The digital world is crumbling, and conventional vulnerability management alone is not enough to defend your organization against the unannounced cyber threats. Identifying the flaws present within your organizational platforms and patching them is a golden rule of protection. However, what about those vulnerabilities that interact with the broader attack surface? Thus, the need for vulnerability exposure management, especially in dynamic cloud environments, comes into play!
Table of Contents
What is Vulnerability Exposure Management?
An exposure management is an upgraded version of vulnerability management that revolves around identifying vulnerabilities, along with understanding the actual risk associated with these vulnerabilities, prioritizing them, and driving remediation efforts that reduce real-world exposure to attacks. In simpler terms:

The Future of Cybersecurity: Exposure Management + Vulnerability Management
Vulnerability Exposure Management doesn’t replace traditional vulnerability management, it enhances it. By combining the detailed technical assessment of individual risks with a broader view of real-world threats, VEM empowers organizations to expand their focus beyond isolated vulnerabilities and consider the entire attack surface, prioritize threats based on the likelihood of exploitation and the potential damage and address exposures before they become threats, reducing the chance of a successful cyberattack.
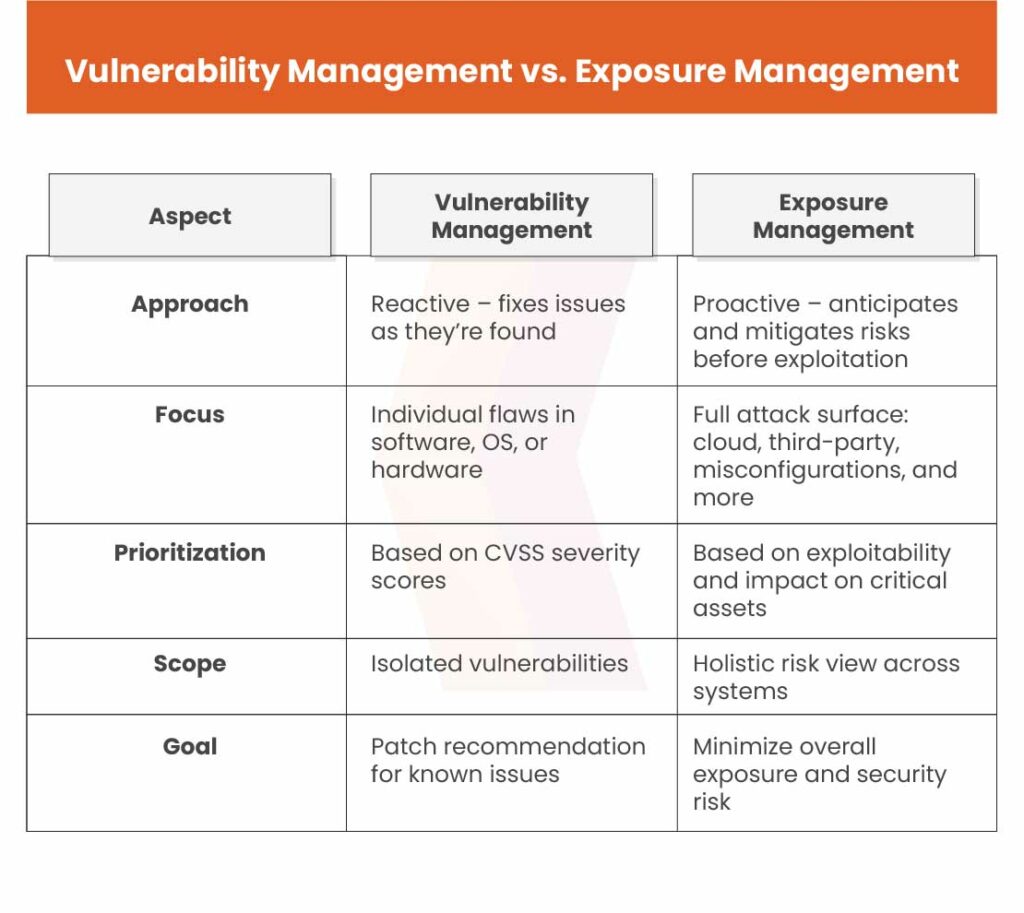
Key Aspects of Vulnerability Exposure Management
Cloud environments introduce unique security risks. They are dynamic, scalable, and often complex. These characteristics can create blind spots for traditional security tools. Common vulnerabilities in the cloud include:
- Misconfigured Identity and Access Management (IAM)
- Publicly exposed storage (S3 buckets)
- Insecure APIs and Services
- Unpatched Operating Systems or Applications
- Lack of Visibility into Ephemeral Cloud Assets
To address these issues, here are the key aspects of Vulnerability Exposure Management:
Identifying and Assessing Exposures
The first step in managing exposure to threats is knowing which platforms, apps, and cloud setups could be at risk. This means looking not just for software bugs, but also for things like services set up the wrong way, open ports, and other weak spots that hackers could use. Instead of only checking for problems inside the company’s network, Exposure Management also looks at things that are connected to the outside world, like websites, smart devices, and services from other companies. By doing this, organizations get a clearer picture of everything that could be targeted in an attack
Prioritizing Risks
Not every security issue is equally dangerous. Exposure Management means looking at how likely it is that a weakness will be used by hackers and how much damage it could cause to important organizational assets. This helps you focus on fixing the most serious problems first, like ones that could lead to stolen data, money loss, or harm to their reputation.
Validating and Testing
To make sure the security risks found are real and can actually be used by hackers, organizations use different tools and methods that help test how well current security systems are working. They show how an attacker might break in and move through the network, from the first step to full control. This testing helps find weak points and shows how ready the organization is to handle real threats.
Remediation
Once exposures are identified and validated, the next step is reducing or eliminating the risk. This could involve installing the latest security updates and fixes, reconfiguring services and systems to adhere to security best practices, ensuring that only authorized users and devices can access critical assets, and removing or replacing unsupported and vulnerable systems.
Effective remediation not only addresses immediate vulnerabilities but also strengthens the overall security posture by improving the organization’s ability to detect and respond to future threats.
Book Your Free Cybersecurity Consultation Today!
Key Capabilities of AutoSecT for Vulnerability Exposure Management
As threats become more sophisticated, cloud security requires a shift from reactive to proactive defense, and that’s where AutoSecT comes in. AutoSecT is a VMDR and Pentesting Tool that comes with vulnerability scanning features and is powered by Kratikal. The tool is equipped with features that can detect, identify, and manage vulnerabilities of four assets (web, mobile, cloud and API) in a single dashboard. Here is the key capabilities of AutoSecT for Vulnerability Exposure Management are:
Asset Discovery and Visibility
AutoSecT automatically discovers cloud assets such as containers, APIs, databases, and virtual machines. This provides full visibility into the cloud attack surface, which is essential for identifying risks in real-time.
Real-Time Vulnerability Scanning
The platform performs regular scans across cloud workloads and services to detect:
- OS-level vulnerabilities
- Outdated or unpatched software
- Misconfigurations and exposed endpoints
These scans are contextual and intelligent, avoiding the overload of generic findings and focusing on actionable threats.
Risk-Based Prioritization
Not all vulnerabilities are equal. AutoSecT for VEM uses AI-driven threat intelligence and exploitability data to prioritize issues based on severity, business impact, and exposure level. This helps security teams focus on the most pressing threats first, improving remediation efficiency.
Cloud Misconfiguration Management
AutoSecT identifies critical misconfigurations such as:
- Overly permissive IAM roles
- Publicly accessible storage
- Weak encryption and insecure protocols
It ensures compliance with security frameworks by enforcing best practices across your cloud architecture.
Threat Exposure Analysis and Response
AutoSecT identifies vulnerabilities that are actively being exploited in the wild and maps them to your cloud assets. By correlating this data with global threat trends, the platform helps teams reduce risk and respond faster to potential breaches.
Get in!
Join our weekly newsletter and stay updated
Vulnerability Exposure Management takes a smarter, more visionary approach, focusing not just on identifying weaknesses but understanding their real-world impact, prioritizing based on risk, and acting fast to reduce exposure across the entire attack surface. AutoSecT helps organizations gain full visibility into their cloud environments, identify critical misconfigurations and vulnerabilities, and respond swiftly to threats before they turn into breaches. In short, Exposure Management is the future of cybersecurity, helping teams move from simply reacting to truly staying ahead.
FAQs
- What is Vulnerability Exposure Management?
It’s a smarter way to handle security risks. Instead of just finding and fixing vulnerabilities, it helps you understand which ones are most dangerous and should be fixed first, based on real-world threats.
- How is Exposure Management different from regular vulnerability management?
Regular vulnerability management looks for flaws. Exposure Management goes further, it checks how those flaws could actually be used in an attack and helps you focus on the ones that matter most.
- How does AutoSecT help with Exposure Management?
AutoSecT gives full visibility into your cloud environment, scans for real threats, identifies misconfigurations, and prioritizes what to fix first, so you can stay one step ahead of hackers.









Leave a comment
Your email address will not be published. Required fields are marked *