
Nearly 98% of web applications face vulnerabilities that could lead to malware infections, redirects to harmful sites, and other security risks. Protecting your data is paramount to shield your business from malicious intent. Web application security testing acts as a preemptive measure, uncovering vulnerabilities before they become exploitable. This proactive approach not only sets you ahead in the market but also fosters customer confidence, enhancing your business’s reputation.
Table of Content
What is Web Application Security Testing?
Web Application security testing encompasses security testing methods aimed at identifying vulnerabilities in web applications and corporate websites. These vulnerabilities can leave websites susceptible to exploitation. As companies increasingly transit the critical business processes to the web, this leads to the website applications becoming a primary vulnerability point within organizations.
The repercussions of web application vulnerabilities include widespread credit card theft, significant reputational and financial damage to enterprises, and compromises to browsing machines accessing affected websites. To prevent such dire scenarios, web application testing ensures comprehensive security, making it indispensable for organizations. Its primary function is to detect security vulnerabilities in web-based applications.
Types of Web Application Security Testing
Securing web applications demand comprehensive testing to identify vulnerabilities. Various testing methods are employed to assess and enhance the security posture of the applications. Here are different types of web application security testing methods:
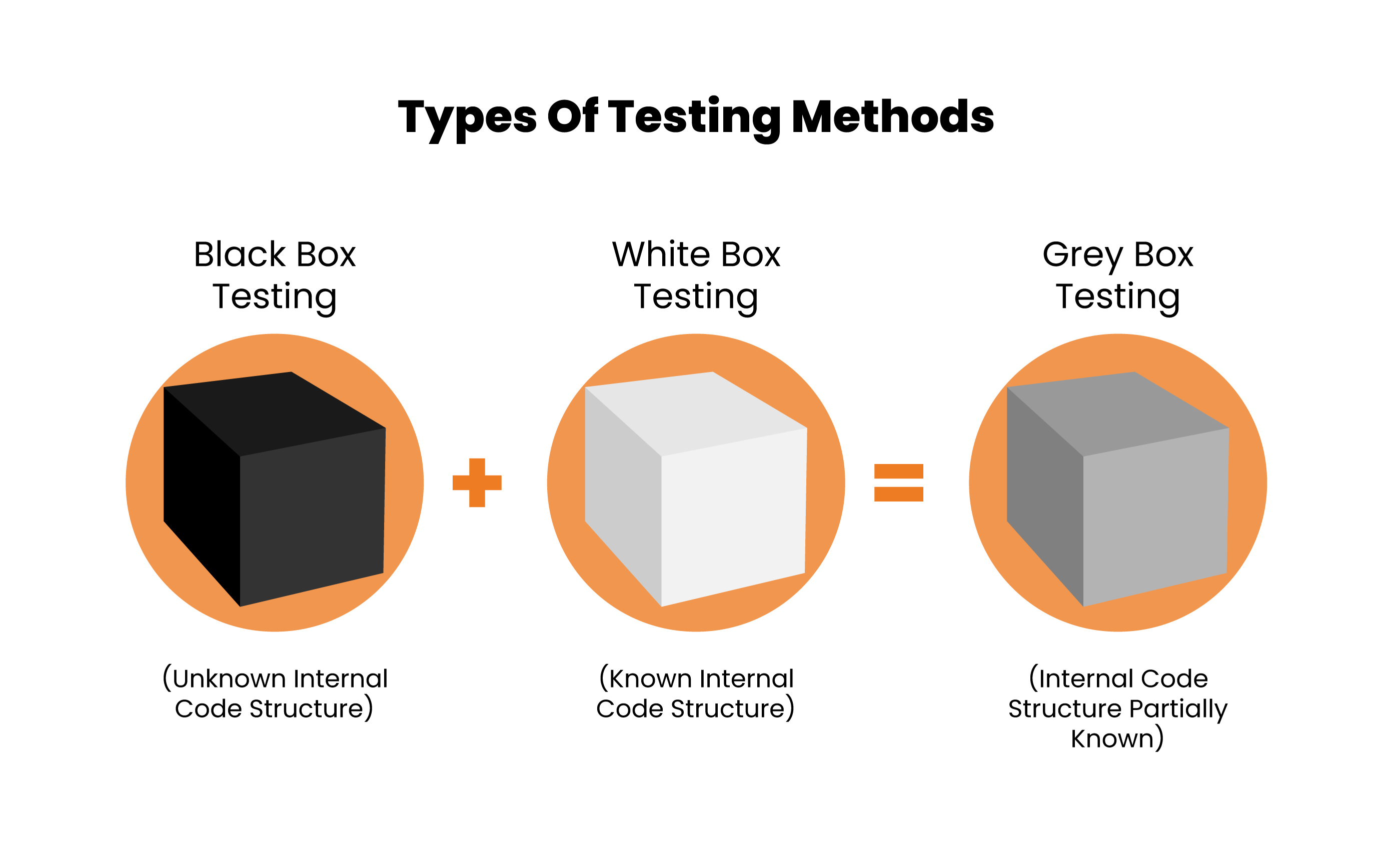
Black Box Testing:
Black Box testing, also known as external testing, is a software testing method that doesn’t require any prior knowledge of the application’s internal code, implementation details, or pathways. This approach centers on evaluating the application based on its input and output, solely relying on the software’s specifications and requirements.
Grey Box Testing:
Gray box testing is a software testing method that has elements of both black box and white box testing. It involves testing an application with a partial understanding of its internal code. The purpose is to uncover context-specific errors resulting from the application’s suboptimal code structure.
White Box Testing:
White Box testing, also known as clear box, open box, or glass box testing, involves analyzing a software’s internal structure, coding, and architecture to validate the input-output flow. It aims to enhance the application’s design, security, and utility by providing visibility into the code for testers.
What are Web Application Vulnerabilities?
Web application vulnerabilities encompass flaws within the system that attackers can exploit to compromise the application’s security. Unlike traditional flaws associated with assets or network setups, these vulnerabilities specifically arise due to the nature of web applications.
Web applications operate by interacting with various users across different networks. This constant communication and interaction make them more susceptible to exploitation by attackers. The accessibility of web applications, while advantageous for user interaction, also makes them prime targets for malicious actors seeking entry points into systems.
To mitigate these risks, continuous and thorough security testing is crucial. Regular assessments and testing help in identifying and addressing potential vulnerabilities within web applications. By proactively seeking out and fixing the flaws, organizations can bolster their defenses and better protect against potential attacks or data breaches.
Book a Free Consultation with our Cyber Security Experts

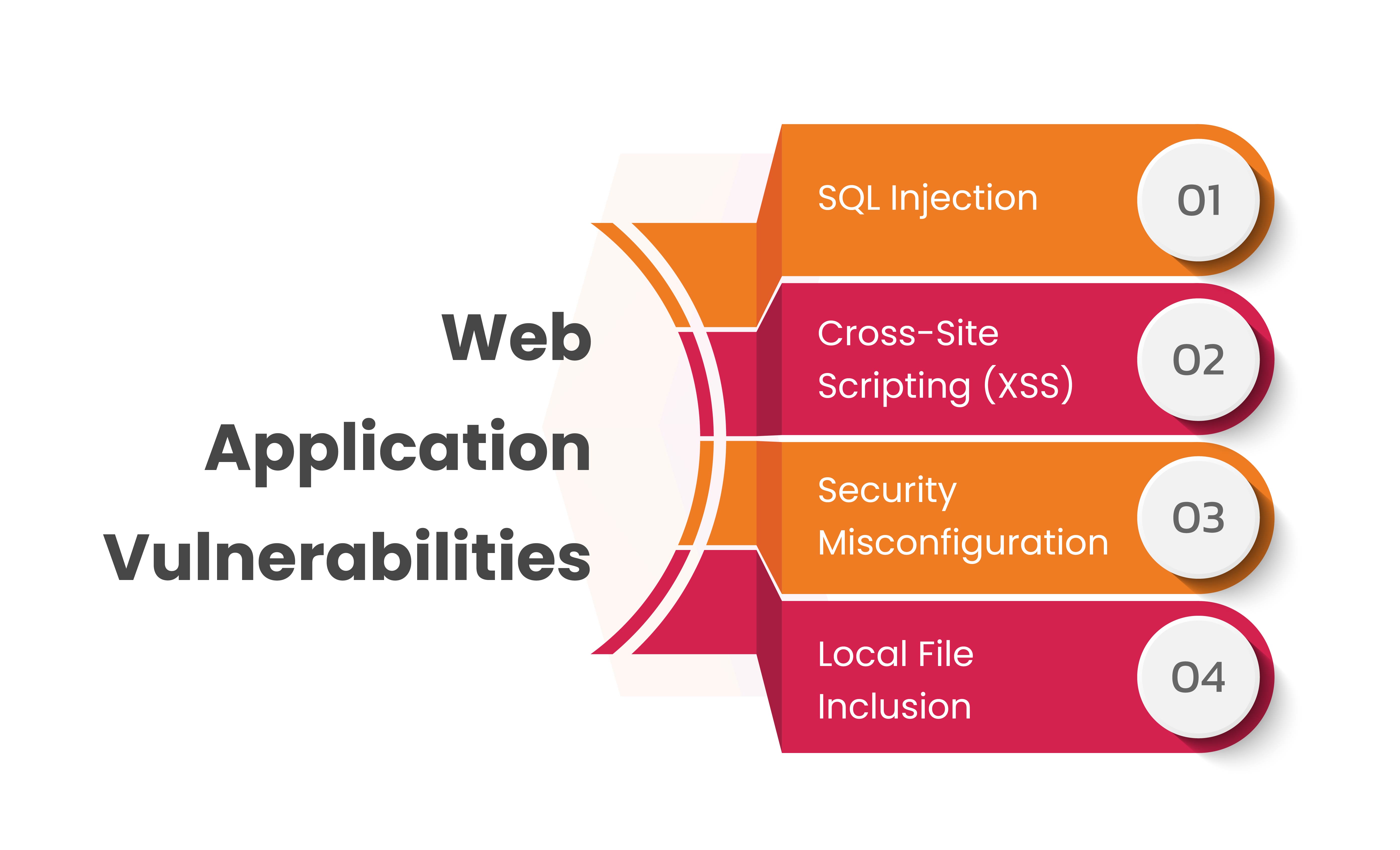
Types of Web Application Vulnerabilities
Web application vulnerabilities pose significant risks to data security and user privacy. Recognizing these vulnerabilities is pivotal for robust cybersecurity measures. Here are some critical types:
SQL Injection
Numerous applications utilize Structured Query Language (SQL) for database communication. SQL vulnerabilities enable attackers to insert harmful commands, potentially extracting, altering, or erasing data. Some exploit SQL to gain system root access.
SQL injection attacks aim at servers housing crucial data for web applications or services. They pose grave risks when exposing vital or confidential information, like user credentials. Unsanitized user inputs often create the vulnerability exploited in SQL injection attacks. Hence, removing elements from user inputs that the server could execute as SQL code is crucial.
Cross-Site Scripting:
XSS attacks are like hidden codes put in websites by hackers. They work when you visit a hacked site or app. Hackers put these codes in places like boxes where you type, and they do bad things when people open the page.
These attacks can show the information without the person knowing. They can take important stuff from the messed-up app, and you might not even notice it happening.
Security Misconfigurations:
Security misconfigurations represent significant flaws in web applications, creating accessible entry points for attackers. These vulnerabilities encompass a spectrum of issues, including default settings that remain unchanged, data stored in cloud environments, incomplete or haphazard configurations, error messages that inadvertently reveal sensitive information, and misconfigurations within HTTP headers.
What makes these misconfigurations particularly precarious is their potential presence across various components within a system. They can lurk within operating systems, libraries, frameworks, or specific application setups. For instance, leaving default settings unchanged or overlooking incomplete configurations can inadvertently create open doors for attackers to exploit. Cloud-stored data can also fall victim to misconfigurations, leaving sensitive information susceptible to unauthorized access.
Local File Inclusion:
A local file inclusion attack exploits how web applications include files dynamically. It happens when an app takes user input, like a URL or parameter, and uses it to include a file. Attackers can manipulate this to make the app include a remote file with harmful code.
Many web app frameworks use file inclusion to organize shared code into different files for use by the app’s main parts. If a web app refers to a file to include, it might run the code explicitly or by calling a specific procedure. Local file inclusion attacks can occur if the app chooses which module to load based on elements in the HTTP request.
Why is Web Application Security Testing Essential?
The evolution of web services and technology has profoundly transformed how businesses operate and how information is shared and accessed. These advancements, while beneficial, have also drawn the attention of scammers and malicious hackers who constantly seek new methods to exploit vulnerabilities for financial gain.
To counter these threats, it’s highly advisable to undergo a Web Application Security Audit. This audit rigorously examines and fortifies the defenses of internet applications and networks, aiming to identify and address potential vulnerabilities that attackers could exploit.
At its essence, a Penetration test is a simulated attack on a computer system to assess its security. When it comes to web applications, the focus shifts exclusively to Web Application Testing. This testing methodology concentrates on actively analyzing a web application to uncover technical flaws or vulnerabilities that could potentially be exploited by malicious actors.
Conclusion
As technology advances, so do the methods of those seeking to exploit vulnerabilities for their gain. From SQL injections to cross-site scripting and misconfigurations, the risks are multifaceted and ever-present. The essence of web application security testing isn’t just a precaution; it’s a proactive shield against potential threats. Through rigorous audits and vigilant assessments, organizations reinforce their defenses, ensuring robust protection for user data and business integrity. Web application testing becomes an essential strategy to strengthen defenses and encourage consideration among users in this virtual age, where information security is of utmost importance. It’s about protecting the confidence and trust of everyone who comes into contact with them, not just about locking up shipments.
Kratikal, being a CERT-In empanelled auditor, plays a vital role in strengthening web application security. Leveraging extensive VAPT experience, Kratikal conducts audits on decentralized software and smart contracts to detect and address potential vulnerabilities.
Kratikal’s proactive cybersecurity strategies and expertise in web application security testing establish its significant role in ensuring the safety of web applications. Our commitment to staying at the forefront of cybersecurity makes us the ideal choice for organizations aiming to safeguard their web application infrastructure. Kratikal empowers businesses to effectively utilize their web applications while ensuring user privacy and protecting important digital assets with confidence.
Ref: https://terranovasecurity.com/blog/cyber-security-statistics/

