
Injection, this word not only terrifies children but also, is a cause of immense worry for those who have suffered from ‘injection’ attacks. Last week, 90% of the deployed cyber-attacks were injection attacks. In an injection attack, attacker injects a malware or malicious code in a query or program. This allows the attacker to execute commands remotely that can read or manipulate a database. It can also enable the attacker to modify data that is lying on the website.
There are different forms of Injection attacks including XPath Injection, Blind XPath Injection, SSI Injection, OS Commanding, LDAP Injection, Format String Attack, Buffer Overflow, SQL Injection, Blind SQL Injection etc.
One of the most commonly deployed injection attacks is SQL injection. Considered as one of the top ten vulnerabilities, this injection attack is a code injection technique that targets data-driven applications by inserting malicious SQL statements into the entry field for execution. It was discovered in 1998 that is still being deployed by the attackers. SQL injection exploit security vulnerabilities in software of applications. This allows the attacker to manipulate, tamper, disclose or destroy data, changing the balances or voiding transactions etc.
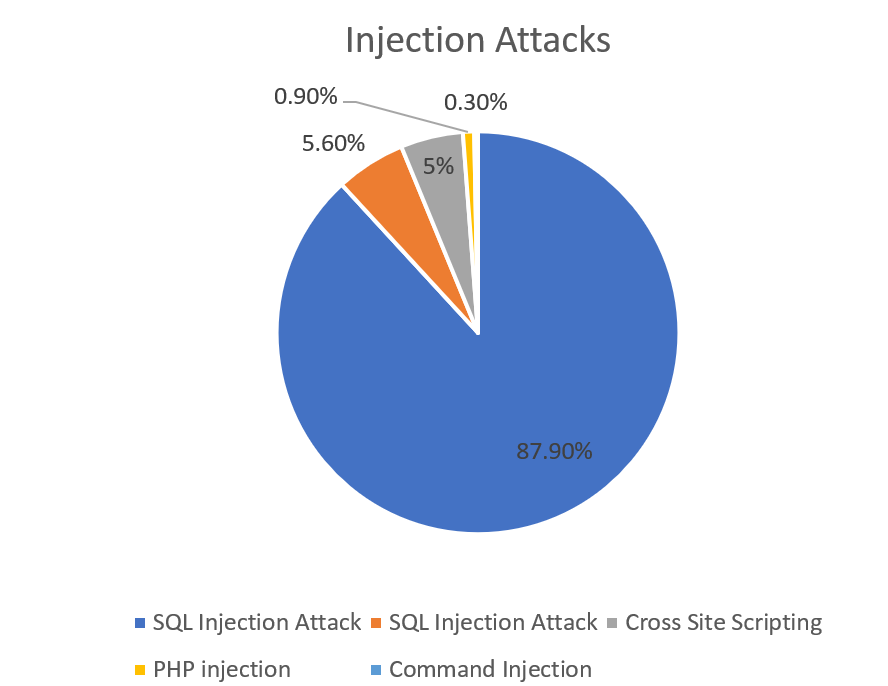
Table of Content
What is an SQL injection attack?
SQL injection attack is deployed through parts of SQL statements in the web entry field for letting the website pass a freshly formed rogue SQL command to the database. It is an attack vector for websites that can be used to attack any type of SQL database.
Why are SQL injection attacks successful?
The reason behind the success of SQL injection attacks is the weak codes. These vulnerabilities can be easily exploited by attackers for the execution of database queries thus, allowing attackers to access sensitive and confidential information, modify database entries and injecting malicious codes resulting in the compromise of the entire data. SQL injection attack can easily encrypt sensitive data. This attack can allow attackers to read information like username, passwords, card credentials. It can also allow attackers to delete the entire database.
What are the different types of SQL attacks?
SQL injection attacks can be categorized into four types. These are:
Blind based: In this form of SQL injection attack, attackers are not required to see any error message for running the attack. Even if the database error messages are disabled, attacker can still route the blind SQL injection attack. It can be further categorized into Boolean-based blind SQL injection attack and Time-based blind SQL injection attack.
Error based: This SQL injection attack is based on the error messages that are thrown by the database server for gathering information about the building of the database. Attackers can calculate an entire database.
Union based: In Union based SQL injection technique, attackers leverage the UNION SQL operator for combining the results of more than two SELECT statements. This attack helps in determining the structure of the main query with the help of blind SQL injection attack.
String based: This type of SQL injection attack takes place when the website is susceptible to SQL injection but does not show any consequences that would have otherwise shown after performing SQLi query.
How to prevent SQL injection attacks?
Sanitization and Validation: Sanitization refers to ensure that no dangerous characters are passed to an SQL query in data. Validation confirms that the data is submitted in the form in which it is expected to be.
Updating and patching vulnerabilities: It is important apply patches and updates as soon as possible in order to prevent attackers from exploiting the vulnerabilities.
Encryption is important: Hashing or encryption of passwords as well as other crucial information including connection string is important for maintaining the confidentiality of your data.
Penetration testing: Cyber security companies like Kratikal provide managed services like web application penetration testing help in preventing SQL injection attacks with input validation testing.
SQL injection has been prevailing in the world of cyber-crime since two decades and is still strongly impacting industries. It is therefore, very important to examine each vulnerability and work in the direction to patch it.

