
According to Gartner, penetration testing will reach a $4.5 billion market by 2025 as a result of its increasing recognition. Failure to conduct routine web application penetration testing exposes vulnerabilities that adversaries can exploit, leaving your website defenseless against potential cyber attacks. Without consistent testing and analysis, potential flaws and entry points for cyber threats remain undetected, leaving the website susceptible to various attacks. Application penetration testing is the crucial shield that identifies vulnerabilities, providing an opportunity to reinforce and protect the website. Using online software testing ensures a proactive approach against any attacks, protecting not just the data but also the reliability and integrity of the digital platform overall.
In this blog, we will discuss how penetration testing can be performed in web applications and why it is important.
Table of Content
Web Application Security Threats and their Prevention
Protecting web applications involves understanding common threats and implementing effective preventive measures. Here are key pointers to address potential vulnerabilities:
Injection Attacks
A web application vulnerable to injection attacks allows unverified data from an input field without adequate sanitization. When an attacker inputs code into this field, it deceives the server into interpreting it as a system command, allowing the attacker to execute their intentions. Risks are associated with injection attacks, such as SQL injections, Cross-Site Scripting, and Email Header Injection. The misuse of administrative privileges and illegal database access could result from taking advantage of those vulnerabilities.
Preventive Measures
- Prevent commands and queries from being exposed to untrusted inputs.
- Utilize a secure Application Programming Interface (API) that uses parameterized interfaces.
- Screen and cleanse all inputs based on an approved list, effectively blocking the utilization of harmful character combinations.
Broken Authentication
Broken authentication refers to a range of vulnerabilities stemming from inadequacies in authentication and session management token handling. These flaws in implementation enable hackers to falsely claim a legitimate user’s identity, gain access to their confidential information, and potentially misuse the assigned ID privileges.
Preventive Measures
- Terminate sessions following a specific duration of inactivity.
- Disable a session ID immediately upon the session ends.
- Restrict the simplicity of passwords and implement multi-factor authentication
Insecure Direct Object Reference (IDOR)
Attackers frequently exploit URL manipulation to access database items of other users, often when the URL reveals references to database objects. This vulnerability arises when individuals can modify the URL, enabling access to sensitive information such as monthly salary slips, and bypassing the need for further authorization.
Preventive Measures
- Implement appropriate user authorization verifications at key points throughout users’ web app interactions.
- Modify error messages to avoid disclosing private user information.
- Avoid exposing object references in the URL; opt for transmitting information using POST instead of GET.
Security Misconfiguration
As per the OWASP Top 10 2017, the primary web application security threats commonly encountered stem from developers and administrators failing to alter default settings. These oversights include default passwords, usernames, reference IDs, and error messages, among others. The vulnerability arises due to the persistence of these defaults, initially set for user convenience. However, overlooking these settings makes them easily detectable and exploitable, posing substantial risks once the website is operational. The consequences span from unauthorized admin privileges to potential complete access to the database.
Preventive Measures
- Regularly upgrade every component within web applications, including firewalls, operating systems, servers, databases, extensions, and more.
- Ensure that default configurations are altered.
- Regular VAPT Testing
Why it is necessary to perform Web Pentesting?
Some organizations may question the value of web pentesting. However, in today’s risk landscape, especially with the prevalence of internet-connected applications and devices, the breadth of potential threats has significantly widened. Securing devices and applications against external attacks is crucial, but understanding and safeguarding their internal network communications are equally important. With the rise of personal devices used for business, the risk factor for organizations has increased.
A web pentesting service stands as a crucial way for organizations to validate the efficacy of their cybersecurity measures. It serves as a means for security assessors to authenticate real vulnerabilities identified in web apps during security scans. Assessing whether these vulnerabilities pose real-world risks is pivotal, and penetration testing aids in gauging their actual exploitability. Evaluating the efficacy of the current cybersecurity posture is crucial, notwithstanding the difficulty and duration of testing for internet penetration.
Web pentesting is crucial, but you should also understand that it is an evaluation of your current cybersecurity defenses. If your cybersecurity practices are lacking, penetration testing merely reaffirms existing knowledge. For optimal effectiveness, it’s essential to combine penetration testing with a range of other cybersecurity evaluation tools employed by professionals to comprehensively assess your organization’s cybersecurity landscape.
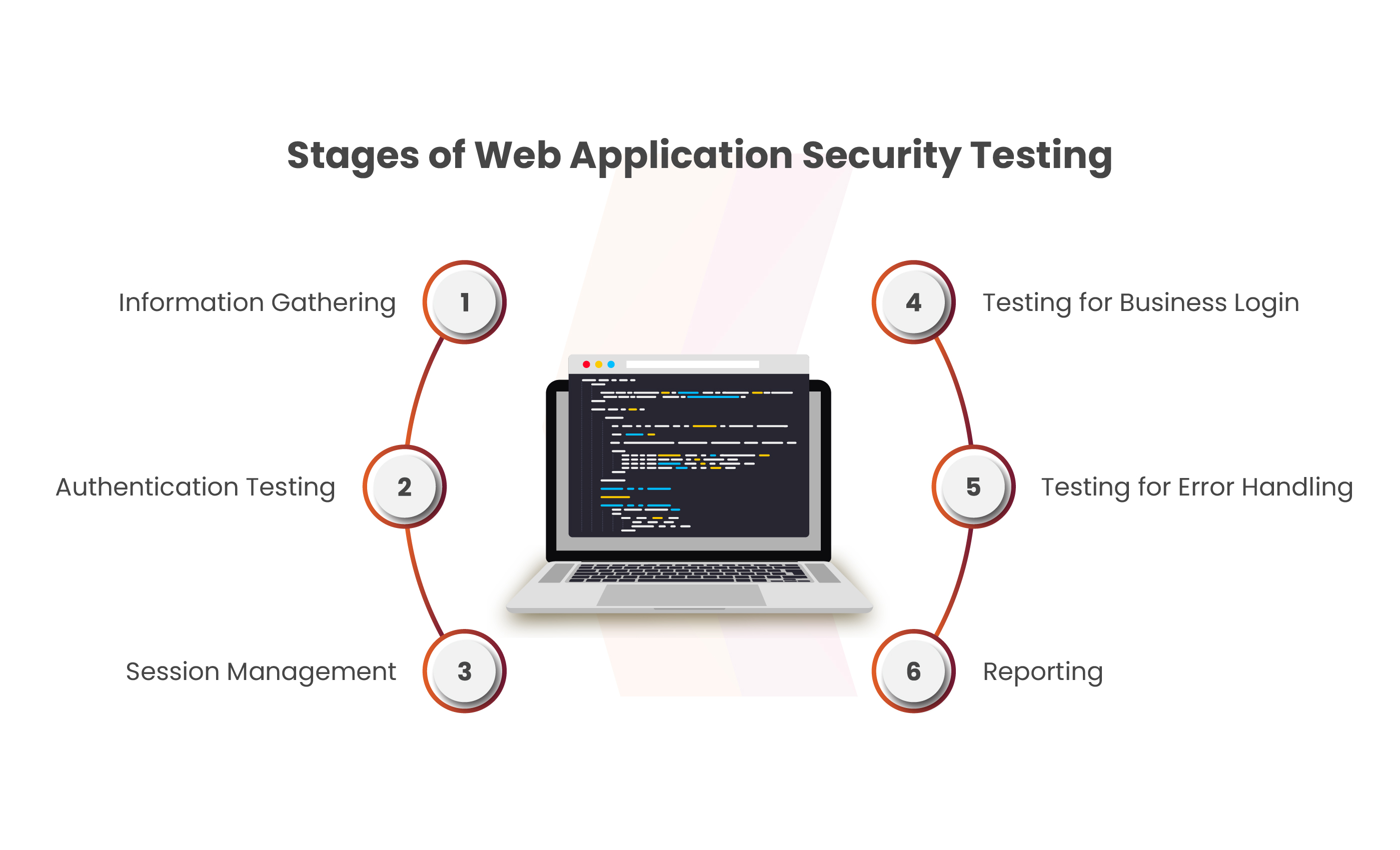
Stages of Web Application Security Testing
Web Application Security Testing encompasses various critical stages to ensure robust protection. These stages include reconnaissance, authentication, session management, vulnerability assessment, and reporting.
Information Gathering
Gathering information, known as reconnaissance, holds immense importance in web application security testing. The initial phase involves extensively understanding the target application. In numerous testing scenarios, this involves conducting search engine reconnaissance and discovery to detect information leaks, app enumeration, and app fingerprinting. The primary objective is to locate the application’s entry points.
Authentication Testing
It involves verifying the digital identity of the sender in a communication attempt. The log-on process is a common example of this validation. Evaluating the authentication system involves understanding its functionality and employing that understanding to bypass the authentication mechanism. Examples of weaknesses in this process include ineffective lockout mechanisms, circumvention of authentication methods, vulnerabilities related to browser cache, and insufficient authentication in alternate channels.
Session Management
Session management encompasses all controls responsible for managing a user’s ongoing interaction with the web application. This umbrella term includes aspects ranging from user authentication to the logout process. Some examples of these components involve session fixation, cross-site request forgery, cookie handling, session timeouts, and evaluating the logout process functionality.
Testing for Business Login
The “Think Outside the Box” vulnerability relies on the expertise and skills of a penetration tester as it evades detection by vulnerability scanners. Often, this vulnerability proves challenging to discover due to its application-specific nature, yet its exploitation can cause severe damage to the program. Examples of this vulnerability include integrity checks, process timing, unexpected file type uploads, and the ability to manipulate requests.
Testing for Error Handling
In the course of a web application penetration test, testers often encounter numerous error codes originating from applications or web based application servers. These issues can be revealed through specific requests crafted manually or generated with tools. Error codes serve as a valuable resource for penetration testers, offering extensive insights into databases, security vulnerabilities, and technological components associated with online applications. Analyzing error codes and examining stack traces exemplify some of the ways testers utilize this information.
Reporting
In the reporting phase, the key aims involve presenting, ranking, and prioritizing discoveries while delivering a concise, actionable report with accompanying data to project stakeholders. At Kratikal, we emphasize the utmost importance of this stage, ensuring thorough communication of the significance of our findings and services.
Conclusion
Web application security against cyber attacks is a multi-layered process that requires strong testing procedures and a comprehensive awareness of potential vulnerabilities. Organizations can strengthen their defenses against a variety of cyber threats by using procedures including penetration testing, authentication verification, session management scrutiny, and error-handling examinations.
Web pentesting is essential because it enables firms to find vulnerabilities and fix them before bad actors take advantage of them. Regular testing and reporting are taken proactively to ensure the efficacy of cybersecurity solutions and allow organizations to reinforce and adjust their security posture in response to evolving threats.
Kratikal is a CERT-In empanelled auditor plays a vital role in enhancing security. Our unmatched experience provides insightful analysis and robust defense against the ongoing threat of cyberattacks. Collaborating with Kratikal can proactively identify and fix security flaws, preventing the attempts of malicious hackers from exploiting them.

