Vulnerability Assessment and Penetration Testing (VAPT) services primary goal is to enhance digital security. The potential for cyber threats and vulnerabilities is constantly growing. This is where VAPT services step in, taking a proactive approach to identify vulnerabilities within an organization’s cybersecurity infrastructure. This blog will cover a range of VAPT services and their benefits. Let’s simplify this essential service and understand the layers of protection necessary to secure an organization’s assets.
Table of Content
What is VAPT Testing?
Vulnerability assessment finds security vulnerabilities by analyzing digital assets for flaws. Vulnerability assessment and penetration testing is a technique for finding security flaws in software or a computer network. Exploiting weaknesses in systems, penetration testing notifies businesses. This proactive testing method enables businesses to prioritize and install efficient security features to improve their overall cybersecurity posture. It also helps businesses understand the true scope of their security vulnerabilities.
To have a better understanding, let’s define these two terms:
Vulnerability Assessment: VAPT testing is a process used for identifying risks inside a system or network. The evaluation may be conducted either manually or through automation. During a manual assessment, a tester follows a structured procedure to identify vulnerabilities. In cases where a manual assessment is inadequate or time-intensive, an automated vulnerability assessment is used.
Penetration Testing: Ethical hacking, often referred to as penetration testing, extends beyond identifying vulnerabilities to replicate real attack scenarios. Proficient security experts attempt to exploit the detected vulnerabilities with the intent of gaining unauthorized access, extracting sensitive data, or disrupting system operations. The primary goal is to evaluate the effectiveness of existing security measures, identify potential points of entry, and recommend measures to enhance overall security.
Book a Free Consultation with our Cyber Security Experts

Benefits of Penetration Testing
- Safeguards sensitive data and information to prevent unauthorized access, theft, or data breaches.
- Adopts a systematic approach to identify significant vulnerabilities and strengthen risk management.
- VAPT testing offers an extensive assessment and evaluation of web/mobile applications as well as network infrastructure
- Regular pen testing helps organizations take steps on cyber security by identifying vulnerabilities before they can be leveraged. This approach enables businesses to promptly and efficiently resolve these concerns, ultimately reducing cyberattacks.
- Organizations need to conduct consistent security assessments, like pen testing, to comply with various regulatory frameworks and industry requirements. Meeting these standards and showcasing their commitment to safeguarding sensitive data can be achieved through the completion of VAPT.
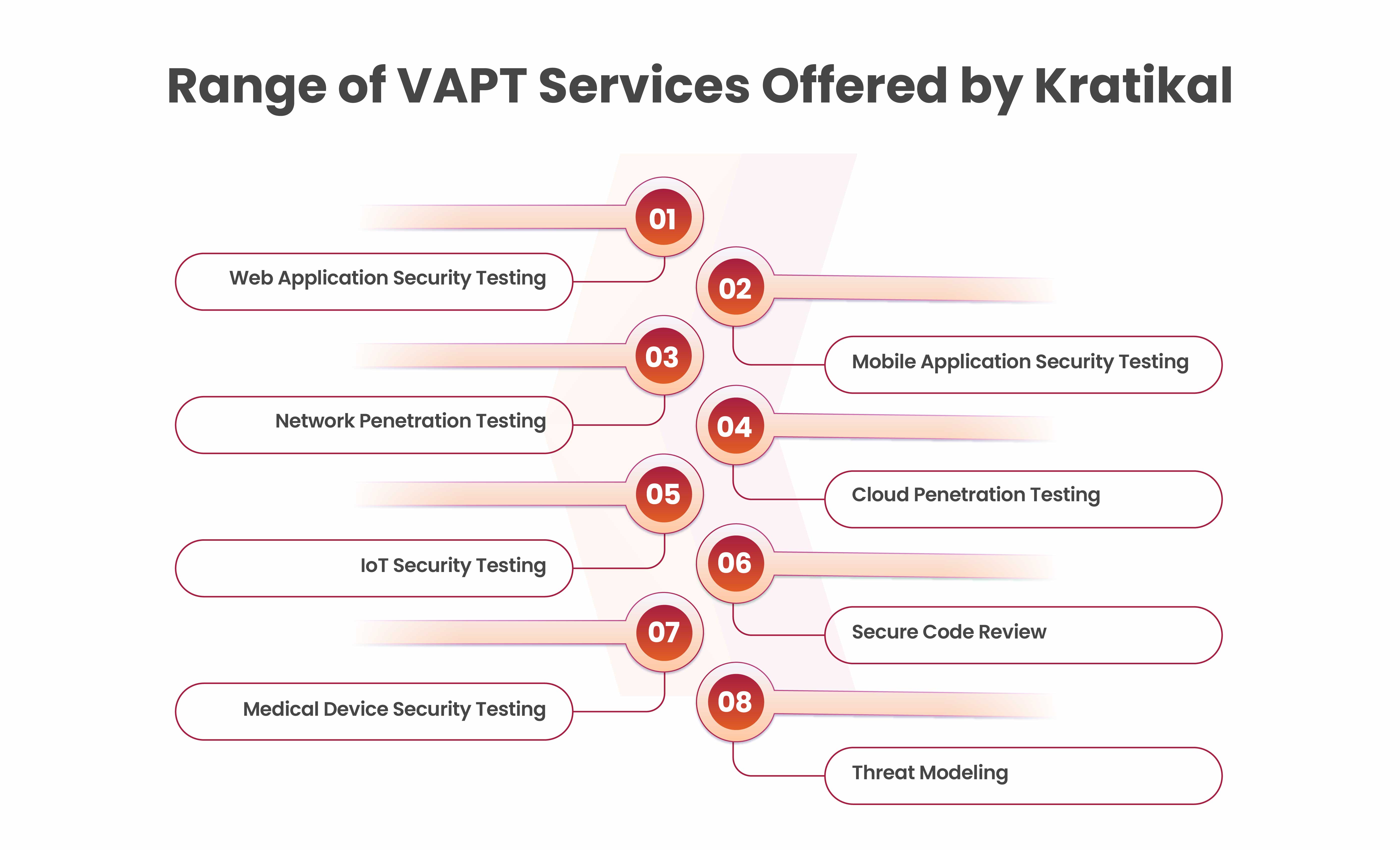
VAPT Services Offered by Kratikal
It assists in assessing the current security posture, locating specific vulnerabilities, and recommending a course of action to improve system protection. Here are the VAPT services:
- Web Application Security Testing
- Mobile Application Security Testing
- Network Penetration Testing
- Cloud Penetration Testing
- IoT Security Testing
- Secure Code Review
- Medical Device Security Testing
- Threat Modeling
Now let’s have a look at these services in detail:
Web Application Security Testing
It is the process of analyzing a hacker’s approach in a web application to identify and assess security vulnerabilities that could be exploited. Web applications are pivotal for business success and are active targets for cyber attackers. Web app testing is vital to spot vulnerabilities that might jeopardize sensitive data and finances.
Mobile Application Security Testing
Mobile application testing entails determining whether they adhere to fundamental requirements for quality, functionality, compatibility, usability, and performance. It operates on a functional Linux-based platform and is designed specifically for touchscreen mobile devices like tablets and smartphones. Mobile devices now comprise servers, data centers, community infrastructure, and the physical devices themselves in addition to serving as wireless communication equipment. In the assessment process, VAPT for mobile applications security testing holds significant importance in application security and mitigating risks related to fraud, malware, data leakage, and various security vulnerabilities.
Network Penetration Testing
A network vulnerability assessment and penetration test, commonly referred to as network VAPT, is a thorough technical security evaluation that surpasses the typical port scanning and vulnerability identification processes. Its goal is to accurately identify security risks and comprehend the potential consequences of those risks on any type of network that a business uses, including wireless, internal, and external networks. In the case of a cyberattack, network security testing is an essential method for identifying security flaws and risks that could risk an employer’s networks, web servers, and other services. It plays a crucial role in comparing the general level of protection of a community and provides insights into the condition of network protection by simulating threats and exploiting unwanted access.
Cloud Penetration Testing
The objective of this testing is to assess the cybersecurity posture of your cloud-based environment through simulated cyber attacks. It aims to identify and exploit vulnerabilities within your cloud security services. Our methodology for cloud security testing emphasizes assessing the most susceptible areas of cloud application and providing actionable recommendations for improvement. The goal of the cloud security testing results is to help the company improve its security protocols. A crucial principle for conducting cloud penetration testing is the concept of shared accountability.
IoT Security Testing
IoT security encompasses protective measures used to safeguard network-based or internet-connected devices. It pertains to the extent of technology focused on ensuring the security of networks and associated devices within the Internet of Things (IoT). In the IoT, internet connectivity is integrated into a network comprising interconnected computers, objects, living beings, and humans. An essential characteristic of an IoT device is its capability to connect to the internet and interact with its environment by collecting and sharing data.
Secure Code Review
In a secure code review, the source code of an application is methodically examined using manual or automated techniques in order to find vulnerabilities, unsafe coding techniques, backdoors, cross-site scripting problems, and other potential faults. Enhancing code security and finding vulnerabilities before they can be a threat are the main goals of a secure code review. This in-depth analysis tries to spot vulnerable code that could possibly result in flaws in the later stages of software development, eventually protecting the security of the program.
Medical Device Security Testing
Medical Device Security Testing detects potential design flaws in hardware, software, and communication methods that might jeopardize the security of the device. It helps organizations grasp the security implications of their devices and how to enhance their security posture. One aspect of security testing for medical equipment involves thoroughly examining all potential software vulnerabilities.
Threat Modeling
At Kratikal, threat modeling is a strategic practice to comprehensively analyze potential cybersecurity risks. Through meticulous evaluation and planning, threat modeling enhances the ability to proactively identify vulnerabilities and develop robust security solutions.
The goal of threat modeling is to identify possible vulnerabilities and how they can affect a computer system, application, or IT infrastructure. It involves focusing on the perspective of hackers in order to foresee the potential harm they might cause. To gain a deeper understanding of the system, the organization uses documents and a thorough analysis of the program requirements.
Why do businesses need VAPT Testing Services?
VAPT services are crucial for identifying security risks within your business’s IT system. These vulnerabilities can be exploited by malicious actors, granting unauthorized access to your company’s computer software which consequently exposes organizations to security threats and potential data breaches. Any organization that manages its own network should conduct VAPT assessments to ascertain the vulnerabilities within its systems. Failing to do so keeps these businesses perpetually at risk of cyberattacks, as they remain unaware of potential future threats. In order to ensure total protection, these organizations must assess and recognize these threats in the networks, which include devices, webpages, Internet of Things (IoT) devices, and Android applications.
Conclusion
VAPT services are crucial for enhancing cyber security and addressing cyber threats and vulnerabilities. By proactively identifying and evaluating risks in an organization’s cybersecurity infrastructure, VAPT services enable businesses to prioritize security enhancements and comprehend vulnerabilities. The combination of Vulnerability Assessment and Penetration Testing offers a systematic and proactive approach to fortifying security measures. Regular VAPT assessments are essential for safeguarding sensitive data, mitigating risks, ensuring compliance with regulations, and demonstrating a strong commitment to cybersecurity.