility, continuous monitoring, and proactive protection to secure your entire cloud environment, without added complexity.
AutoSecT Web App Vulnerability Scanner
AutoSecT’s Web Application Scanner starts with a single URL and automatically crawls all endpoints, pages, forms, scripts, and APIs. It detects vulnerabilities such as XSS, SQL injection, exposed secrets, and misconfigurations. Optimized for modern web technologies, it provides clear, actionable insights to help teams remediate issues quickly and strengthen their security posture.
AutoSecT Mobile App Vulnerability Scanner
AutoSecT’s Mobile App Security scans APK and IPA files by thoroughly analyzing every embedded package. Once uploaded, it inspects the entire app structure for exposed secrets, insecure APIs, hardcoded credentials, misconfigurations, and known vulnerabilities, ensuring comprehensive security coverage.
AutoSecT API Vulnerability Scanner
AutoSecT’s API Security scans every exposed endpoint for vulnerabilities, misconfigurations, and data exposure risks. It automatically discovers APIs, analyzes request and response patterns, and detects issues such as broken authentication, injection flaws, and insecure data handling, ensuring your APIs remain secure, compliant, and resilient against modern threats.
Get in!
Join our weekly newsletter and stay updated
By intelligently detecting, prioritizing, and providing remediating measures in real-time, the AI-powered vulnerability scanners are transforming vulnerability management into a proactive, adaptive, and strategic operation. In the digital environment, where threats evolve faster than manual processes can keep up, relying solely on traditional scanners is no longer viable. AI-powered vulnerability management is the present.
FAQs
- What is an AI-powered vulnerability scanner?
An AI-powered vulnerability scanner uses machine learning, behavioral analysis, and real-time threat intelligence to detect and prioritize security flaws more accurately than traditional rule-based scanners.
- Why should organizations switch to an AI-powered vulnerability scanner?
Organizations should switch to AI-powered vulnerability scanners because they offer faster detection, contextual prioritization, and automated remediation. They minimize alert fatigue, adapt to new threats without manual updates, and provide deeper visibility.









Leave a comment
Your email address will not be published. Required fields are marked *